
Adaptive Authentication
Adaptive authentication achieves balance between strong security and great UX by assessing contextual attributes – such as behavioral biometrics, geolocation, and device reputation – in real-time.

Get risk-based authentication that works behind the scenes
When users request access, the access context is assessed in real-time by our policy engine. And a decision is made to either grant access or challenge it. By automatically assessing each user login attempt, our technology speeds access to important data for the users who need it and are authorized to access it.
What is risk-based adaptive authentication?
Risk-based adaptive authentication considers a user's risk level when authenticating them to access a resource or system. The risk score is calculated by evaluating various factors such as location from which they are authenticating, type of device they are using, whether they are logging in from an IP address for a restricted geography, etc.

How does it work?
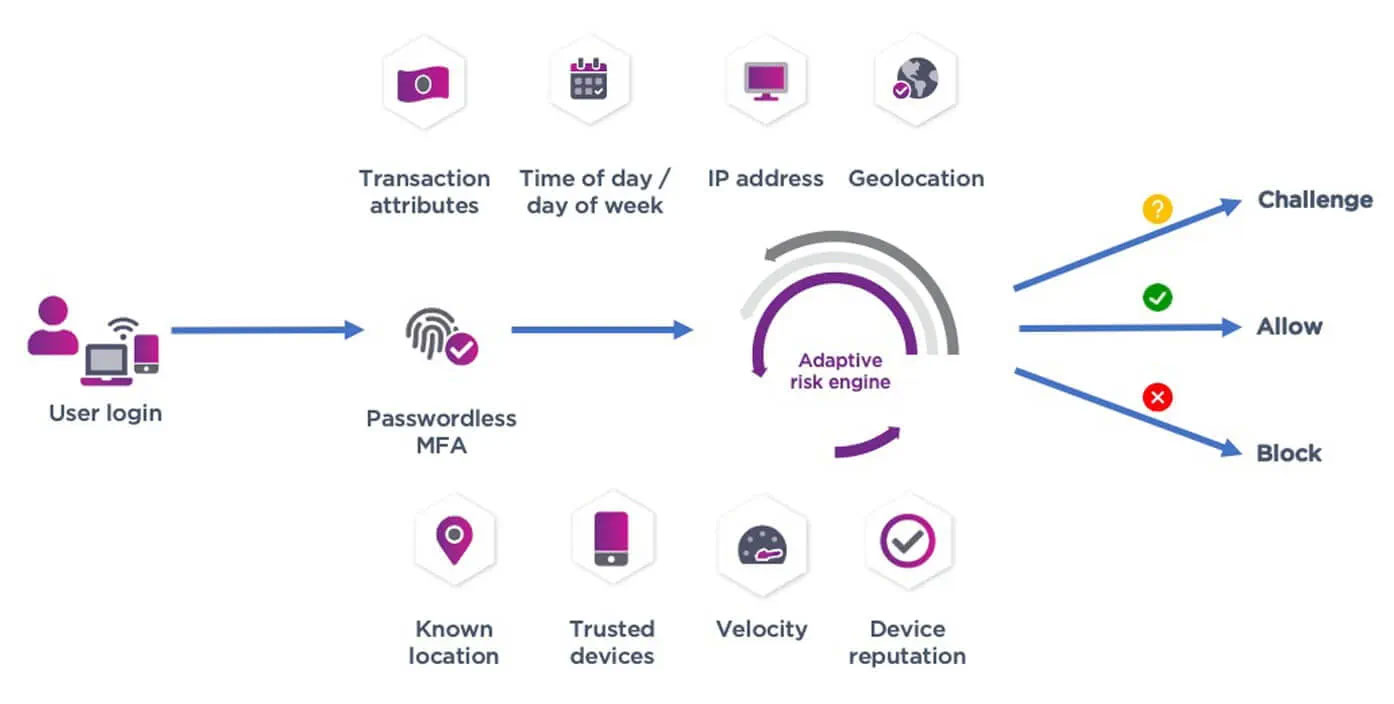
Experience the Benefits of Risk-Based Adaptive Authentication
Prevent Unauthorized Access
To systems and data by requiring additional verification steps for high-risk users or activities.
Improve the User Experience
By reducing the number of required login steps when risk is low.
Customizable
To the specific needs of an organization, allowing for a more tailored approach to security by weighting factors based on the use case.
How to Improve User Experience
Simple Management
Intuitive, risk-based policy creation, configurable user roles, and robust reporting that provides critical insights into your user security profile.
Effortless UI
Behind-the-scenes authentication enables users to effortlessly log in to workstations and applications and even open secure doors with just their phones.
Authentication Options
Provision authenticators based on user requirements and risk.
How to Configure Risk-Based Adaptive Authentication
There are several ways to configure risk-based adaptive authentication, but here is a basic overview of the process:
Step 1: Define Conditions
Define the conditions that will trigger adaptive authentication. This can be based on factors like the user's location, the type of device they are using, or the time of day. Different weights can be applied to various factors based on the use case.
Step 2: Select MFA
Select the multi-factor authenticator that will be used to verify the user's identity. This can include something they know (like a password), something they have (like a security token), or something they are (like their fingerprint).
Step 3: Configure System
Configure the system to challenge the user with the appropriate authentication factor(s) based on the conditions that are met and the risk levels that exceed a predefined threshold.
Identity Portfolio
Our identity portfolio capabilities:
Authenticate
Streamline the onboarding of diverse users and devices with a wide range of technologies.
Authorize
Ensure both strong security and exceptional user experiences with these best-in-class technologies.
Transact and Manage
Continuously protect against advanced threats with technology from behavior analytics to fraud detection.
The identity portfolio suited to your authentication needs
Consumer
Consumer Banking
Attract and retain customers with best-in-class mobile and online banking services.
Customer Portals
Give customers frictionless access to your portals — and build a great brand experience.
CIAM Integration
Our portfolio integrates seamlessly with your customer identity and access management (CIAM) strategies.
Meet PSD2 Regulations
We have the trusted identity tools you need to help you be successful and in compliance.
Workforce
Physical/Logical Access
Our portfolio offers the necessary technologies to integrate physical and logical secure access.
Privileged Worker
Protect the critical application credentials of system administrators or senior leaders.
Passwordless Login
Get a passwordless SSO solution that supports all devices, PCs and Macs, and cloud and on-premises apps.
Enable PIV Compliant Government Mobility
Remove complexity and enable highly secure mobility with proven PIV solutions.
Citizen
Digital Citizen
Use our portfolio to secure and manage passports, national IDs, and driver's licenses.
Get Entrust Identity as a Service Free for 60 Days
Explore the Identity as a Service platform that give you access to best-in-class MFA, SSO, adaptive risk-based authentication, and much more.
