
Zero Trust Solutions
Start your Zero Trust journey with phishing-resistant identities, secure connections, and secure data.
What is the Zero Trust Framework?
Organizations that adopt Zero Trust principles assume every connection, device, and user is a potential cybersecurity threat. By eliminating implicit trust, the Zero Trust model advocates for a security policy in which nobody is inherently deemed safe, regardless of role or responsibility.
Taking a Zero Trust approach allows you to enhance data security without compromising user experience. And, with Entrust’s suite of authentication and secure access solutions, you can safeguard sensitive data from unauthorized access and exposure.

Explore Zero Trust Solutions
Entrust uniquely helps organizations establish a strong Zero Trust framework with a comprehensive portfolio of Zero Trust security solutions that helps secure identities, devices, applications, networks, and data.
Phishing-Resistant Identities
Enable high assurance identities with phishing-resistant MFA to protect against remote-based account takeover (ATO) attacks.
Secure Connections
Establish strong identity, end-to-end encryption, and access control to micro-segmented networks.
Secure Data
Ensure confidentiality, integrity, and secure access to critical information while staying aligned with data security regulations.
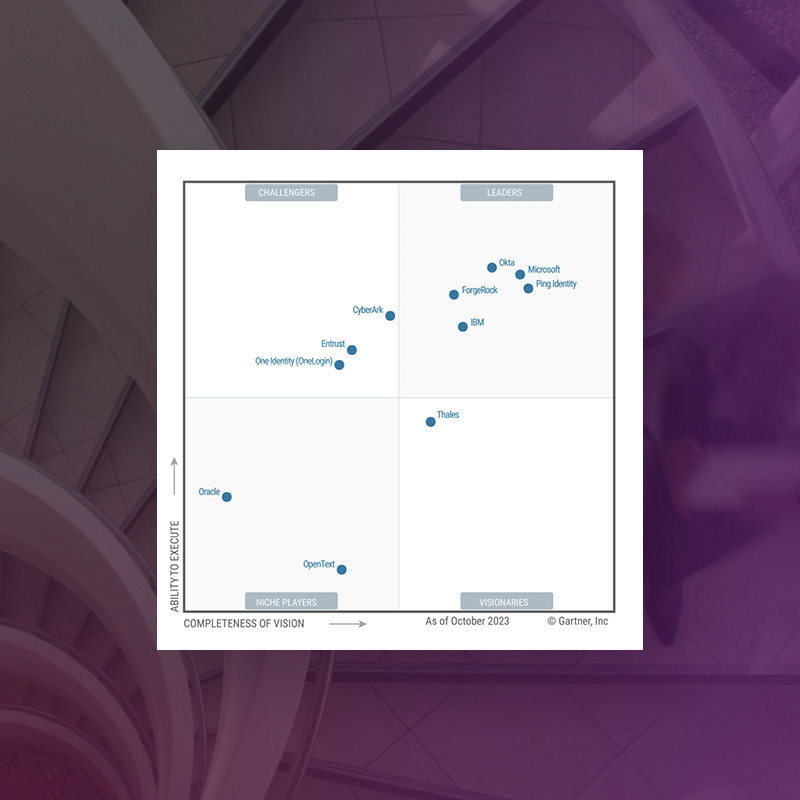
Entrust Named a Challenger for Access Management
Gartner has named Entrust a Challenger in the 2023 Gartner® Magic QuadrantTM for Access Management, recognizing our ability to execute and completeness of vision
What Is Your Zero Trust Maturity Level?
Where does your organization sit within the CISA Zero Trust Framework recommendation? Answer a few short questions to find out.
Key Components of the Zero Trust Framework
Fundamentally, there are three Zero Trust principles integral to this unique security policy.
Assume Breach
A Zero Trust architecture advocates the belief that data breaches are inevitable. It emphasizes the importance of minimizing the attack surface through microsegmentation encryption, and conditional access control policies.
