
Single Sign-On (SSO)
Traditionally, signing in to a user account required two login credentials: a username and password. But now, with dozens of applications, resources, and services to consider, providing secure access isn’t so simple.
The good news? Rather than having to remember or manage multiple passwords, customers and employees can access essential systems using just one set of user credentials. In short, that’s what Single Sign-On (SSO) is all about.
Read on to learn everything you need to know about SSO authentication, including why it’s important, how it works, and how to protect your SSO setup.
What is SSO?
Single sign-on is a federated identity management function that enables users to access multiple applications with just a single set of login credentials. For example, when an employee enters their identity credentials to log in to their workstation, SSO authentication also provides access to their apps, software, systems, and cloud-based resources.
Likewise, say someone logs in to a Google service like Gmail. SSO automatically authenticates them, allowing their user account to access other Google apps, such as YouTube or Google Sheets. And, if they sign out of any of these applications, they’re automatically logged out of the rest.
Why is SSO important?
At its core, an SSO solution is an authentication service, which is a crucial part of identity and access management (IAM). In turn, it’s also an especially valuable foundation for the Zero Trust security model — a framework that advocates against implicit trust and requires continuous user authentication.
Why does this matter? If a system doesn’t know who a user or entity is, there’s no way to allow or restrict their actions, creating a major data security risk. This is even more problematic given the proliferation of cloud apps and services, each one requiring its own set of user credentials.
According to the latest estimates, the average enterprise uses 210 distinct collaboration and cloud services, and the average employee uses 36 cloud services at work. That’s a lot of passwords to manage, and unfortunately, many organizations have a far-too-fragmented IT infrastructure to govern them appropriately.
Luckily, that’s where SSO implementation comes into play. Reducing multiple passwords down to one set of login credentials not only improves the user experience, but promotes better cybersecurity hygiene for all.
What are the advantages of SSO?
SSO implementation can provide several benefits to users, enterprises, and customers alike. For example:
Better user experience, productivity, and cost-savings
Boiling multiple passwords down to one unified set of user credentials can streamline the login process, allowing employees to leverage resources as quickly as possible. This is especially vital in a hybrid work environment, where the most essential applications are increasingly on-premise or in the cloud.
Ultimately, this accelerated workflow translates into employee productivity gains. Better yet, even a small timesaver such as SSO can have a tangible financial impact. According to research, saving three minutes of an employee’s time can eventually save a 5,000-person company about $1.5 million per year.
Plus, an SSO solution can minimize unproductive tasks, such as IT help desk requests for password resets.
Improved security via stronger password hygiene
At least 45% of breaches are a result of compromised login credentials — and in most cases, weak password security. When people have to remember multiple username-password combinations, they eventually start reusing the same ones for various accounts.
This is called “password fatigue.” It’s a big security risk because it means if one account is compromised, all other services can be, too. In other words, attackers could use the same password to hack the victim’s other applications.
SSO implementation mitigates password fatigue by reducing all logins down to one. Although a bad actor could access other services if they manage to compromise one account, SSO theoretically makes it easier for individuals to create, remember, and use strong passwords.
However, in reality, this isn’t always the case. That’s why it’s best to support your SSO solution with additional security measures — but more on that later.
Simpler policy enforcement and identity management
SSO provides a single point of entry for passwords, making it easier for IT teams to enforce security policies and rules. For instance, period password resets are much simpler to manage with SSO, as each user has just one credential they need to change.
More importantly, if implemented correctly, federated identity management stores login credentials internally in a controlled environment. By contrast, organizations store traditional username-password combinations externally with little visibility over how they’re managed, such as in a third-party application. This makes it more difficult to ensure credentials are managed according to data security best practices.
