
What is IAM? A Guide to Identity and Access Management
In this guide, we’ll help you understand all there is to know about identity and access management (IAM), why it’s important, and how you can implement the right solution for your organization’s needs.
What is IAM?
According to Gartner, identity and access management is the IT discipline that enables the right users or devices to access the right resources at the right times for the right reasons. The term “resources” refers to applications, networks, infrastructure, and data.
Moreover, IAM is a framework of policies and technologies that protect your organization from internal and external threats. In other words, IAM simplifies user access while simultaneously preventing cybersecurity incidents, such as a data breach or insider attacks.
The IAM framework aims to establish and maintain “digital identities.” In short, a digital identity is a representation of a person, organization, device, application, or other entity online. It includes attributes that are uniquely associated with said entity, thereby allowing computer systems and services to verify authenticity.
Perhaps the most basic example of digital identity would be a username and password combination. For instance, when you create an account on a website or platform, you typically choose a username (which serves as your unique identifier) and a password (which serves as a means of authentication). This combination establishes your user identity within that particular platform.
However, once established, the organization that issues the digital identity must also manage it — or in other words, ensure it’s protected from unauthorized access. Bad actors that crack user accounts can abuse their access rights, steal sensitive information, and infect infrastructure with malware, viruses, and more.
That’s why IAM solutions simplify identity management with robust monitoring controls and other safeguards, allowing them to mitigate potential threats even after initial authentication.
Use case: IAM for consumers
Many organizations use an IAM framework to verify consumers during the digital onboarding experience. For example, a bank customer may apply for a new checking account online or through a mobile app.
With an anytime-anywhere IAM system, the bank can safely confirm the applicant’s identity while providing secure access to their services — all without requiring an in-person visit. When the customer wants to access the app or their account, the system verifies the user and the trustworthiness of their device, which happens in just a matter of seconds.
Use case: IAM for workplaces
Even if some businesses are returning to the office, hybrid work is here to stay. According to a Gallup poll, just 21% of remote-capable jobs in the United States are fully on-site. That compares to 52% that are hybrid and 27% that are exclusively remote.
The point? Companies are issuing more digital identities than ever before. Between full-time employees, contractors, and consumers, managing such a high volume isn’t easy. Fortunately, IAM solutions can help.
Leading systems can provide physical/logical access to buildings, boosting security for in-person employees. Of course, they also offer secure access to virtual private networks (VPNs) and Software-as-a-Service (SaaS) applications, thereby protecting the distributed workforce. Plus, they can offer real-time control over contractor access rights, constantly monitoring user behavior for suspicious activity.
Use case: IAM for citizens
The public sector frequently uses IAM for digital citizen authentication. For instance, an IAM tool can help government agencies issue, manage, and verify passports, national IDs, and driver’s licenses. Additionally, it provides citizens secure access to essential government services and platforms, such as education, healthcare, and benefits programs.
Likewise, IAM facilitates cross-border travel through mobile identity credentials and self-service kiosks at airports. Digital citizen identities can also enable safe transactions, binding digital identities to the citizen through secure, public key infrastructure (PKI) certificates.
Why is IAM important?
Organizations have always known access control to be an essential piece of the cybersecurity puzzle. But now, given the complexity and interconnectedness of the evolving IT landscape, more are realizing that identity is a can’t-miss component.
In short, digital transformation accelerated during the COVID-19 pandemic. For some, it leapfrogged multiple years. With the rise of multi-cloud environments, artificial intelligence (AI), automation, and remote work, enterprises are providing access to more types of entities across an increasingly distributed environment. Simply put, they have more identities than they can manage.
Meanwhile, cybercriminals are evolving just as quickly. With a combination of sophisticated and AI-driven attack strategies, they’re targeting users with a swarm of phishing scams, malware, ransomware, and more. Without IAM, it’s exponentially more difficult to contain a threat because IT departments don’t have visibility over who has access to which resources. Even worse, they can’t revoke privileged access from a compromised user.
Luckily, IAM technology makes it possible to strike a balance between security and accessibility. It allows organizations to set granular access privileges to users and devices without hindering productivity or customer experience. Rather than restricting permissions across the board, an IAM tool can implement protections on an individualized basis.
IAM security and Zero Trust
IAM is a key foundation for building a Zero Trust architecture. In brief, Zero Trust is a security model that advocates for strict identity management and assumes every connection, device, and user is a potential threat. This stands in contrast to traditional security models, which are built on implicit trust.
