
What Is A Hardware Security Module (HSM)?
Hardware security modules (HSMs) are hardened, tamper-resistant hardware devices that secure cryptographic processes by generating, protecting, and managing keys used for encrypting and decrypting data and creating digital signatures and certificates.
HSMs are tested, validated and certified to the highest security standards including FIPS 140-2 and Common Criteria. Entrust is a leading global provider of HSMs with the nShield General Purpose HSM product family.
HSMs enable organizations to:
What is HSM as a service or Cloud HSM?
HSM as a service is a subscription-based offering where customers can use a hardware security module in the cloud to generate, access, and protect their cryptographic key material, separately from sensitive data. The service offering typically provides the same level of protection as an on-premises deployment, while enabling more flexibility. Customers can transfer CapEx to OpEx, enabling them to only pay for the services they need, when they need them.
nShield as a Service uses dedicated FIPS 140-2 Level 3 certified nShield HSMs. The offering delivers the same full set of features and functionality as on-premise nShield HSMs, combined with the benefits of a cloud service deployment. This allows customers to fulfill either their cloud first objectives or deploy a mix of on-premise and as-a-Service HSMs, with maintenance of the as-a-Service appliances performed by the experts at Entrust.
Why should I use an HSM?
Cryptographic operations like encryption and digital signing are worthless if the private keys they use are not well protected. Attackers today have grown much more sophisticated in their ability to locate private keys that are stored or are in use. HSMs are the gold standard for protection of private keys and associated cryptographic operations, and enforce the policy defined by the using organization for users and applications that can access those keys.
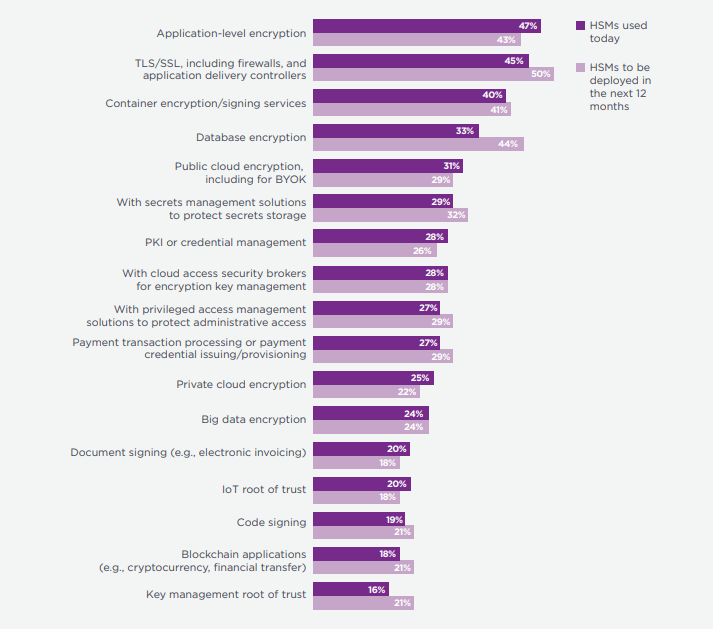
HSMs can be used with many different types of applications that perform encryption or digital signing. The top use cases for HSMs, from the Ponemon Global Encryption Trends Study, are shown in the figure below.
How HSMS are deployed or planned to be deployed in the next 12 months
Learn more about why you should use an HSM
What is a Root of Trust?
Root of Trust is a source that is trusted by default within a cryptographic system. Hardware Root of Trust and software Root of Trust components are inherently trusted, which means they must be inherently secure. The most secure implementation of Root of Trust typically includes a hardware security model (HSM), which generates and protects keys and performs cryptographic functions within a secure environment.
What value does an HSM provide?
HSMs enhance and extend the security of a wide range of applications that perform encryption and digital signing. The table below describes the added value of HSMs for a set of the most common use cases.
| Use Case | Value of HSM to Use Case |
| Cloud and Containers/Kubernetes | Maintain control of keys and data in the cloud; secure containerized applications |
| Public Key Infrastructure (PKI) | Protect critical PKI root and CA signing keys |
| Privileged Access and Secrets Management | Address insider threats and simplify access to secrets for DevOps |
| Encryption and Tokenization | Enhance encryption key protection for data in transit and storage |
| Key Management | Enforce key management policy across multiple clouds and applications |
| Digital Signing and Code Signing | Protect keys that ensure software integrity and enable legally binding transactions |
| TLS/SSL applications (ADCs, Firewalls, etc.) | Secure master TLS/SSL encryption keys |
| Identity and Authentication | Create trusted identity credentials |
| Payments | Protect the keys that create and sign payment credentials |
What is random number generation?
Random number generation (RNG) refers to the random numbers created by an algorithm or device. It is important that cryptographic keys are created using a certified source of random numbers, which is a challenging problem for software-based systems.
When the source of entropy for a random number generator is derived from software-based measurements, it cannot be guaranteed that the entropy will not be predictable, or able to be influenced. An HSM uses a hardware-based source of entropy for its RNG that has been verified to provide a good source of entropy in all normal operating conditions.
This is important for use cases like BYOK (Bring Your Own Key), which allows users to create and manage keys that they upload to cloud service providers.
What Makes Entrust a Top HSM Vendor?
Countless organizations have chosen Entrust as their go-to partner when it comes to hardware security modules. Why? Because we’re setting the industry standard for secure and versatile data protection. We’ve been designing, innovating, and selling HSMs for over 25 years.
Our nShield HSMs are engineered to deliver robust security with a strong root of trust. That way, you can rest assured your cryptographic assets are protected.
Here’s what you can expect from Entrust as your trusted advisor:
- Comprehensive protection: Entrust HSMs are designed with a robust, tamper-resistant architecture, providing the highest level of assurance to safeguard your sensitive data against sophisticated threats. Our FIPS 140-2 Level 3, FIPS 140-3 Level 3 (coordination stage) and Common Criteria EAL4+ certifications demonstrate our commitment to meeting stringent security standards.
- Flexible deployment: One-of-a-kind businesses deserve better than one-size-fits-all security. We offer multiple deployment options, including on-premises, cloud, and hybrid models. Plus, our extensive HSM ecosystem includes over 150 documented integrations with other solutions. That way, your needs are covered no matter the use case.
- Innovative solutions: At Entrust, we are constantly innovating to stay ahead of evolving security challenges — including the post-quantum threat. Our devices leverage the Security World architecture, which uniquely allows you to support a versatile key management framework that spans the entire Entrust nShield family of general-purpose Hardware Security Modules (HSMs). And, with the CodeSafe software developer toolkit, you can write and execute sensitive applications inside the tamper-resistant boundary of FIPS-certified nShield devices.
- Trusted expertise: With 25+ years of experience, Entrust is a dedicated partner for businesses worldwide. Our team of experts is committed to providing you with the support and guidance you need to implement and maintain a future-proof security posture.
