How to install SSL/TLS certificates on Cisco appliance using CLI
Before you begin...
-
Never share private keys files.
-
If you plan on using the same certificate on multiple servers always transfer the private key using a secure method ( e-mail is not considered a secure method of transfer ).
-
It is best practice to ensure that you have current and up to date Ciphers and Protocols to ensure the best security when deploying a new Private key and Server Certificate.
-
Make sure you run the SSL/TLS Server Test at the end of the installation process to check your certificate configuration against SSL/TLS Best Practices.
-
For more information on SSL/TLS Best Practices, click here .
Pre-requirement:
Cisco Appliance with minimum IOS version 15.2(4) . Any version below this will not support SHA256 algorithm on SSL/TLS certificate.
This is a five part process:
1) Generate the keypair
2) Create the trustpoints
3) Generate CSR (Certificate Signing Request)
4) Obtain public signed SSL/TLS certificate
5) Import certificate to trustpoint
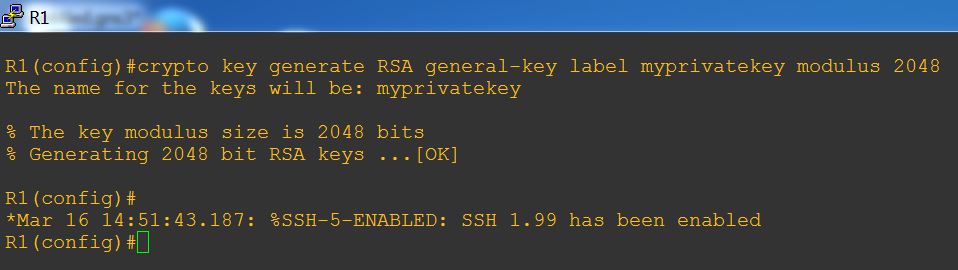
Part 1 of 5:Generate the keypair
Command:
crypto key generate rsa general-keys label myprivatekey exportable modulus 2048
Example:
Part 2 of 5: Create the trustpoints:
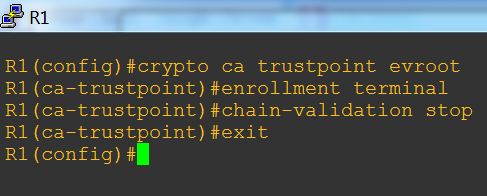
1. Create trustpoint for root certificate:
crypto ca trustpoint <yourtrustpointname>
Complete set of instructions are on the example below:
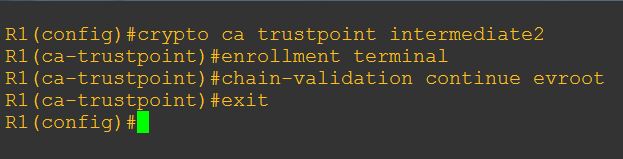
2. Create trustpoint for second intermediate certificate:
crypto ca trustpoint <yourtrustpointname>
Complete set of instructions are on the example below:
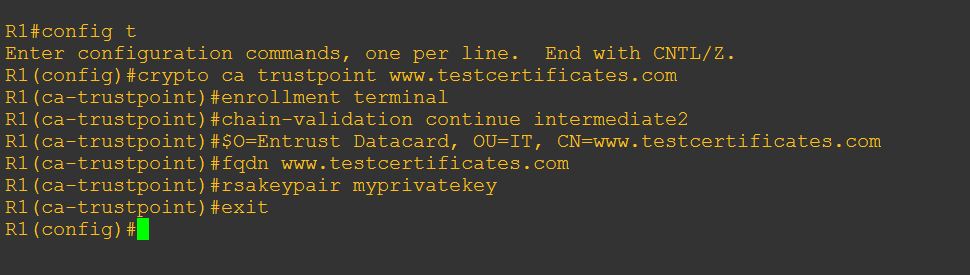
3. Create trustpoint for server certificate:
crypto ca trustpoint <yoursitename>
Complete set of instructions are on the example below:
Part 3 of 5: Generate CSR (Certificate Signing Request)
NOTES : The CSR can only be generated from the trustpoint that has already associated with private key. Normally this is a trustpoint that intended for importing server certificate.