There are three principles integral to Zero Trust security:
- Continuous authentication: Organizations must grant secure access based on numerous risk factors that are continually checked throughout a given session. In other words, they must verify entities based on identity, location, device, service, and so on.
- Limit the blast radius: Teams must always assume a data breach will occur and maximize visibility into user activity and network traffic, thereby spotting anomalies and detecting threats.
- Least privileged access: Entities should only have the necessary permission to fulfill their role or function. For example, employees shouldn’t be able to access sensitive databases if they don’t pertain to their job responsibilities.
At its core, Zero Trust emphasizes identity management. IAM, in response, provides a way to enforce its three principles at scale — and in turn, strengthen security.
Want to learn more about Zero Trust? Check out our latest solutions today.
Benefits of IAM
The right IAM tool can unlock several notable advantages:
- Compliance: Organizations must comply with data privacy regulations and contractual requirements. IAM systems allow them to enforce formal access policies and prove compliance with an audit trail of user activity.
- Productivity: Complicated security measures disrupt the user experience, which can frustrate customers and hinder employee productivity. The best IAM tools make it possible to grant secure access to multiple resources without multiple logins — a feature known as Single Sign-On (SSO).
- Data protection: IAM tools help security teams detect ongoing incidents and investigate potential risks, allowing them to eradicate threats with speed and confidence.
- IT automation: Rather than relying on manual processes, IAM automates key tasks like password resets and log analysis. This saves the IT department time and effort, enabling them to focus on more important responsibilities.
How does IAM work?
At a high level, IAM has three key components. The first two — identity management and access management — are respectively about authentication and authorization. Here’s the difference:
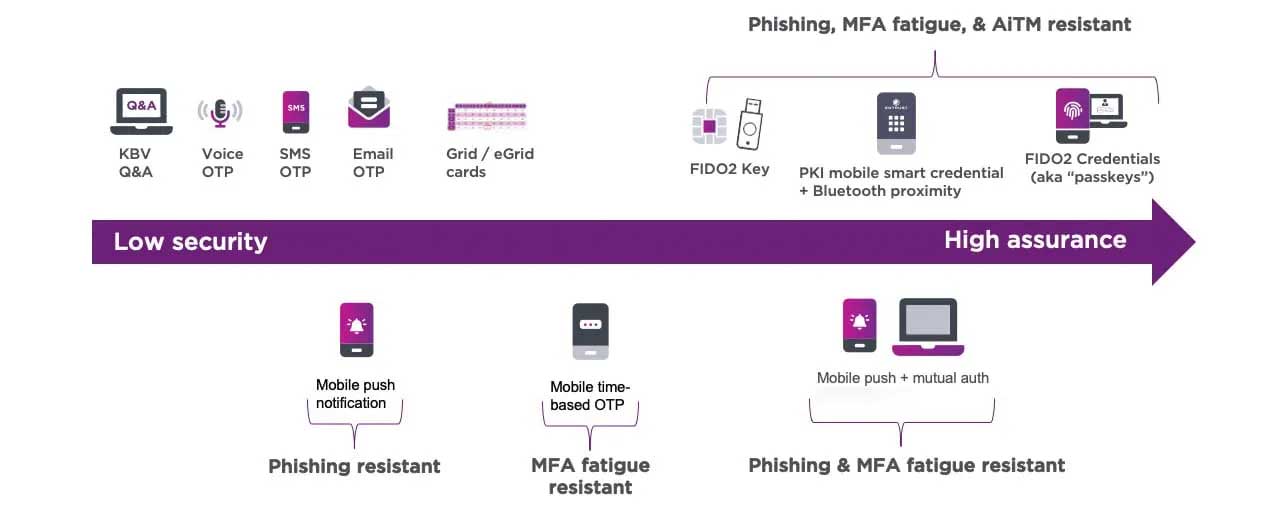
- Authentication is the process of verifying a user (or entity) is who they claim to be. Traditionally, this may involve providing a username and password, but hackers have learned to easily circumvent this method. That’s why more organizations are requiring stronger, more sophisticated techniques, like multi-factor authentication (MFA).
- Authorization is the process of verifying what specific applications, files, and data a user can access. This works by setting rules called “access control policies,” and always takes place after authentication.
Lastly, the third component is management. It involves the ongoing administration, oversight, and analysis of IAM processes, systems, and activities to ensure regulatory compliance, security, and operational efficiency. More simply, it’s the overall process of monitoring identities and access rights to spot threats and rectify vulnerabilities.