Continuous Authentication
Rather than implicit trust, the Zero Trust model requires your security team to authorize all users based on identity, location, device, data classification, and other variables. After contextual analysis, the user is either granted access, prompted to submit additional information, or blocked.
Least Privileged Access
Credentials are the root cause of many cybersecurity incidents. In turn, the Zero Trust framework requires you to limit privileged access based on user roles and responsibilities. Entities are only authorized to use resources essential to their job – no more, no less.
Featured Products
Identity as a Service (IDaaS)
Cloud-based identity and access management (IAM) solution with multi-factor authentication (MFA), credential-based passwordless access, and single sign-on (SSO).
PKI as a Service
A highly secure PKI that’s quick to deploy, scales on-demand, and runs where you do business.
Entrust KeyControl
Manage cryptographic keys and secrets with decentralized vaults and a comprehensive compliance management dashboard for security policies and regulations.
Digital Certificates
Trust our digital certificates and certificate lifecycle management services for trusted identities and transaction security.
Hardware Security Modules (HSMs)
Our cryptographic solutions not only protect your data, but secure emerging technologies such as cloud, IoT, blockchain, and digital payments.
Our Impact
workforce and consumer identities are protected by Entrust.
of our customers state they’d recommend Entrust Identity to others.
years of digital identity expertise and 50+ years of security innovation.
Implementing Zero Trust
Learn how to begin your Zero Trust journey on the right foot with the help of Entrust experts.
Zero Trust Solution Benefits and Capabilities
Reduced attack surface
A Zero Trust strategy can help organizations verify identities and secure data. PQ-ready solutions help you protect sensitive data, applications, and transactions against threats.
Growth and productivity
Enable business growth without compromising security. We help you take an innovative Zero Trust approach that’s built to secure data across multi-cloud, hybrid, and on-premises environments.
Secure hybrid workforces
Reduce the risk of account takeover (ATO) and insider threats, enabling a hybrid workforce that can securely work from anywhere, on any device.
Integrated ecosystem
Implement best-in-class cybersecurity solutions that can easily integrate with a comprehensive partner ecosystem to provide complete coverage for an optimal Zero Trust strategy.
Protected identities
Build a strong foundation with support for full identity lifecycle management across users, devices, apps, and workloads.
End-to-end encryption
Establish start-to-finish encryption for secure access and communications across devices, networks, and cloud services – all while future-proofing your environment with PQ-ready solutions.
Multi-cloud support
Entrust solutions integrate with a wide variety of cloud service providers and technology partners to offer secure access to virtual machines, containers, and multi-cloud environments and workloads.
Compliance management
Monitor and enforce compliance with legal, industry, and organizational policies and perform annual health and compliance checks to evaluate the progress of your Zero Trust journey.
Verify code integrity
Confirm the unaltered integrity of software and other code and authenticate a software publisher's identity.
Related Resources
Zero Trust Implementation Around the Globe
Highlights from a global survey of cybersecurity decision-makers in the U.S., Europe, and Asia-Pacific.
Inside the Transition to Zero Trust
Entrust and IDC surveyed more than 300 cybersecurity decision-makers on their adoption of Zero Trust strategies.
Entrust named a Challenger in 2023 Gartner® Magic Quadrant™ for Access Management
Learn why Entrust was recognized in the Magic Quadrant report.
Deploying Zero Trust in Ecosystems Where Devices Outnumber Humans
Discover the power of identity-centric technology.
The Critical Role of CLM for Zero Trust Today, and PQ Tomorrow
Read why CLM is essential to the future of your business.
Advancing Your Place on The Zero Trust Maturity Model
Uncover the secret to a successful Zero Trust strategy.
Identity for Workforce
See how our identity and access management solution can make your workforce more secure and productive.

Deploy Zero Trust Security Today
Secure your sensitive data and protect your assets with a foundational portfolio of Zero Trust solutions.
Fill out the form to have one of our Zero Trust experts contact you.