Steps to generate CSR from server cert trustpoint:
crypto ca enroll <yoursitename>
Example Steps:
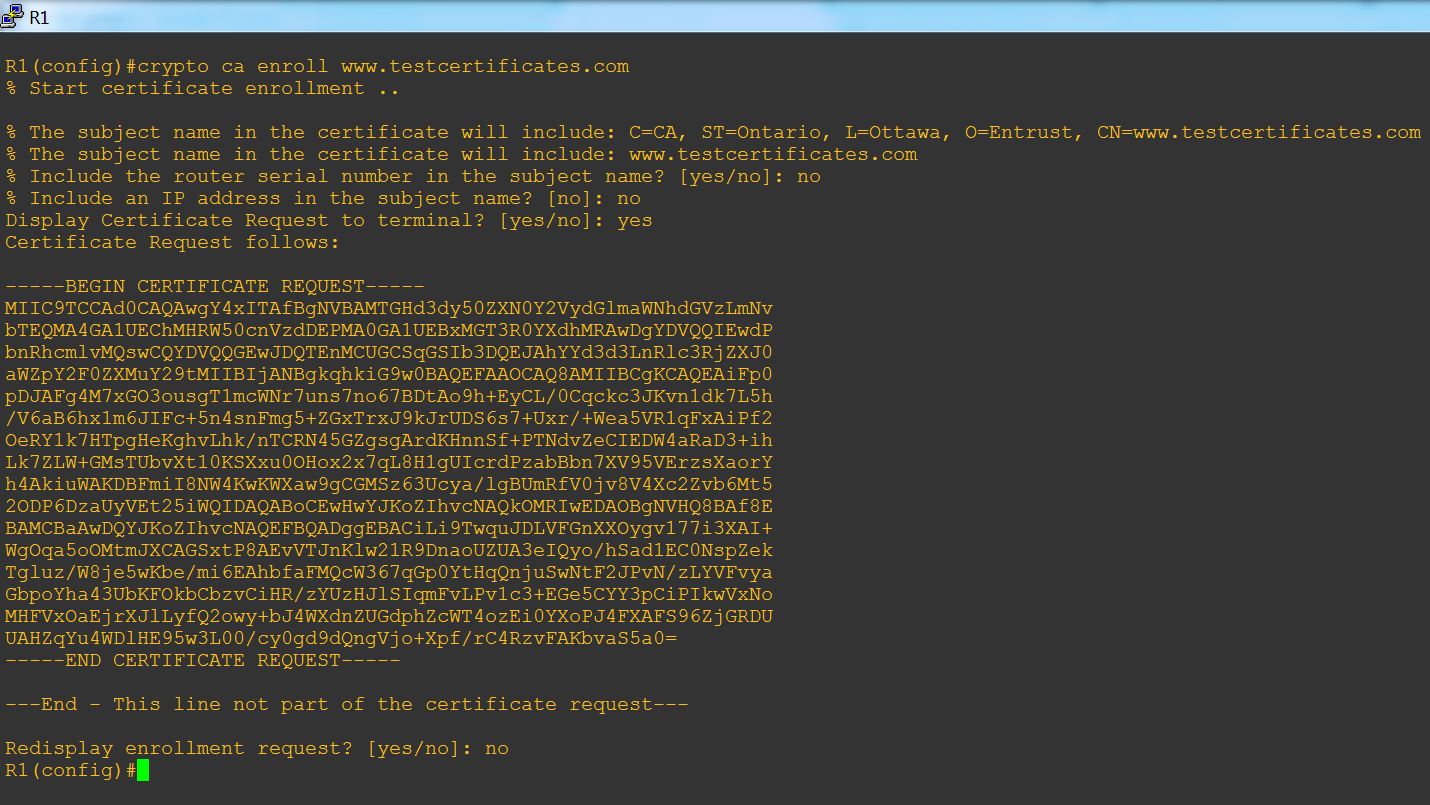
Copy your CSR and paste it to your text editor application such as Notepad. This is your CSR file that you need when issue or purchase an SSL/TLS certificate from Entrust Datacard.
Part 4 of 5: Obtain public signed SSL/TLS certificate
Login to Entrust Datacard certificate management portal or placing an order for SSL/TLS certificate to Entrust Datacard Online buy website using the CSR that being generated on the section C above.
Part 5 of 5: Import certificate to trustpoint
NOTE: Before you continue the steps below, you need to have all the certificates from Entrust Datacard ready by downloaded it from the certificate pickup link.