Each component relies on several essential capabilities and services. Let’s break down a few of the most notable ones in more detail:
Identity governance
IAM technologies can streamline onboarding and identity governance using the following tools:
- Authenticators: Verify digital identity using a range of methods, such as hardware tokens, digital certificates, device analysis, and one-time passcodes.
- Mobile authentication: Embed a digital identity onto a mobile device, thereby creating a smart credential that provides access to critical applications.
- ID proofing: Onboard users within seconds using biometric authentication that compares selfies to government-issued identity documents.
- Adaptive authentication: Leverage contextual analysis in real time to either grant access or challenge users with additional risk-based step-up authentication prompts.
Access control
IAM solutions make secure access possible using numerous tools, such as:
- SSO: Streamline the log-in process and allow users to leverage just one set of credentials for all their required applications.
- Passwordless login: Eliminate the risk of stolen credentials with high-assurance passwordless login. Using PKI, you can install digital certificates on the user’s mobile device, converting it into a trusted endpoint. Once authenticated, Bluetooth connectivity to a Mac or PC enables secure access to all cloud and on-premise apps in proximity.
- VPN authentication: Give users fast access to key apps and protect against credential theft using an encrypted VPN.
- Credential issuance: Allow users to request mobile smart credentials that almost instantly grant access to websites, VPNs, apps, and other essential services.
Management and monitoring
With the right solution, you can also protect against advanced threats, manage identities, and secure transactions using:
- Fraud detection: Defend customer data and your brand reputation by automatically mitigating payment fraud.
- Password reset: Cut costs and reduce help desk tickets with a self-service option for users who’ve forgotten their passwords.
- Secure device provisioning: Automate the device issuance and return process for new, existing, and outgoing employees.
IAM implementation
Implementing IAM technologies is a significant step, as it impacts nearly every user. The wrong configuration can leave gaps in your security posture, which may lead to a data breach if left unattended. That’s why it’s best to follow a few best practices when deciding on an identity provider:
1. Evaluate your IT landscape
Start by mapping your current IT environment as well as any future additions, such as cloud-based deployments already in progress. Assess your infrastructure, applications, data repositories, and other assets. This will help you identify which resources need secure access control.
Next, consider your users — employees, contractors, partners, and customers. Who needs access to which systems? This exercise ensures the scope of your IAM solution is comprehensive enough for your business requirements. Plus, it helps you enforce the principle of least privileged access.
2. Check regulatory compliance requirements
You may be subject to different data privacy laws depending on your business size, sector, and area of operation. For example, if you provide services to end users in Europe, you may be subject to the General Data Protection Regulation. Ensure your chosen identity provider meets the minimum standards as outlined by your specific legal obligations.
3. Decide on a deployment model
There are three ways to deploy an IAM system:
- On-premise: This option will require a significant investment, both in terms of upfront costs and ongoing maintenance. Although you gain more control of your IAM infrastructure, it’s often difficult to make upgrades over time.
- Cloud: By contrast, cloud-based identity-as-a-service (IDaaS) deployments are much more cost-efficient and scalable. They’re often much faster to implement and require minimal upfront configuration, as the identity provider manages the underlying infrastructure.
- Hybrid: As the best of both worlds, you can leverage both cloud and on-premise capabilities. This approach allows you to choose the most suitable model for different use cases based on your business needs.
4. Take a phased approach
Why bite off more than you can chew? Rather than rushing through the process, build your IAM foundation in pieces. A phased approach allows you to roll out various components over time, making it easier for you and your users to adjust to new processes.
5. Monitor and adapt
You can’t set and forget an IAM strategy. After implementation, pay close attention to how your solution performs. Consult with your identity provider to strategize areas of improvement — that way, you’re always protected against potential threats.
Why Entrust Identity is your ideal solution
Protecting the identities of workers, consumers, and citizens is key to preventing uncontrolled access, data breaches, and fraudulent transactions. Entrust Identity is the IAM portfolio that provides the strong foundation you need to realize a Zero Trust framework. As one unified IAM suite, Entrust Identity supports an unparalleled number of use cases and deployment options.
Take our cloud-based IDaaS platform, for example. With one solution, you can:
- Eliminate weak passwords
- Mitigate insider threats
- Detect authentication anomalies
- Reduce IT costs
- Improve reporting and compliance
- Streamline productivity
