There’s been quite a buzz about Zero Trust in the last couple of years. Its genesis dates back to 2009, when the then Forrester Research analyst John Kindervag popularized the term when presenting the idea that an organization should not extend trust to anything inside or outside its perimeters. However, Zero Trust is still not a theme that resonates with all IT security experts. There are some who find it too fuzzy and non-deterministic, given that it is more akin to a philosophy or organizational strategy than a prescriptive certification that can be followed to the letter.
Zero Trust Principles – A Look Back in Time
We concluded that Zero Trust is firmly rooted in traditional well-established security design principles. We reached out to our Director of Product Security, Pali Surdhar, to get his view on Zero Trust. Pali forwarded a vintage document for our edification. The document “The Protection of Information in Computer Systems,” authored by Jerome H. Saltzer and Michael D. Schroeder, was published a mere 49 years ago in 1975. This was a time when computers were the preserve of universities, industry, and governments, and usually so big that they needed a large room to accommodate them. It was a time when Gates, Allen, Jobs, and Wozniak were just fledgling computer enthusiasts about to start their transformational journey in personal computing.
A quote from the abstract section of the paper gives a flavor of the content. “[this paper] examines in depth the principles of modern protection architectures and the relation between capability systems and access control list systems, and ends with a brief analysis of protected subsystems and protected objects.”
Security Principles Circa 1975
The paper then introduces three security categories:
- Unauthorized information release
- Unauthorized information modification
- Unauthorized denial of use
These terms still resonate, although today we’d probably describe them as data breach, code hacking, and finally, Denial of Service, or perhaps a ransomware attack, where a bad actor has taken measures to lock out the authorized user.
The paper then provides examples of security techniques sometimes applied to computer systems. We thought it would be worthwhile translating into today’s cybersecurity terminology.
| Security Techniques – 1975 | Today’s Security Terminology | Aligned with a Zero Trust Principle? |
|---|---|---|
| Labeling files with lists of authorized users | Access Control List – defines who has access to a system or application. Authorization and authentication could apply here too. | Yes |
| Verifying the identity of a prospective user by demanding a password | Password verification or even passwordless MFA | Yes |
| Shielding the computer to prevent interception and subsequent interpretation of electromagnetic radiation | Side channel attacks. Typically require an antenna or probe within close proximity of a device to eavesdrop by analyzing electromagnetic signals. | N/A |
| Enciphering information sent over telephone lines | Encryption, probably using TLS or similar. Refer to our last blog post Harvest Now, Decrypt Later – Fact or Fiction for more information. | Yes |
| Locking the room containing the computer | Access control, defense in depth, secure room/vault, etc. These security measures are all still in use today. | Yes |
| Controlling who is allowed to make changes to the computer system (both its hardware and software) | Least privilege principle – only giving access to those who have the correct clearance and need access to the system | Yes |
| Using redundant circuits or programmed cross-checks that maintain security in the face of hardware or software failures | High availability would typically be used today with hardware devices having a backup device ready to continue service should a failure occur. Software can be designed with similar fault tolerance. | N/A |
| Certifying that the hardware and software are actually implemented as intended | In today’s IT environment this would involve a combination of internal quality assurance, security testing, and approval of hardware or software design. In addition, the code or hardware could be submitted to a third party for penetration testing and product certification against industry standards such as FIPS 140-2/3 or PCI DSS. Given today’s complex software and hardware systems, knowing the provenance of the components is essential. This is achieved through bills of materials, code signing, and security processors in hardware. | Yes |
So while the language used is reflective of the time it was written, we think you’ll agree that most of the ideas conveyed are security principles that equally apply in today’s modern distributed architectures.
NIST, CSA, and the CIA Triad
For those not inclined to read the 59-page NIST SP 800-207 document, here are the seven core tenets of Zero Trust.
