
Passwordless Authentication
Enable strong identity with passwordless authentication that ensures security, manages risk, and adapts to your users.

Why passwordless
It's no secret that passwords have historically been one of the largest causes of cyberattacks. Weak passwords are easily compromised through attacks like brute force, social engineering, password spray, and more. Strong passwords increase complexity by being long and random, but that leads to them being forgotten by users – and still leaving them susceptible to attacks such as phishing.
Adopting high assurance passwordless authentication that includes proximity detection and certificate-based authentication will eliminate security threats from remote-based account takeover (ATO) attacks and improve the overall user experience.
PKI-based mobile smart credentials
Ensure security without compromising the user experience, with PKI mobile smart credential-based passwordless access that uses Bluetooth® proximity detection in the authentication process. Transform your users’ mobile devices into trusted digital identities with the installation of certificates that let them securely log in passwordlessly to their desktops and laptops using biometrics such as Face ID or Touch ID.
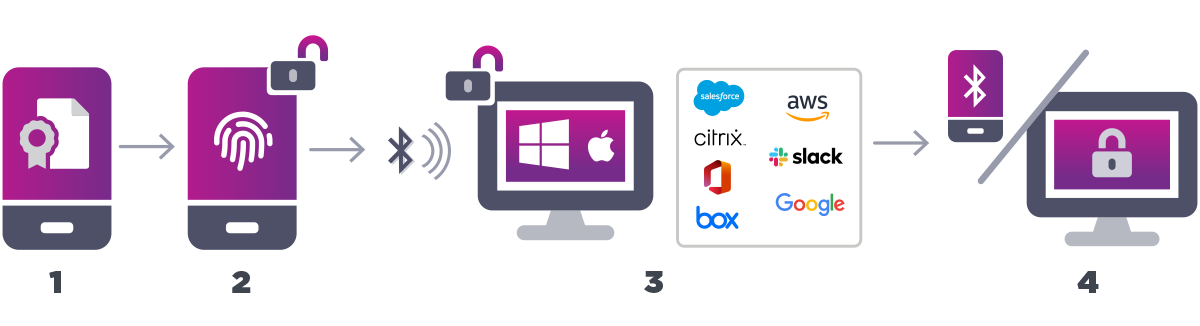
- A digital certificate is installed on the user’s mobile device, converting it into a trusted device.
- User unlocks their device and accesses their trusted identity using a biometric such as fingerprint or facial recognition.
- Once user is authenticated, Bluetooth connectivity to a Mac or PC delivers passwordless login and single sign-on (SSO) to all cloud and on-premises apps while in close proximity.
- When user walks away from their workstation with their mobile device, they’re automatically logged out of the workstation and their apps. (The proximity settings to trigger an automatic logout are customizable.)
Add support to FIDO2 with WebAuthn
WebAuthn, a core component of the FIDO (Fast Identity Online) Alliance’s FIDO2 specifications, is a web-based API that adds FIDO-based authentication support to web applications on supported browsers and platforms.
It provides a higher level of security through the use of cryptographic keys that are unique across every app, with the private key stored on the user’s device and not on a server. Users can use external authenticators such as a security key or mobile phone to log in to applications through their web browsers.

Enable passkeys with ease
Passkeys are cryptographic key pairs used to authenticate users into various applications. A public key is stored on the application server and a private key is stored on the user’s device. Passkeys use Bluetooth to communicate between the user’s phone (FIDO authenticator) and the device from which the user is trying to authenticate. Bluetooth requires physical proximity, providing a phishing-resistant way to leverage the user’s phone during authentication.
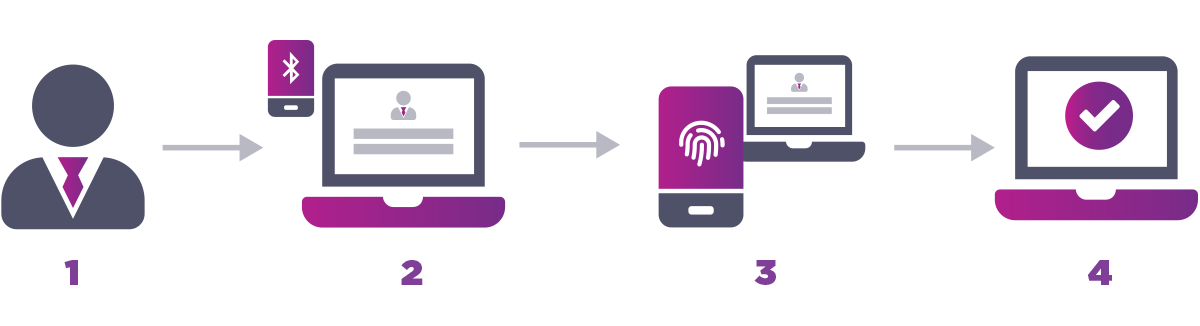
- User initiates login.
- Application issues security challenge to registered smart device in proximity (confirmed via Bluetooth).
- User uses biometrics to authenticate passkey. Passkey on mobile is used to sign and send back challenge.
- Application verifies signed challenge using the corresponding public key stored on the server and proximity of passkey device to log in user.
Securing Your Largest Attack Vector: Identity
Learn more about common identity-based cyberattacks and how to protect your organization against them.

