What Is A Cloud HSM?
Cloud hardware security modules (HSMs) deliver the same functionality as on-premises HSMs with the benefits of a cloud service deployment, without the need to host and maintain on premises appliances.
Cloud HSMs allow organizations to:
- Align crypto security requirements with organizational cloud strategy
- Support finance and procurement preference to shift from a CapEx to OpEx model
- Simplify budgeting for business-critical security
- Allow high-skilled security personnel to focus on other tasks
- Meet high assurance security and compliance mandates for FIPS 140-2 and Common Criteria EAL4+
What is an HSM?
Hardware security modules (HSMs) are hardened, tamper-resistant hardware devices that secure cryptographic processes by generating, protecting, and managing keys used for encrypting and decrypting data and creating digital signatures and certificates.
Click here to learn more.
Who offers Cloud HSMs?
The major public Cloud Service Providers (CSP) offer cloud HSMs as an option in their service offering. These solutions provide the convenience, resilience and flexibility you would expect from a CSP but the services are often tied to the specific public service provider and not always portable for organizations adopting multi-cloud strategies.
Like most cloud services the infrastructure is abstracted from the user so you may have a trade-off regarding ownership/residual risk with respect to the cryptographic keys and losing some of the control that you would have with an on premises HSM.
On premises HSM vendors like Entrust offer Cloud HSMs. These offer organizations the benefits of a cloud service working in unison with the CSP but with greater control of your cryptographic keys.
Entrust’s cloud HSM product is nShield as a Service. It uses dedicated FIPS 140-2 Level 3 certified nShield HSMs. The service delivers the same features and functionality as on-premises nShield HSMs, combined with the benefits of a cloud service deployment. This allows customers to fulfill their cloud first objectives and leave the maintenance of these appliances to the experts at Entrust.
Who manages an nShield Cloud HSMs?
nShield as a Service is available as either a Self-managed or Fully-managed service.
The Self-Managed service means the organization retains the full management of the HSM albeit remotely. The Fully-Managed service suits customers who want to utilize the cryptographic services of an HSM but want to delegate the management and maintenance to a Security Officer role fulfilled by trusted Entrust personnel. Figure 1 below is a modified version of the popular shared responsibility model, used to illustrate the cloud security framework identifying the responsibilities of cloud service provider and customer to highlight accountability.
Column 1 represents an on premises deployment. The HSM, HSM management layer and keys are highlighted as icons. In this scenario all of the attributes of an on premises deployment are the responsibility of the customer.
Column 2 in the model represents an Infrastructure as a Service (IaaS) deployment where nShield as a Service based on a Self-Managed deployment is the best fit. The HSM in this scenario is the responsibility of Entrust. The management of the HSM and the keys are the responsibility of the customer.
Column 3 represents a Platform as a Service (PaaS) deployment where nShield as a Service based on a Fully-Managed deployment is the best fit for the model. In this scenario the HSM and management of the HSM appliance are the responsibility of Entrust. The keys are the responsibility of the customer.
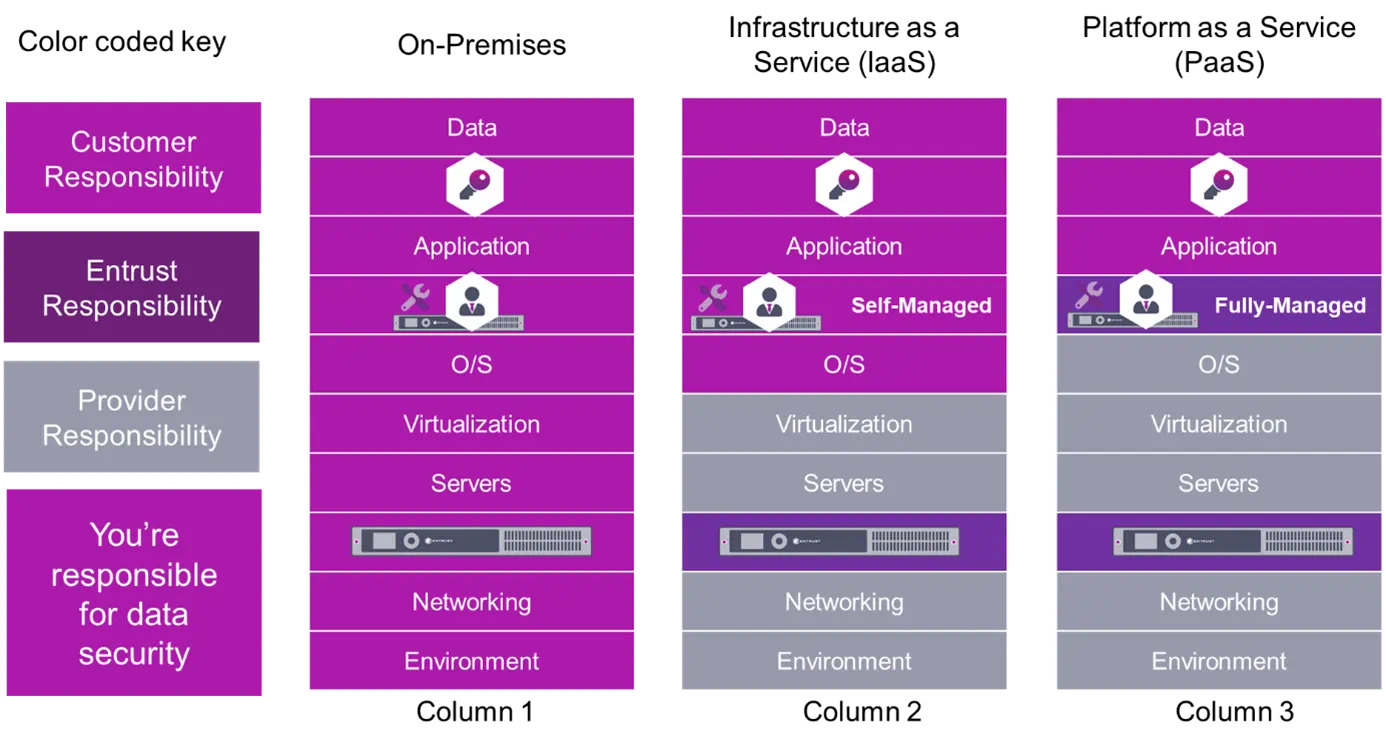
Figure 1: Modified version of the cloud shared responsibility model illustrating an on premises HSM deployment v nShield as a Service (Self-managed & Fully Managed) deployments
Are Cloud HSMs as secure as on premises HSMs?
The Cloud Service Provider has responsibility of the cloud, the Customer has responsibility in the cloud.
