
Entrust CloudControl
More than 20 capabilities in one risk and security control solution? Experience it for yourself.
What is Entrust CloudControl?
Entrust CloudControl can help you create the unified framework you need to tighten your security compliance across your VMware environment.
With CloudControl, you can:
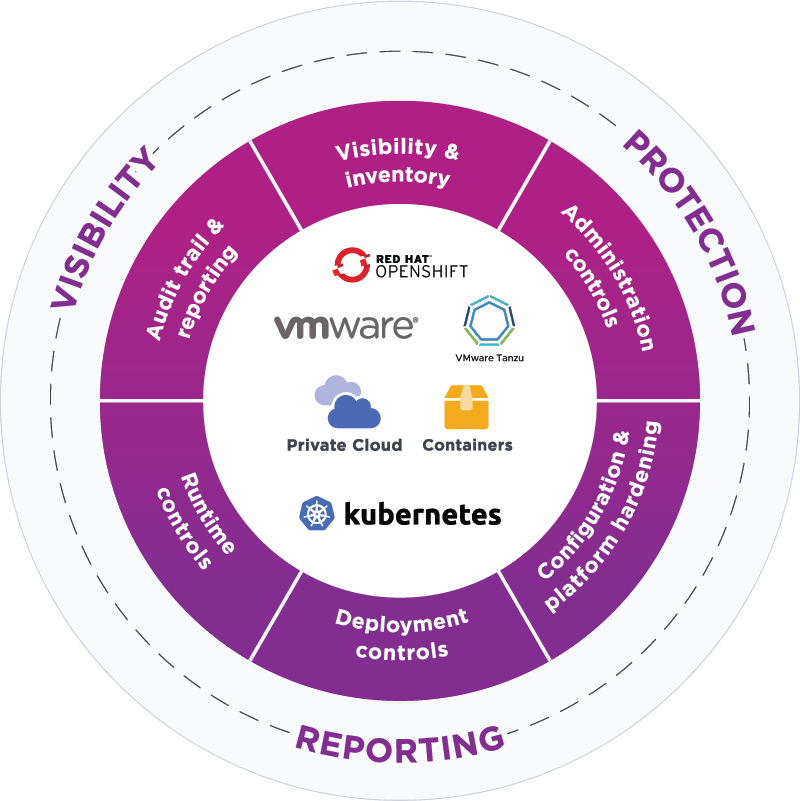
Comprehensive Capabilities
CloudControl offers more than 20 capabilities, which can be customized to meet any organization’s desired risk posture and control activity requirements.
CloudControl Trial for Enhanced Security and Compliance Management for VMware
Test out CloudControl for yourself with our free 30-day trial.

CloudControl for vSphere and NSX
Virtualization and cloud technology have brought new capabilities in automation, time to market, and IT flexibility, but have also heightened the need for hypervisor security.
Entrust CloudControl plays a key role by capturing vital data for compliance, forensics, and troubleshooting, while identifying hypervisor configuration errors in VMware vSphere for ongoing compliance.
VMware NSX consolidates management interfaces and, with Access Control for NSX, ensures secure access to admin consoles through strong authentication, keeping order among internal and external users.
CloudControl Foundation
Entrust CloudControl Foundation Edition provides a comprehensive solution for multi-cloud deployments to meet a broad range of government and industry compliance mandates.


CloudControl for SWIFT
As the incidence and sophistication of cyberattacks on financial networks continues to increase, the Society for Worldwide Interbank Financial Transactions (SWIFT) has introduced the Customer Security Program (CSP) to respond to this threat.
Entrust CloudControl provides a unified framework for security and compliance addressing the CSP requirements, protecting your virtual infrastructure and data.
CloudControl for Containers and Kubernetes
Container-based development provides big gains in productivity, agility, and efficiency, but comes with challenges for security and compliance.
Entrust CloudControl helps secure your container environment across three key dimensions:
- Unified visibility and inventory
- Secure container validation and deployment
- Kubernetes orchestration
Discover a full-stack security solution and get greater visibility and security on your growing cloud-based deployments using VMware Tanzu and RedHat OpenShift platforms.
Unique CloudControl Benefits
Decreased risk of security or availability failures.
Gain full-stack, multi-dimensional policies and administration controls to protect against human errors and insider threats that cause downtime.

Improved agility for virtualized data centers.
Acquire “create one, apply anywhere” policies that support consistent controls and eliminate manual efforts.

Lower operational overhead.
Eliminate multiple consoles and inconsistent security constructs and gain security policies that support “security as code” automation.

Related Resources
Learn about the integration of Entrust CloudControl with VMware vSphere.
Automating Compliance with Swift Global Interbank Security Controls
SWIFT’s CSP boosts banking cybersecurity, reducing risks and minimizing losses from fraud.
The Three Categories of Container Security
Read about the three container security categories in HyTrust Cloud Control (HTCC).
KeyControl for VM Encryption
Data encryption, multi-cloud key management, and granular policy control.
Security as Code
HyTrust Cloud Control 6.0 enables agile, automated security with Trust manifests.
Isolation and Workload Security for Multi-Tenant Lines-of-Business and Applications
Secure SAP environments without the need for air-gapping.
