U.S. Federal Government Data Protection
Federal government agencies and their partners protect sensitive information with Entrust nShield HSM security solutions
U.S. Federal agencies face complex data protection challenges from cybercriminals, state actors, and malicious insiders who seek to expose sensitive records found in agency databases, both on-premises and in the cloud.
Entrust nShield® hardware security modules (HSMs) and our Entrust Ready Technology Partners offer proven data protection solutions that enable Federal agencies to align with security frameworks and programs, including:
- Cybersecurity Maturity Model Certification (CMMC)
- NIST 800-53
- FedRAMP
- DHS CDM
- NSA CSfC Key Management
All our nShield HSMs are FIPS 140-2 Level 3 certified.
Entrust nShield HSMs are available to the U.S. Federal market through Carahsoft.
Contact an Entrust U.S. Federal Specialist
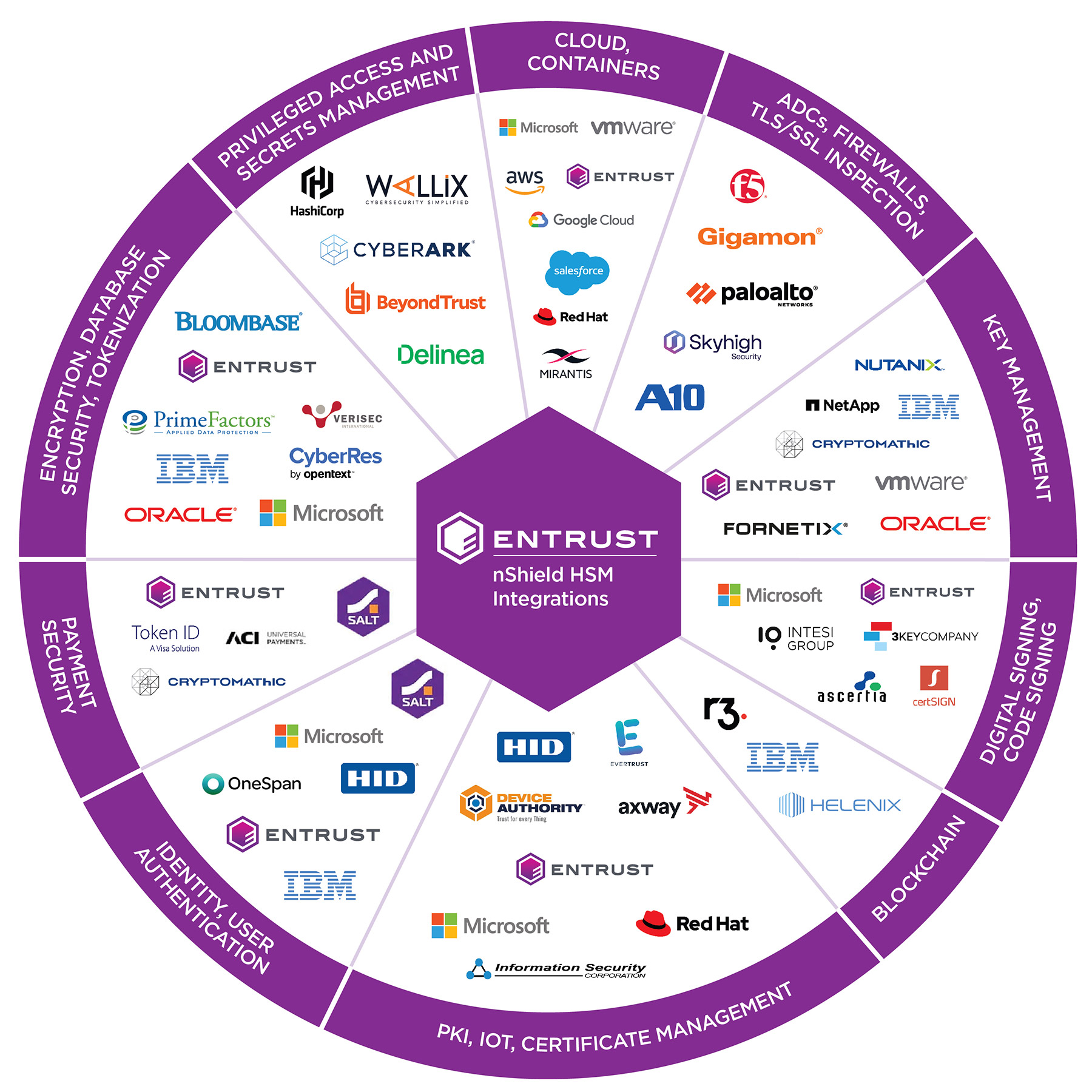
Entrust nShield HSM Partner Integrations
Click the logos below to learn more about our premier partner integrations and supported platforms.
