With the fight for the attention of digital consumers, it is crucial to provide a seamless, secure way for them to interact with your application or service. One of the most important aspects of this interaction is when a new user registers on your application and when they need to log in. Having a poor user experience during registration and login can cause a drop in conversion rate and deter users from engaging with your application. It’s important to provide a way for users to register and authenticate to your application in a quick, secure, and frictionless manner.
One way to enable a secure and painless way for users to log in to your application is through the use of social logins, where a user can register and sign into an application using an existing social account such as Google, Microsoft, Facebook, or LinkedIn. The advantage of using this approach is that the user doesn’t have to re-enter their information while registering and doesn’t have to create yet another username and password. In addition, using a social login provides a single sign-on (SSO) like experience, reducing password fatigue and compromised credentials resulting from weak passwords and password re-use on multiple websites.
As you can see, using social logins comes with a number of advantages for organizations: Offering a simplified registration and login process brings greater adoption of applications and conversion of users. Additionally, using social logins allows for use of profile and preference data that can be used to pre-configure and customize the in-app experience for a newly onboarded user.
How do social logins work?
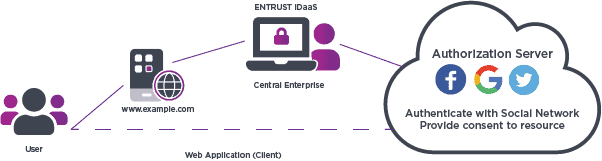
Social login is built using the OpenID Connect (OIDC) protocol that is built on top of OAuth2 and provides a single sign-on (SSO) like experience to customers using a consumer application. When a user visits the registration or login page of an application, they can click on a social login option that will then validate their identity and onboard the user by communicating with the social login provider.
User
Step 1. User visits application and gets redirected to the social network’s authorization page to authenticate themselves if not already signed in to their social network.
Step 2. Once user is authenticated with the social network, they will need to provide consent to the scopes (permissions) requested by the application if in the registration phase.
Step 3. User is redirected back to the application and is registered and logged in to the application.
Application
Step 1. The application will redirect the user to the social network’s authorization server with the requested scopes including the OpenID profile scope.
Step 2. Once the user has provided consent to the scopes, the social network redirects the request back to the application’s callback / redirect URI with an authorization code.
Step 3. The application then exchanges the authorization code for an access token and an ID token from the authorization server in the backend.
Step 4. The application then logs in the user with the information received from the social network.
By using the Entrust Identity as a Service platform, organizations need not build customized integrations for each social platform. Instead, organizations can use out-of-the-box social login integrations to get up and running quickly with support for social logins, increasing usability, and conversion rates for their users while improving security by providing a trusted single sign-on (SSO) experience.
Organizations can also use the generic OIDC connection to enable proxy IdP connections to other login providers in a seamless way with the Entrust IDaaS platform.
Learn more about the Entrust Identity as a Service (IDaaS) platform.



