
How Does Passwordless Authentication Work?
What is passwordless authentication?
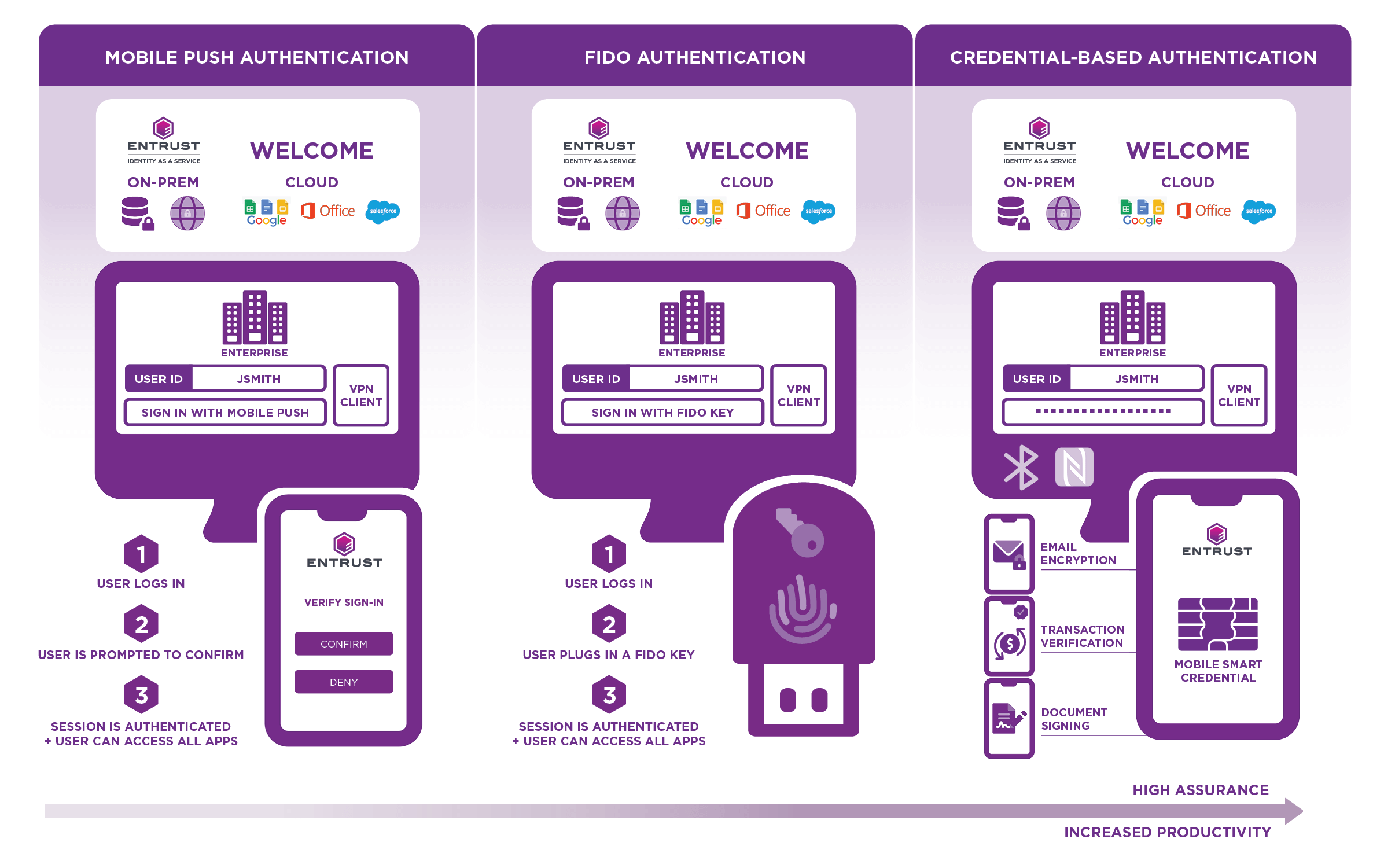
Simply, passwordless authentication provides an alternative form of authentication (i.e. biometrics) to the password to enable secure user access. However, a passwordless experience is not necessarily passwordless authentication. For example, mobile push authentication provides a passwordless experience to the user, but still relies on an underlying password.
True passwordless authentication removes the password altogether. For example, credential-based passwordless authentication replaces the password with a digital certificate. In this case, a digital certificate is provisioned onto the user's mobile device, transforming it into their trusted digital identity. When the device is unlocked with the user's biometrics (i.e. fingerprint or facial recognition) they are granted secure access when in close proximity of the connected system or application and logged out when they leave the vicinity. Since the user is authenticated by a PKI-based credential, they can use the same verified identity to send encrypted email, digitally sign documents, and encrypt files, which is not possible with FIDO keys. It also enables the user to log out of the connected system or application automatically.
The three common forms of passwordless solutions are summarized below.
What are the benefits of passwordless authentication?
Stronger security: Passwords are a vulnerable form of identity verification, responsible for 81% of security breaches. Passwordless methods rely on authenticators that are less susceptible to theft, such as biometric signatures and hardware tokens.
Better user experience: Passwords require increased security. Passwordless authentication provides that security without introducing unneeded friction and frustration. A truly passwordless solution creates a very high degree of user friendliness while also ensuring a high degree of security by relying completely on PKI credential-based authentication.
Reduced total cost of ownership (TCO): Passwords take time, money, and resources to manage. They require constant maintenance from IT. Removing the password eliminates these costs by relying on more efficient and secure authentication methods.
Is it easy to implement passwordless authentication?
Passwordless authentication is an investment in security that over time leads to many cost savings. Deployment costs can vary depending on the size of your organization's existing user directory and authentication mechanisms. The technology needed to adopt a passwordless authentication approach may already be used at your organization, or may require new technology purchases. It is also best to consult an expert before investing in your authentication solutions.
What makes Entrust's passwordless authentication different?
Unlike other solutions, the Entrust passwordless solution is truly passwordless – it really does remove the password altogether and enables users to send signed and encrypted emails, digitally sign documents, and encrypt files with a PKI-based credential.
How does Entrust passwordless authentication work?
There are no servers to manage or software to deploy. Simply use the Entrust cloud-based service to establish your policies and monitor activity on your networks.
- Install a smart credential on an employee’s mobile device to create a secure digital workforce identity.
- The worker unlocks the device with biometric authentication, such as fingerprint or facial recognition, to verify his or her identity.
- Once the worker is authenticated, Bluetooth® connectivity to his or her Mac or PC computer delivers passwordless single sign-on to all apps – cloud-based and on-premises – while in close proximity.
- When the worker walks away from their computer with their mobile device, he or she is automatically logged out of their workstation and signed out of any applications they were using.