Passwordless multi-factor authentication (MFA)
Going passwordless doesn’t mean you need multiple authenticators for multi-factor authentication. Using a mobile-based FIDO2 key or mobile smart credential combines multiple factors such as possession (smart phone) and inherence (biometrics with Face ID/Touch ID).
Single sign-on (SSO)
With our SSO offering, your users can access all applications after authenticating once, instead of re-authenticating for every unique cloud, on-prem, and legacy application they need to access.

Flexibility for every use case
With multiple passwordless options that include high assurance authentication – including PKI-based mobile smart credentials, biometrics, FIDO2 keys and passkeys, secure mobile push with mutual authentication, soft token time-based one-time passwords, and more – you can enable a user-friendly experience and tailor the type of passwordless authenticator used based on your use case.

Benefits of passwordless login
Focused Security Expertise
Entrust is a leader in digital security with 25+ years of experience in the industry. We have been first-to-market with many solutions, including passwordless user authentication.
Reduced Total Cost of Ownership
Our passwordless authentication capabilities work with the environment you have. You’ll save on the costs of resets, administration, and support.
Flexible Deployment Options
With Entrust, you decide if you want a cloud-based or on-prem solution for high-assurance credential-based passwordless authentication.
Welcome to a passwordless world
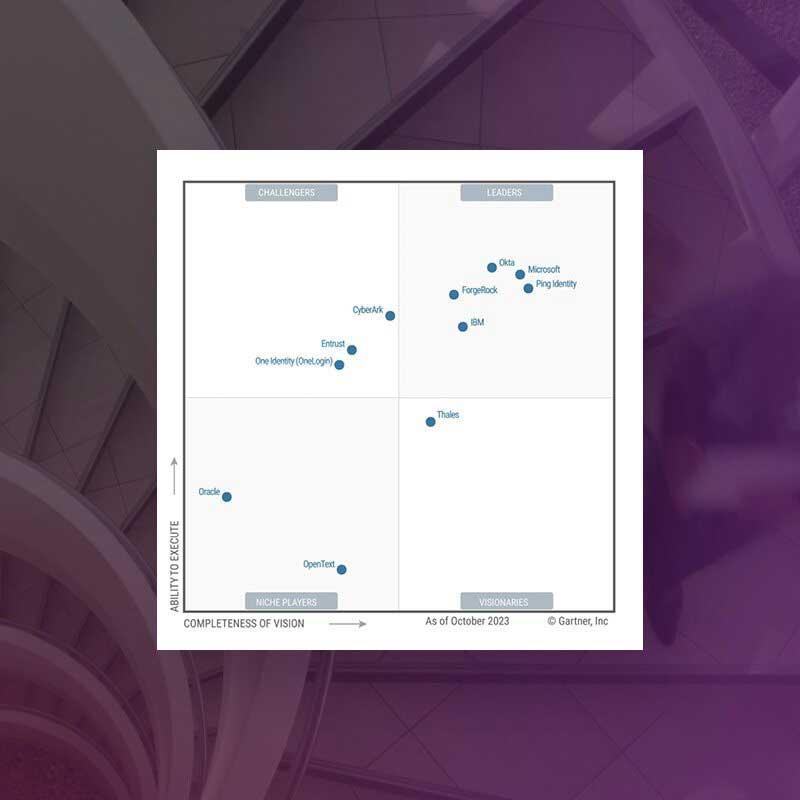
Entrust Named a Challenger for Access Management
Gartner has named Entrust a Challenger in the 2023 Gartner® Magic QuadrantTM for Access Management, recognizing our ability to execute and completeness of vision.
Identity Portfolio
Our identity portfolio capabilities:
Authenticate
Streamline the onboarding of diverse users and devices with a wide range of technologies.
Authorize
Ensure both strong security and exceptional user experiences with these best-in-class technologies.
Transact and Manage
Continuously protect against advanced threats with technology from behavior analytics to fraud detection.
The identity portfolio suited to your authentication needs
Consumer
Consumer Banking
Attract and retain customers with best-in-class mobile and online banking services.
Customer Portals
Give customers frictionless access to your portals — and build a great brand experience.
CIAM Integration
Our portfolio integrates seamlessly with your customer identity and access management (CIAM) strategies.
Meet PSD2 Regulations
We have the trusted identity tools you need to help you be successful and in compliance.
Workforce
Physical/Logical Access
Our portfolio offers the necessary technologies to integrate physical and logical secure access.
Privileged Worker
Protect the critical application credentials of system administrators or senior leaders.
Passwordless Login
Get a passwordless SSO solution that supports all devices, PCs and Macs, and cloud and on-premises apps.
Enable PIV Compliant Government Mobility
Remove complexity and enable highly secure mobility with proven PIV solutions.
Citizen
Digital Citizen
Use our portfolio to secure and manage passports, national IDs, and driver's licenses.
Get Entrust Identity as a Service Free for 60 Days
Explore the Identity as a Service platform that give you access to best-in-class MFA, SSO, adaptive risk-based authentication, and much more.
