
What is SAML
SAML (Security Assertion Markup Language) is an XML based markup language used for authentication via identity federation. SAML is a ubiquitous protocol that is supported by various service provider applications such as Office 365, Salesforce, Webex, ADP, and Zoom.
SAML is used for federating identity between a service provider (e.g., Office 365) and an identity provider (e.g., Entrust Identity as a Service). When a user attempts to log in to the application directly or through a single sign-on (SSO) portal, authentication information is exchanged between the identity provider and service provider.
SSO eliminates the need for users to have to log in to various applications repeatedly. SAML enables SSO by facilitating information exchange between three parties: the user, the identity provider, and the service provider. The user is you, who has the right to access an application (service provider). The identity provider refers to the server that is in charge of authenticating the user and passing on user information to the service provider.
How does SAML work?
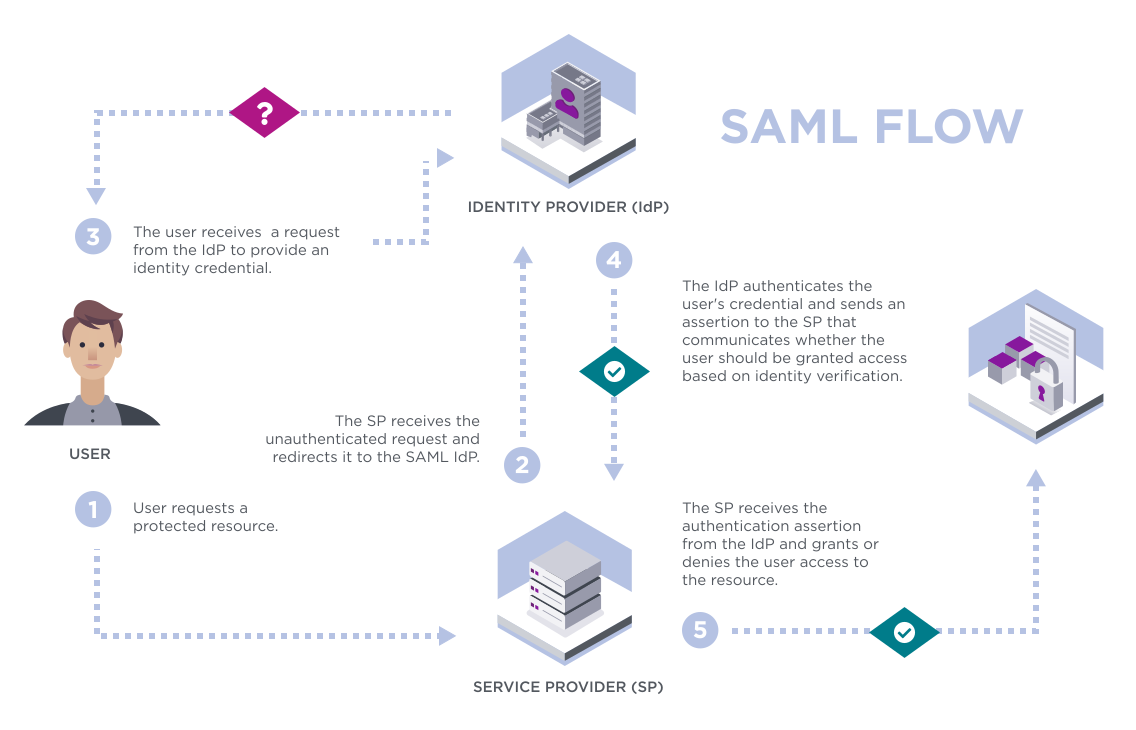
SAML specifies three components, or roles: the principal (e.g., a user), the identity provider (IdP), and the service provider (SP).
In the typical SAML use case, a principal will request a service from a service provider, which prompts the service provider to request and receive an authentication assertion from an identity provider. This assertion provided to the service provider is the basis upon which an access control decision is made either to perform or deny the service requested by the principal.
For example:
What's the difference between SAML, Open Authorization (OAuth), and OpenID Connect (OIDC)?
SAML is a widely applicable authentication protocol whereas OAuth is an authorization standard designed for use with specific applications, devices, or APIs to provide secure delegated access. One is used to authenticate a user and the other is used to authorize specific access.
OIDC is an authentication protocol built to specifically add a layer of security to OAuth 2.0. Using JSON web tokens (JWTs) to verify the identity of an end-user, it enables users to log in to multiple sites using one set of login credentials.
Although SAML and OAuth are both interoperable standards, their purposes vary greatly. SAML handles the function of granting access, whereas OAuth handles the function of determining what can and cannot be accessed.
What is the most current version of SAML?
SAML 2.0
How can Entrust help simplify identity and access management (IAM)?
Single Sign-On (SSO) is vital to any enterprise IAM strategy, as it increases workforce productivity by having one set of user credentials to securely access all systems and applications. Entrust Identity supports SSO so your users can access all applications with a single strong credential instead of managing credentials for each unique cloud, on-prem, and legacy application. Learn more about Entrust SSO.
