“I went down to the crossroads,” starts many a blues song, dating back to music pioneer Robert Johnson, who, legend has it, sold his soul to the devil for the secret of the blues.
Sometimes it feels like data protection is at a crossroads – with IT leaders standing at the intersection between security and compliance. Does it have to be fateful choice? Or, is the real secret that compliance can be considered as a form of security?
Compliance in data protection typically refers to mandatory regulations designed to ensure sensitive digital assets are protected against loss, theft and misuse. Examples might include medical records, financial details and personally identifiable information (PII) such as name, social security number, email address and date of birth.
Most regulations require organizations to implement best practice policies and procedures while protecting data and customers. They can be in play for specific industries., by state or federal law, for specific countries or an economic community such as the European Union. You may be familiar with the European Union’s General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS) which protects payment card holder’s details; the California Consumer Privacy Act (CCPA) of 2020; or the Federal Information Security Management Act (FISMA) of 2002, which requires federal agencies to develop, document, and implement information security and protection programs. However, compliance doesn’t equal security. While data compliance refers to mandatory regulations on what must be protected, data security relates how to protect this information – processes, procedures and technologies that define how your organization looks after sensitive data and guards against data breaches.
Encryption is the standard way to protect data and render it unreadable and unusable in the event of a breach. The 2021 Global Encryption Trends Study by the Ponemon Institute and commissioned by Entrust identifies what IT professionals see as the most salient threats to their organizations:
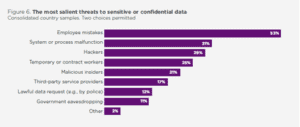
Employee mistakes were considered the most salient threat, significantly outweighing concerns over malicious attacks by temporary or contract workers. This is perhaps a reflection of the pressures that come to bear on IT staff with too many plates spinning, dealing with myriad processes and procedures, user interfaces and tools. Let’s face it, these staff are in high-pressure roles where innocent actions can lead to data being unencrypted, unprotected and exposed to breach.
Encryption requires cryptographic keys to encrypt and decrypt the workload. These keys are often thought of as an organization’s crown jewels. Which is why we have seen data compliance regulations start to call out the importance of cryptographic key management – from creation to retirement.
As an industry leader in establishing secure connections Entrust has a complete portfolio of solutions to help not just with the key management but also with the encryption of workloads. Because compliance is just the baseline. Organizations need to look to data security standards and best practices to protect customers, partners, employees and their own businesses, while enabling secure interactions.
Customers can deploy Entrust KeyControl to simplify management of encrypted workloads such as virtual machines (e.g., VMware vSphere) and storage by automating the encryption key lifecycle – including key rollover, audit logging and more — which facilitate compliance. Under the hood, it utilises a Key Management Server (KMS) to handle provisioning of keys to encrypted workloads – and helping to avoid the risk of human error. KeyControl integrates with Entrust nShield HSMs, certified to FIPS 140-2 Level 3 and Common Criteria security standards for cryptographic key generation, protection and a strong source of entropy for creating the crypto keys.
Another area to combine data compliance and security is in multi-cloud environments. Entrust DataControl provides agent-based encryption of virtual machine workloads in multi-cloud environments, using robust policy-based access controls to enforce separation of duties across different user personas. This means certain tasks can only be carried out by specific members of staff – as defined in your security policy, preventing system administrators from accessing sensitive data by enforcing access controls on encrypted volumes. For hybrid cloud deployments, this prevents your cloud service providers’ administrators from accessing encrypted data.
Finally, a strong infrastructure requires a unified framework for security and compliance. Entrust CloudControl offers lowers risk and operational overhead for both on premises and cloud deployments. Security policies can be written independently of underlying infrastructure and are translated into actual controls based on workload location. Logical segmentation automatically enforces workload placement policies based on multiple attributes. In other words, CloudControl takes well-intended but error-prone employees out of the picture.
So, are we at a crossroads between security and compliance? Well-defined compliance regulations are a good thing, raising the bar in a specific industry, region or state, and ensuring customers’ and organizations are following best practice with respect to managing their data. And, both base compliance and data security best practices usually involve deploying encryption. With encryption comes responsibility – to manage your data, manage your cryptographic keys and have policies and procedures in place to which apply as your business grows. Doing whatever you can to simplify your encryption strategy, mitigate manual processes where mistakes can be made, and having a genuine focus to do encryption right is a huge step forward to protecting enterprises data against attacks, misuse, and breaches.
It’s clearer than ever that in today’s climate, compliance and security very much go hand in hand, even if the devil is very much in the details. Entrust can help you with that! Find out more about Entrust HSMs and a free trial of HyTrust KeyControl.



