
The Ultimate Guide to CMMC
Regulations and requirements come with the territory when you’re operating at the federal level. That said, implementing controls and achieving compliance is much easier said than done — especially when it comes to the Cybersecurity Maturity Model Certification (CMMC).
Not sure where to get started? We’re here to help. Read on to learn the ins and outs of CMMC and how your organization can take the pain out of compliance.
What is CMMC?
The Cybersecurity Maturity Model Certification program is a verification mechanism designed to ensure all Defense Industrial Base (DIB) companies implement adequate cybersecurity practices. Based on the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, the CMMC framework unifies all DIB contractors under one certifiable security standard.
In short, all Department of Defense (DoD) mission partners are required to adopt the same set of security controls, depending on certain variables. Regardless, any government contractor bidding on a DoD contract must obtain a CMMC certification, thereby verifying they’ve fulfilled their requirements.
Why was CMMC created?
In October 2016, the DoD issued the Defense Federal Acquisition Regulation Supplement (DFARS) Clause 252.204-7012 — titled “Safeguarding Covered Defense Information and Cyber Incident Reporting.” Under this regulation, defense contractors were only required to self-attest their own cybersecurity maturity.
However, auditing was often inaccurate and rarely conducted, resulting in inconsistent compliance. In turn, DoD agencies didn’t have assurance that their mission partners were taking all necessary steps to protect government assets.
In an effort to migrate away from this self-attestation model, the DoD unveiled CMMC in 2019. It began incorporating CMMC standards into DoD contract requirements in November 2020.
Why is CMMC compliance important?
The purpose of the CMMC framework is to protect government information from unauthorized access and exposure. More specifically, it mandates practices for securing two types of data:
- Controlled Unclassified Information (CUI): Controlled Unclassified Information is any data that doesn’t carry classified status but still needs to be safeguarded due to particular government policies and ordinances. CUI can pertain to critical infrastructure, financial records, national defense, and other sensitive areas.
- Federal Contract Information (FCI): By contrast, FCI is information provided by or generated for the U.S. government under contract that hasn’t been marked for public release. Although not as sensitive as CUI, Federal Contract Information must still be strictly protected.
With a growing swarm of cyberattacks targeting government agencies, CMMC compliance has become vital. State-sponsored hacks can be especially costly, ringing in an average cost of $4.43 million per breach. Worse yet, given the nature of government data, these attacks can jeopardize U.S. interests — including national security.
What are the benefits of gaining a CMMC certification?
Defense contractors have every reason to comply with CMMC requirements. Not only is it mandatory for all mission partners, but it’s also a competitive business advantage. For instance, earning a CMMC certification can:
- Help you bid on DoD contracts
- Provide a high level of assurance to agency customers
- Strengthen your cyber resilience and minimize risk exposure
What’s CMMC 2.0?
The DoD announced plans to update and simplify the CMMC framework in November 2021. The aim was to make it easier for contractors to implement and comply with CMMC standards while streamlining the certification process.
It consolidated its framework into a more uniform, comprehensive, and easily understandable rendition: CMMC version 2.0. Looking ahead, the DoD will require at least some level of CMMC certification to qualify for a contract award by October 1, 2025.
How does CMMC compliance work?
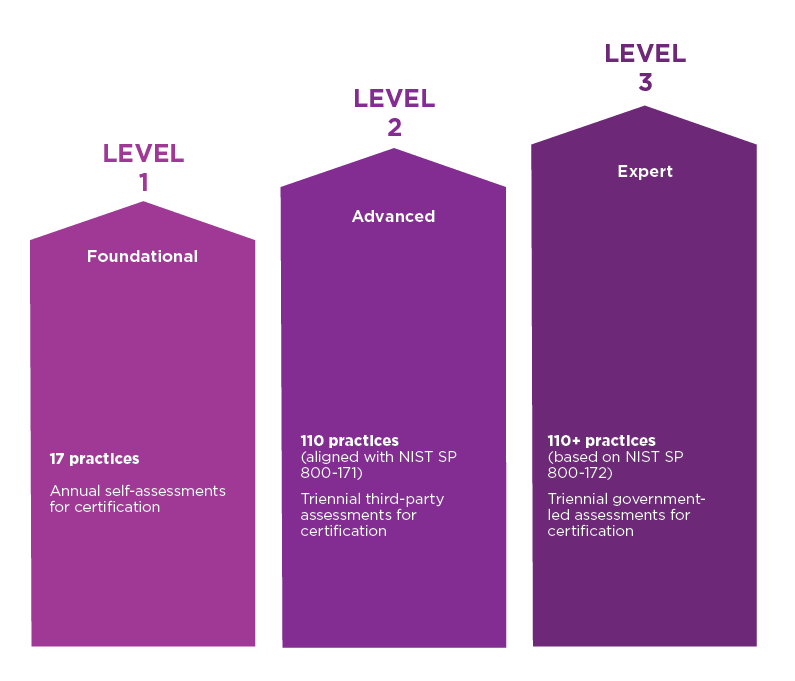
CMMC organizes its requirements using a tiered system. Whereas the original version contained five independent levels, CMMC 2.0 simplified the framework down to three.
They’re aligned based on how contractors (and subcontractors) handle FCI and CUI. Generally, the more sensitive information you process, the more stringent your compliance requirements.
As such, each level has its own processes, practices, and assessment procedures and builds upon the previous.
- CMMC Level 1 (Foundational): 17 practices verified through self-assessment.
- CMMC Level 2 (Advanced): 110 practices aligned with NIST SP 800-171, verified by a triannual third-party security assessment.
