Cybersecurity Maturity Model Certification (CMMC)
Ebook: Getting CMMC Ready
What is CMMC? What does your organization need to do to prepare for it? And which Entrust solutions can help you get CMMC ready? Read this ebook to find out.

Entrust facilitates CMMC compliance so contracting networks can continue to support DoD and other government agencies.
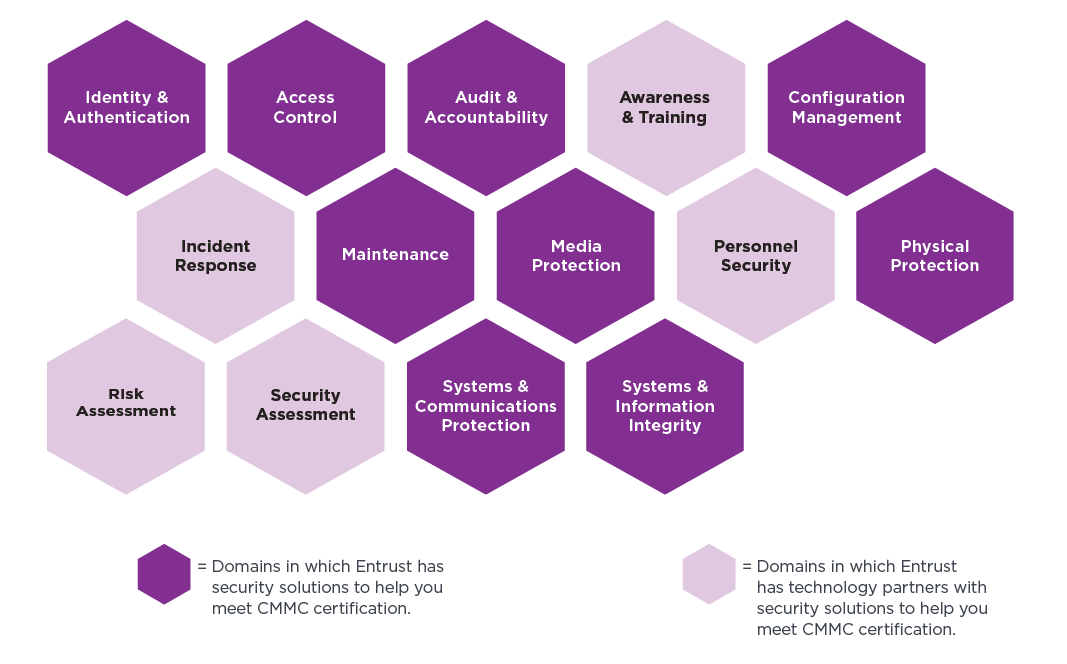
Cybersecurity Maturity Model Certification (CMMC) is a program established by the U.S. Department of Defense (DoD) to secure and protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) by requiring the certification of external contractors across 14 different domains, each with three specified levels of certification.
CMMC is a unified standard for implementing cybersecurity across DoD’s contracting network, which includes over 300,000 companies in the supply chain. CMMC is the DoD's response to significant compromises of sensitive defense information located on contractors' information systems.
- Release date was January 1, 2020.
- The DoD began incorporating CMMC requirements into select RFPs / RFIs as of November 30 , 2020.
- By October 1, 2025, all DoD contract awards will require at least some level of CMMC certification. And while DoD was the catalyst for CMMC, it is now gaining traction across the Defense Industrial Base (DIB), including the Department of Homeland Security and other federal government departments and agencies – especially post SolarWinds.
Are you prepared for CMMC compliance?
Historically, contractors were responsible for implementing, monitoring, and certifying the security of their information technology systems and any sensitive DoD information stored on or transmitted by those systems.
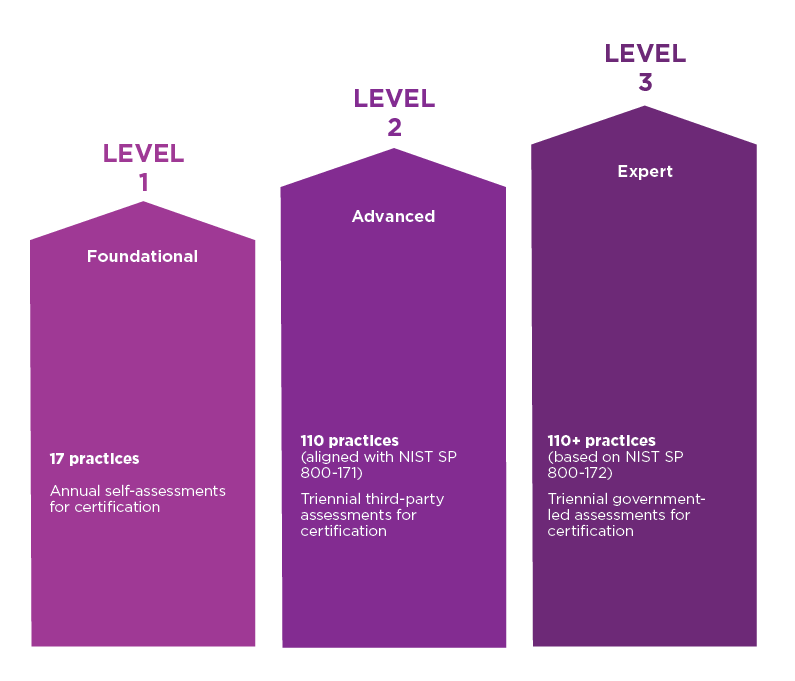
Starting November 30, 2020, DoD began incorporating CMMC requirements into select RFPs, RFIs, and research contracts. By October 1, 2025, all DoD contract awards will require at least some level of CMMC certification. The model consists of 3 levels of maturity – foundational, advanced and expert – which is dependent on the type of information being handled. Each level also has different assessment requirements of either self-assessments, third party assessments, or government led. Entrust’s digital security portfolio including identity, certificate, and data protection solutions facilitates compliance with 9 CMMC domains across the three possible levels of certification.
Key questions to determine what level of maturity your organization needs
Is the organization handling basic information, such as Federal Contract Information (FCI)? Or is it Controlled Unclassified Information (CUI)? FCI requires a Level 1 certification, but CUI requires at least a Level 2.
Where are the gaps between the organization’s current cybersecurity stance and the desired CMMC level? A gap assessment will be invaluable for defining a plan of action and milestones toward achieving CMMC cybersecurity maturity.
CMMC encompasses the security requirements specified in NIST SP 800-171, as well as additional requirements from other standards and sources, which varies by certification level. What will a gap assessment reveal about the organization’s current level of cybersecurity hygiene?
Keep in mind the ultimate goal of CMMC: Keeping FCI and CUI out of the hands of malicious cyber attackers.
Entrust is here to help
Entrust provides solutions to facilitate compliance with the following 9 CMMC domains:
Capability
- Establish system access requirements
- Control internal system access
- Control remote system access
- Limit data access to authorized users and processes
- Define audit requirements
- Perform auditing
- Identify and protect audit information
- Review and manage audit logs
- Establish configuration baselines
- Perform configuration and change management
- Grant access to authenticated entities
- Manage maintenance
- Identify and mark media
- Protect and control media
- Sanitize media
- Protect media during transport
- Limit physical access
- Define security requirements for systems and communications
- Control communications at system boundaries
- Identify and manage information system flaws
- Identify malicious content
- Perform network and system monitoring
- Implement advanced email protection
CMMC Capability Domains