DoD and Intelligence Agency Solutions
Nation states and other malicious actors continue to probe Department of Defense and Intelligence agencies for cybersecurity weaknesses. As articulated by Ellen Lord, former Undersecretary of Defense for Acquisition and Sustainment: "It's no secret that the U.S. is at cyber war every day.” 1
To help address today’s dynamic threat landscape Federal agencies rely on Entrust and our technology partners to help protect their mission-critical data and cryptographic material. We have decades of experience in helping agencies address a wide range of use cases and programmatic requirements, including:
- Commercial Solutions for Classified
- Public Key Infrastructur
- Robotic Process Automatio
- KMIP/Key Managemen
- Privileged Access and Secrets Management
Featured Technology Partners
Civilian Agency Solutions
Federal agencies collect and manage large volumes of sensitive data as a necessary part of their operations. This includes personally identifiable information (PII) and other mission-critical records that require high levels of protection. These large stores of data are highly attractive to cybercriminals, who seek to exploit it for financial gain.
Civilian agencies rely on Entrust and our technology partners to help protect their data and cryptographic material. We have decades of experience in helping agencies address a wide range of use cases and programmatic requirements, including
- Public Key Infrastructure
- Robotic Process Automatio
- Privileged Access and Secrets Management
- KMIP/Key Management
- Database Encryption
Featured Technology Partners
Resources
Solution brief: NSA CSfC Key Management
The NSA CSfC Key Management (KM) Requirements Annex specifies the use of approved algorithms and certificates to ensure the security of classified data in transit. Download this solution brief to learn how Entrust nShield HSMs help US government agencies meet the HSM requirements defined by the Key Management Capability Package.
Brochure: Entrust nShield HSMs Brochure
Entrust nShield HSMs provide a hardened, tamper-resistant environment for secure cryptographic processing, key generation and protection, encryption and more. Available in three FIPS 140-2 certified form factors, Entrust nShield HSMs support a variety of deployment scenarios.
Brochure: Entrust nShield HSM Professional Services
The Entrust nShield HSM professional services team offers unmatched expertise in architecting and implementing crypto applications for the world’s most security-conscious organizations. Download the catalog to learn how our team can help design and deploy the right solution for your unique environment.
Data Sheet: Code Signing Gateway
The Code Signing Gateway Service provides a range of flexible and centralized workflow automation functions that helps organizations successfully meet secure code signing requirements. The Code Signing Gateway is a customer hosted server that runs an Entrust nShield code signing application and is complemented by onsite installation and training delivered by Entrust nShield HSM professional services.
In addition to enhanced code signing key security, the Entrust nShield HSMs’ Code Signing solution offers a flexible range of automation capabilities for code signing approval processes as well as for centralized cryptographic key management. The Entrust nShield HSM Code Signing solution is unique in that it not only provides a high assurance method to protect private code signing keys in certified secure hardware, but also offers a flexible range of capabilities to simplify and automate the code signing request/approval workflow for organizations with more complex environments.
Solution brief: Bring Your Own Key | Hold Your Own Key
Entrust nShield HSMs provides the mechanisms that let you use your nShield HSMs to generate keys, secure long-term storage, and export your keys into the cloud, whether you’re using Amazon Web Services (AWS), Google Cloud Platform (GCP) or Microsoft Azure. Download the solution brief to learn more.
Related Solutions
Related Products
An Entrust Federal Government specialist will be in touch soon.