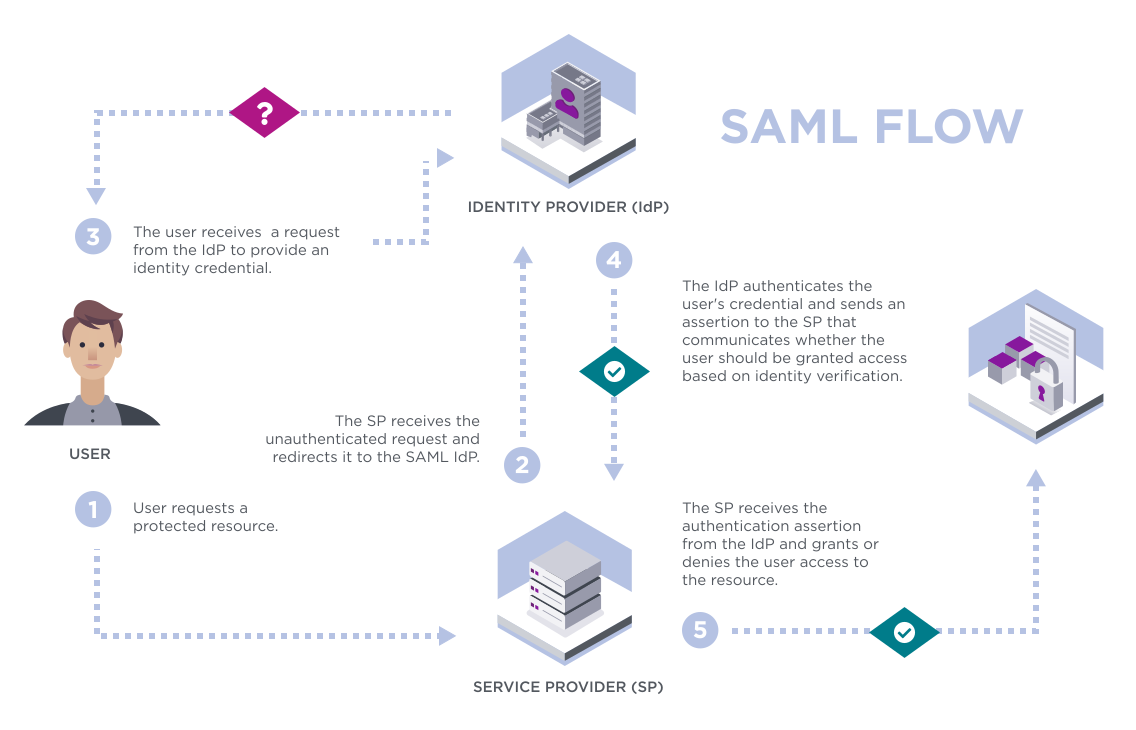
How does SSO work?
SSO is often referred to as a function of “identity federation.” In simple terms, identity federation is a trust system between two parties for authenticating users and exchanging information required to authorize their access to certain resources. Most often, this involves using Open Authorization (OAuth) — a framework that gives applications the power to grant secure access without revealing the actual login information.
Generally, the SSO authentication workflow is a fast and simple process:
- First, the user requests access to a resource within the SSO setup, initiating the login process.
- The resource’s service provider, such as the host website, redirects the user to an identity provider, like Entrust.
- The identity provider verifies the user’s identity by checking their credentials using one of several SSO protocols.
- If the user is successfully verified, the identity provider generates an SSO token (also known as an authentication token). In brief, this is a digital asset that represents the user’s authenticated session.
- The identity provider sends the SSO token back to the service provider, which then verifies its validity. If necessary, the application, system, or service provider can verify the user identity further by issuing an additional authentication request.
- Once verified, the service provider grants the user access to their resource or application.
Now, the user can use all other applications configured in the SSO setup. If they have an active session, the SSO solution uses the same authentication token to grant access.
Are there different types of SSO?
Yes, there are various SSO protocols and standards. Each SSO configuration works a bit differently, but all follow the same general process. Some of the most common include:
- Security Access Markup Language (SAML): The SAML SSO configuration is an open standard for encoding text into machine language and conveying identity information. Compared to others, it’s a widely applicable authentication protocol, whereas others are designed for specific secure access use cases. Security Assertion Markup Language is also the main standard used to write SSO tokens.
- Open Authorization (OAuth): OAuth is an open standard protocol that encrypts identity information and transmits it between applications — thereby allowing users to access data from other apps without manually verifying their identity.
- OpenID Connect (OIDC): As an extension of OAuth, OIDC enables multiple applications to use one login session. As a common example, many services allow you to sign in using a Facebook or Google account instead of your user credentials.
Is SSO secure?
Single sign-on may provide a great user experience, but it’s not in and of itself a perfect solution. Hackers can take advantage of SSO’s convenience if access control and password policies aren’t sufficient.
If your SSO authentication consists of a single password without multi-factor authentication for multiple applications, you’ve made your users more productive, but multiplied your risk. For example, if a bad actor compromises an SSO account, they may have unfettered access to the other applications within the same configuration.
To alleviate risk, it’s best for organizations to complement SSO with additional layers of security, such as:
- Risk-based adaptive authentication, which provides a step-up challenge when contextual data indicates a potential threat. If someone attempts to log in from an unknown or unmanaged device, the authentication scheme may ask them to provide additional information, such as a one-time passcode.
- Credential-based passwordless authentication, which replaces traditional passwords with biometrics or tokens for fast, frictionless access. And the best part? No password, nothing to steal — no way of breaking through the defenses.
How do you implement SSO authentication?
SSO can be a major boon to productivity, but it also comes with risk. So, to ensure your SSO implementation is as secure as can be, consider the following best practices:
- Map out your applications: Identify which software, systems, apps, and services should be included in your SSO configuration.
- Choose an identity provider: Look for a flexible SSO solution that’s platform-agnostic and compatible with all browsers. More importantly, ensure your identity provider also delivers multiple security capabilities to guarantee your deployment is well-protected.
- Verify user privileges: In the spirit of the Zero Trust framework, base your access control decisions on the concept of “least-privileged access.” The idea is each user receives only the minimal permissions they need to perform their job responsibilities. That way, if they lose control of their account, a hacker can’t use certain applications.
What makes Entrust SSO different?