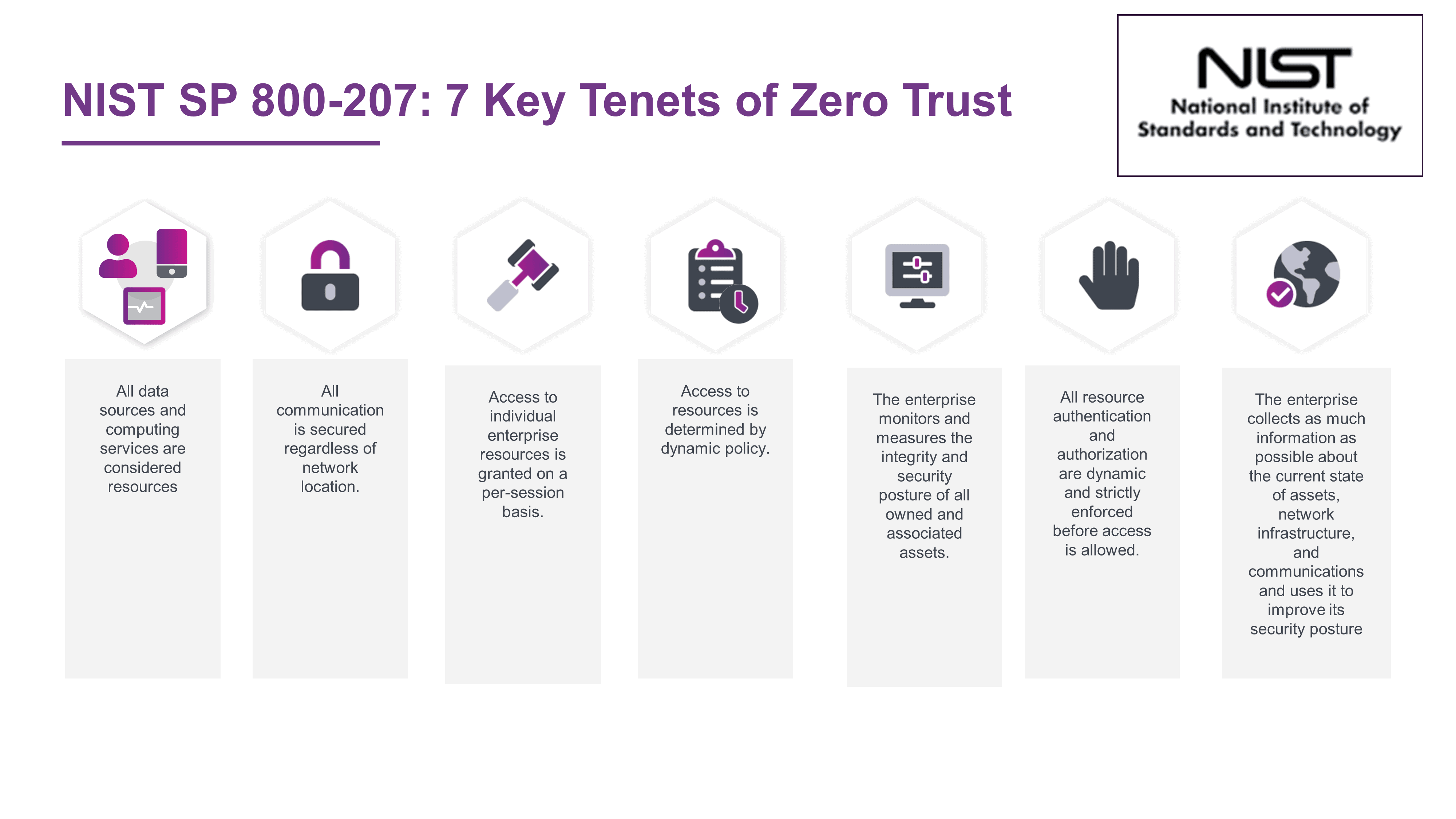
Building on the NIST publication, the Cloud Security Alliance (CSA) has recently published its Zero Trust Guiding Principles. For anyone who wants to get up the learning curve on Zero Trust without digging too much into the weeds, it is an excellent read. It is also reassuring that the CSA Zero Trust Working Group are of the same opinion as us:
“Zero Trust is a collection of long-standing principles applied in a way that aligns the security architecture with the way we work and live.“
The CSA document then provides a list of the security principles critical to the success of your Zero Trust effort:
- Concept of least-privilege access controls (e.g., preventative)
- Separation of duties (e.g., preventative)
- Segmentation/micro-segmentation (e.g., preventative)
- Logging and monitoring (e.g., detective)
- Configuration drift remediation (e.g., corrective/reactive)
While the term Zero Trust was coined by Kindervag 34 years after the Saltzer & Schroeder paper, we think you’ll agree that many of those principles align with the 1975 document.
And while things have certainly changed since 1975, when computers were monolithic and had limited networking capabilities (think remote users connecting in from terminals), the concerns about security were the same: protecting confidentiality, integrity, and availability of data. Hopefully most of you will be familiar with the CIA triad, another cybersecurity fundamental.
The Unchanging Need for Robust Security
Today, while the concerns remain the same, the complexity of compute environments has greatly increased. For example, in current environments, systems can be spread out across multiple clouds, software systems consist of many microservices, and data resides everywhere, just to name a few of the complexities. Additionally, today’s users not only consist of internal computer users sitting at their desks with directly connected terminals, but also potentially anyone, anywhere on the planet, accessing these complex systems via the internet.
The problem, and the strategy to mitigate the problem, have remained somewhat unchanged over the years. It is just the scale of the problem that has changed. Saltzer and Schroeder knew that the identity of a user needed to be established. They specified using a password for this. At the time with the limited access (no wide area network) this was sufficient. Today users (and adversaries) can access systems from anywhere. This makes establishing identity require something more than a strong password.
Furthermore, while Saltzer and Schroeder talked about locking their 1970s computer room (i.e., protecting the perimeter), they recognized that wasn’t in itself sufficient. In today’s world of distributed users and a multitude of devices wanting access, those physical walls have been replaced by a virtual perimeter, making it even harder to protect and further emphasizing the need for alternative approaches. Zero Trust therefore does not focus on perimeter defense, but instead advocates for strong identity (never trust, always verify) and micro-segmentation (to avoid lateral movement through the network). Sometimes what’s old is new, and that is because we have had a good thing all along.
Whether your organization is embarking on a Zero Trust journey or looking to strengthen its overall security posture by implementing more robust measures based on well-established security principles, consider reaching out to Entrust. Discover how we can assist you in securing your environment.