The cloud offers organizations many benefits in terms of flexibility, scalability and convenience. When migrating applications and workloads to the cloud the security envelope has changed. The CSPs quite rightly assert that security in the cloud is not necessarily weaker than on-premises, it’s just different. In essence the threat model has changed, the residual risks have changed. With on-premises the risks are perhaps easier to identify – usually a data center with racks of physical appliances, perimeter security considerations, physical attacks, disgruntled employees, theft, disruption to utilities etc. as well as the raft of network security considerations, firewall, malware, DDOS etc.
With the cloud service providers’, they have the responsibility for the security of their server farms, network infrastructure et al. However different threats are now at play and given the appliances are abstracted from the customer it is the controls and procedures adopted by the customer that in part informs the security of a customers’ workloads in the cloud. In fact, to date the majority of successful attacks in public cloud are due to customer misconfiguration, mistakes and mismanagement. So that’s users of the services, not the cloud service providers at fault. The cloud shared responsibility model discussed above is a useful reference to encourage customers migrating to the cloud to recognize the ownership and responsibilities when utilizing cloud based service.
What is a multi-cloud strategy?
A multi-cloud strategy is where organizations choose to utilize the services of multiple CSPs. This strategy can be informed by different CSPs offering different services but also has the added value of sharing the workload and risk/resilience across multiple organizations.
CSPs provide the tools required to create cryptographic keys that you use with your application and data. However, as you would expect these tools are not the same for different CSPs. nShield as a Service can help solve that problem. Using nShield as a Service to provision your cryptographic keys you only need to be familiar using the nShield tool set applying the same procedures per CSP.
What is a hybrid cloud strategy?
A hybrid strategy is when an organization chooses to retain an on premises presence and in addition utilize the cloud to provide extra capacity, resilience and scalability. In some cases organizations may choose or be mandated to retain high value, sensitive workloads on premises, so called data localization, and use the cloud for less sensitive workloads. nShield as a Service works seamlessly with on premises nShield HSMs supporting hybrid cloud strategies.
What is the difference between a Cloud HSM and BYOK?
Bring your own key (BYOK) is an innovative concept that was initially pioneered by Entrust and Microsoft to enable public cloud users to maintain control of the cryptographic keys used in the cloud to keep their data secured. As the adoption of public cloud services exploded, BYOK is now supported across all major cloud services. BYOK enables public cloud users to generate their own high quality master key locally on-premises, and securely transfer the key to their cloud service provider (CSP) to protect their data across multi-cloud deployments.
Cloud HSM does not require an on premises HSM footprint. Cryptographic services are provisioned in the cloud while the owner retains full control of those services. Having your crypto services commissioned in the cloud gives you the maximum freedom and flexibility.
What are the typical use cases for an HSM?
HSMs including Entrust nShield as a Service can be used to provide cryptographic services for a wide variety of applications from PKI and key management, privileged access management, containerization, database encryption and code signing to name but a few. Entrust has a substantial proven ecosystem of over 100 security solution providers. See figure below.
The partner eco-system offers the following benefits:
- Delivers value and enhanced security to end customers by hardening partner solutions with certified, hardware-based cryptography
- Mature, proven processes backed by technology expertise and global coverage ensure the strongest customer support