
Identity Proofing
Give your customers a streamlined digital account opening experience, without sacrificing security. Verify identities in seconds with cloud-based ID proofing.

Meet customer and compliance requirements
Financial regulations - KYC, AML, and PSD2/Open Banking - demand high-assurance identity verification. Your customers demand flexible, digital service on their schedule. Our ID proofing provides both by supporting 6,000 government-issued identification documents from 196+ countries, as well as presenter verification and liveness test options.
STEP 1
User takes a photo of their identification
As part of your digital application process, customers use their mobile device to photograph themselves and one of the 6,000 government-issued identification documents from 196+ countries.

STEP 2
User takes a selfie
As part of your digital application process, customers use their mobile device to photograph themselves and one of 6,000 government-issued identification documents from 196+ countries.
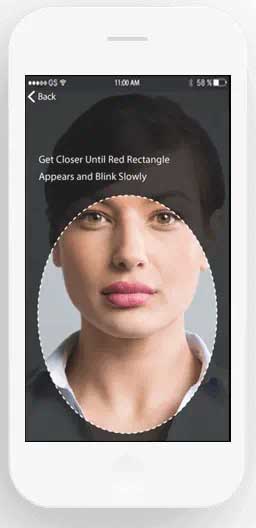
STEP 3
User's identity is verified
Within seconds, users are approved, denied, or issued a challenge based on policies and rules you establish.
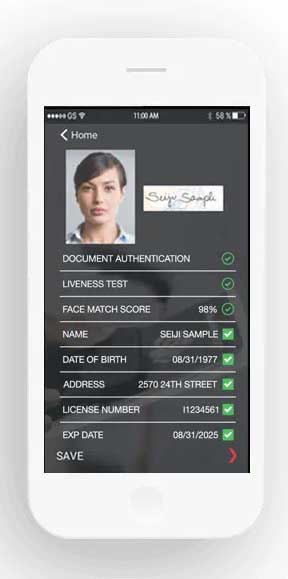
Smart, simple ID proofing
Accelerate Onboarding
Integrating ID verification into your mobile experiences enables features (like form autofill) that accelerate the application process.
Increase Customer Growth Digitally
Digital onboarding isn't just customer-preferred, it's cost-efficient at a fraction of what it costs to onboard a customer at a brick and mortar location.
Secure Verification Without a Paper Trail
Digital onboarding authenticates the customer's ID with cloud-based AI, encrypting and storing the digital ID on the customer's mobile device - nowhere else.
ID Proofing Features
Our ID proofing capability automatically supports 6,000 government-issued documents from 196+ countries, including passports, visas and driver's licenses. Integrations with Interpol and other watch-list organizations, plus advanced technologies, such as facial match verification, make it ideal for high-assurance use cases.
Secure Mobile Verification
Customers can use their mobile phone to perform secure self-service identity verification.
Integrated Authentication
ID proofing integrates with our complete portfolio of cloud-based identity access management solutions.
Mobile SDK
Our mobile SDK makes it easy to integrate our identity proofing solution into your existing mobile websites and apps.
Liveness Test Option
A liveness test is available, offering multi-layered security for higher risk transactions and customer profiles.
Device Reputation
Our service establishes trust with the device first, then the user, ensuring valid credentials aren't compromised.
Adaptive Authentication
Our adaptive authentication solution provides behind-the-scenes security so it's transparent to your end-users.
Identity Portfolio
Our identity portfolio capabilities:
Authenticate
Streamline the onboarding of diverse users and devices with a wide range of technologies.
Authorize
Ensure both strong security and exceptional user experiences with these best-in-class technologies.
Transact and Manage
Continuously protect against advanced threats with technology from behavior analytics to fraud detection.
The identity portfolio suited to your authentication needs
Consumer
Consumer Banking
Attract and retain customers with best-in-class mobile and online banking services.
Customer Portals
Give customers frictionless access to your portals — and build a great brand experience.
CIAM Integration
Our portfolio integrates seamlessly with your customer identity and access management (CIAM) strategies.
Meet PSD2 Regulations
We have the trusted identity tools you need to help you be successful and in compliance.
Workforce
Physical/Logical Access
Our portfolio offers the necessary technologies to integrate physical and logical secure access.
Privileged Worker
Protect the critical application credentials of system administrators or senior leaders.
Passwordless Login
Get a passwordless SSO solution that supports all devices, PCs and Macs, and cloud and on-premises apps.
Enable PIV Compliant Government Mobility
Remove complexity and enable highly secure mobility with proven PIV solutions.
Citizen
Digital Citizen
Use our portfolio to secure and manage passports, national IDs, and driver's licenses.
Get Entrust Identity as a Service Free for 60 Days
Explore the Identity as a Service platform that give you access to best-in-class MFA, SSO, adaptive risk-based authentication, and much more.