Our IAM platform, Entrust Identity, supports SSO so your users can access all applications with a single strong credential instead of managing credentials for each unique cloud, on-prem, and legacy application. Better yet, it provides every core capability you need to realize a Zero Trust architecture, including:
- Multi-factor authentication
- Passwordless access
- Deployment flexibility
- Seamless integrations
- Centralized management
Best of all, Gartner recognized Entrust as a Challenger in the 2023 Magic Quadrant™ for Access Management — highlighting our ability to execute and completeness of vision.
Download the report to learn more about why Entrust is poised to help you leverage a secure SSO implementation.
Frequently Asked Questions
What is single sign-on and what is it used for?
Single sign-on (SSO) is a method of authentication that allows users to securely access multiple applications and websites with a single set of credentials. It eliminates the need for users to remember multiple usernames and passwords. It also provides an easy way for them to access all of their accounts without having to re-enter credentials each time. With SSO, a single username and password can be used to log into all associated services, allowing users to have a secure and seamless experience across all applications.
What are the advantages of SSO?
SSO has numerous benefits, including:
- Improved User Experience: Eliminate the need for users to remember multiple usernames and passwords, making it easier for them to access the resources they need.
- Increased Security: Reduce the risk of password reuse and phishing, making it more difficult for unauthorized users to access sensitive information.
- Improved Productivity: Allow users to access the resources they need more quickly, which can lead to increased productivity and revenue.
- Enhanced User Management: Streamline the process of managing and maintaining multiple user accounts, making it more efficient for IT teams.
- Cost Savings: Reduce the cost associated with managing multiple usernames and passwords, data breaches, and security incidents.
Entrust provides an SSO solution that can easily integrate with your existing systems and applications.
How does SSO work?
SSO works by creating a central authentication server, known as an Identity Provider (IdP), that is used to authenticate users for multiple applications or services. Once a user is authenticated by the IdP, they can access all the applications or services they are authorized to use without the need for additional usernames and passwords.
To set up SSO, an organization typically configures the SSO service and then integrates it with the applications or services they want to use. Once set up, when a user attempts to access an application or service, they will be redirected to the IdP to sign in. Once they have signed in, they will be able to access the applications or services they are authorized to use without having to enter their login credentials again.
Entrust supports different SSO methods, such as SAML, OpenID Connect, and OAuth2. We provide step-by-step instructions on how to set up SSO with Identity Provider, along with support and guidance throughout the process.
Are there security risks for SSO?
While SSO can improve security by reducing the risk of password reuse, there are still security risks that organizations should be aware of.
- Single Point of Failure: If the SSO system is compromised, unauthorized users could gain access to multiple applications or services at once.
- Phishing: Phishing attacks can still occur, even with SSO, if users are tricked into providing their login credentials to a fake website.
- Session Hijacking: An attacker could steal a user's session and gain access to multiple applications or services if the session is not properly secured.
- Third-Party Access: SSO relies on third-party identity providers and if one of them is compromised, it could lead to a security breach.
- Lack of Multi-Factor Authentication: SSO may not provide the added security of multi-factor authentication by default.
Entrust’s SSO solution is designed with security in mind, and it is regularly updated to address new security risks as they emerge. We add another layer of protection by offering the widest range of MFA authenticators, including Grid Cards, Mobile Push Notifications, High Assurance PKI-based Credentials, Passwordless, and more!
How is SSO different from traditional authentication methods?
SSO is different in several ways:
- Centralized Authentication: SSO uses a central authentication server, known as an Identity Provider (IdP), to authenticate users for multiple applications or services. Traditional methods typically require users to sign in separately for each application or service.
- Single Set of Credentials: It allows users to access multiple applications or services with just one set of login credentials, eliminating the need to remember multiple usernames and passwords. Traditional methods typically require users to remember multiple usernames and passwords for each application or service.
- Improved User Experience: It improves the user experience by making it easier for users to access the resources they need, without having to remember multiple usernames and passwords.
- Enhanced Security: It can improve security by reducing the risk of password reuse and phishing, making it more difficult for unauthorized users to access sensitive information.
Our solution is designed to work seamlessly with traditional methods, and it can be easily integrated with existing systems and applications, whether on-premises or cloud.
What security measures should organizations take when implementing SSO?
When implementing Single Sign-On, organizations should take the following security measures:
- Secure the SSO environment: Implement firewalls, intrusion detection and prevention systems, and other security tools to protect the SSO environment from unauthorized access.
- Use multi-factor authentication: Implement multi-factor authentication (MFA) as an added layer of security to ensure that users are who they claim to be. Entrust provides robust security measures by implementing multi-factor authentication (MFA) as an added layer of protection. Our platform offers a wide range of MFA options, such as grid cards, mobile push notifications, high-assurance PKI-based credentials, and passwordless, ensuring that only authorized users have access to protected resources.
- Monitor user activity: Watch activity and identify suspicious behavior to detect and respond to security incidents.
- Keep software up to date: Regularly update the SSO software, identity providers and applications with the latest security patches and upgrades.
- Secure data transmission: Ensure that all data transmitted between the SSO server and applications, or services is encrypted.
- Regularly audit access controls: Review and update access controls to ensure that only authorized users have access to protected resources.