- CMMC Level 3 (Expert): 110+ practices based on NIST SP 800-172, verified through a triannual government-led security assessment.
CMMC also breaks down specific cybersecurity practices into 14 domains with 43 capabilities. In this context, the term “capabilities” refers to the security controls a DoD contractor must implement and manage depending on their corresponding level. The CMMC domains include:
- Access Control
- Audit and Accountability
- Awareness and Training
- Configuration Management
- Identification and Authentication
- Incident Response
- Maintenance
- Media Protection
- Personnel Security
- Physical Protection
- Risk Assessment
- Security Assessment
- System and Communications Protection
- System and Information Integrity
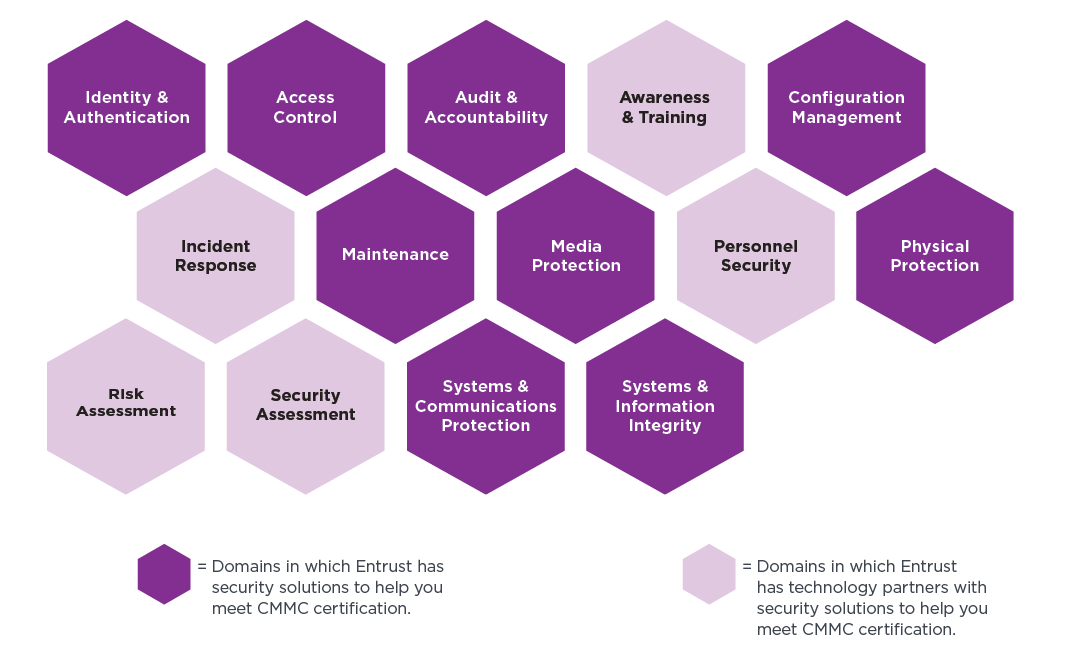
Entrust provides solutions to facilitate compliance with the following 9 CMMC domains:
Capability
- Establish system access requirements
- Control internal system access
- Control remote system access
- Limit data access to authorized users and processes
- Define audit requirements
- Perform auditing
- Identify and protect audit information
- Review and manage audit logs
- Establish configuration baselines
- Perform configuration and change management
- Grant access to authenticated entities
- Manage maintenance
- Identify and mark media
- Protect and control media
- Sanitize media
- Protect media during transport
- Limit physical access
- Define security requirements for systems and communications
- Control communications at system boundaries
- Identify and manage information system flaws
- Identify malicious content
- Perform network and system monitoring
- Implement advanced email protection
How do you become CMMC-certified?
The CMMC assessment process is rigorous by design. Starting your compliance journey can be daunting, but with a well-planned checklist you can take it one step at a time.
Let’s review each one to help you get started:
- Determine your CMMC level: Your minimum cybersecurity maturity level depends on how you handle FCI and CUI. Take inventory of your systems, networks, and processes to identify exactly where and how you come in contact with this data.
- Complete a self-assessment: Conduct a CMMC gap analysis to detect vulnerabilities or areas of improvement that aren’t aligned with best practices.
- Build a system security plan (SSP): SSPs are required for CMMC certification. They map your security landscape and control capabilities, allowing you to identify your environment’s boundaries, where it connects to other systems, and how well you execute certain requirements.
- Invest in future-ready tools: You’ll likely discover gaps in your cybersecurity posture. Be prepared to deploy additional solutions to cover the bases and satisfy your CMMC compliance requirements.
- Engage a third-party auditor: The CMMC audit must be completed by a Registered Practitioner, Registered Provider Organization, or Third-Party Assessment Organization (3PAO).
- Maintain compliance: Once certified, you must implement continuous monitoring to identify gaps as they arise and ensure security controls continue to operate as intended.
Simplify compliance with Entrust solutions
Compliance is mandatory if you’re a DoD contractor. Unfortunately, that doesn’t mean it’s easy.
However, there are ways you can simplify the process, harden your defenses, and achieve and maintain a CMMC certification. With Entrust as your expert partner, you can deploy a portfolio of solutions that not only get you CMMC-ready, but also help you future-proof security for years to come.
From identity and authentication to media protection, access control, and more, we help you facilitate CMMC domains with ease. Whether it be through Entrust Public Key Infrastructure or Entrust Identity as a Service, you can rest assured you — and your DoD partners — are well-protected.