Steps to import certificate to trustpoints:
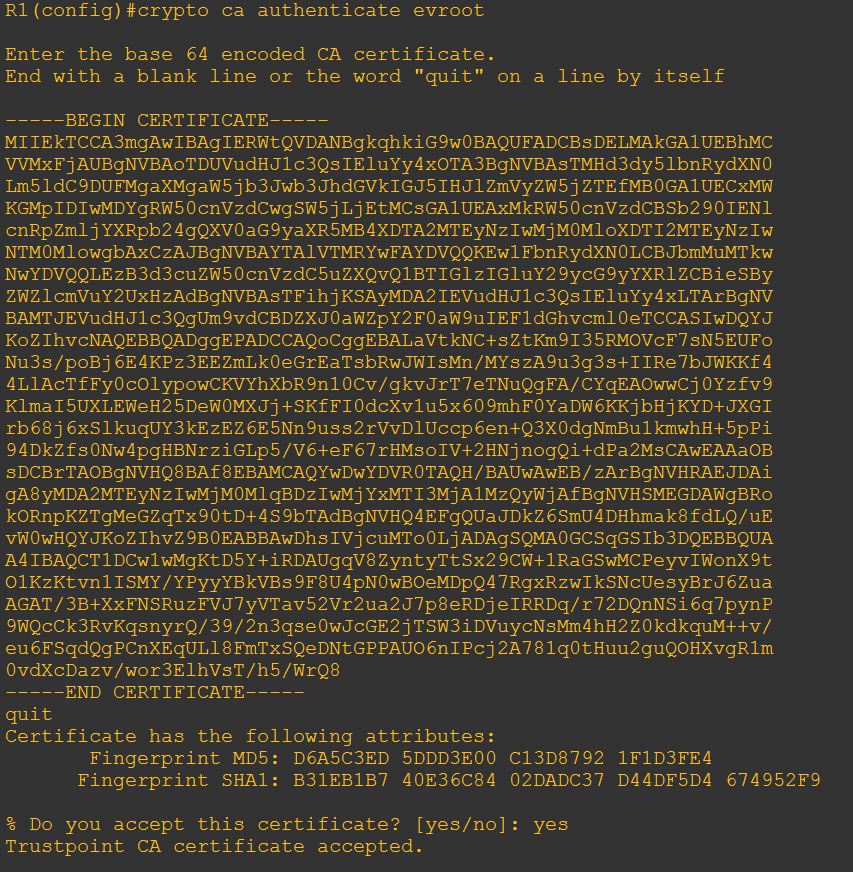
1. Import root certificate to root trustpoint.
- Open root.cer using text editor application such as Notepad and then copy all the content to clipboard (Ctrl-C).
- Run command below and paste the CSR:
crypto ca authenticate <trustpointname>
Example of the steps:
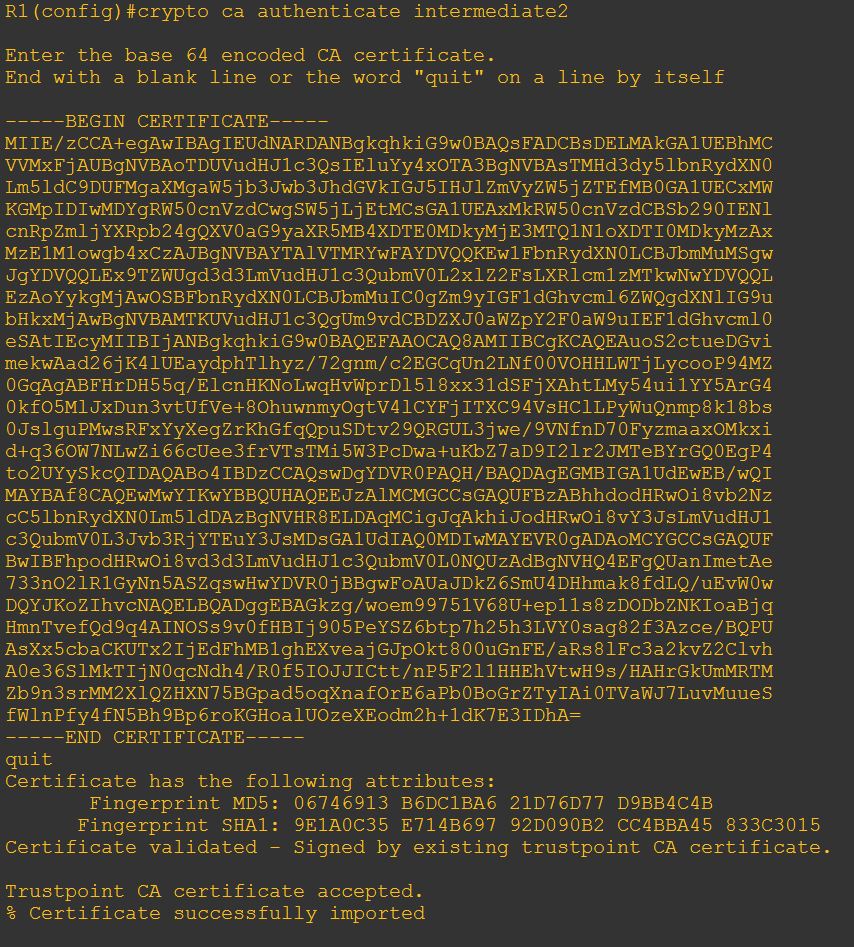
2. Import intermediate2 certificate to intermediate certificate trustpoint.
- Open intermediate2.cer using text editor application such as Notepad and then copy all the content to clipboard (Ctrl-C).
- Run command below and paste the CSR
crypto ca authenticate <trustpointname>
Example of the steps:
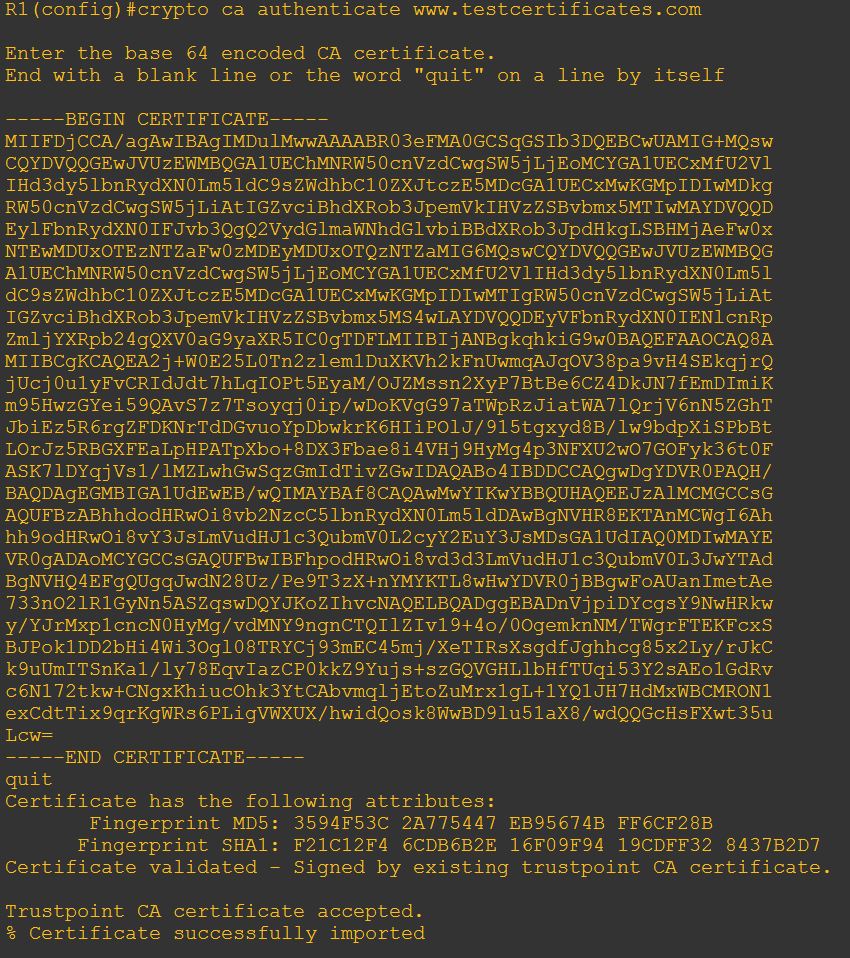
3. Import intermediate1 certificate to server certificate trustpoint.
- Open intermediate1.cer using text editor application such as Notepad and then copy all the content to clipboard (Ctrl-C).
- Run command below and paste the CSR
crypto ca authenticate <yoursitename>
Example of the steps:
If you have any questions or concerns please contact the Entrust Certificate Services Support department for further assistance:
Hours of Operation:
Sunday 8:00 PM ET to Friday 8:00 PM ET
North America (toll free): 1-866-267-9297
Outside North America: 1-613-270-2680 (or see the list below)
NOTE: Smart Phone users may use the 1-800 numbers shown in the table below.
Otherwise, it is very important that international callers dial the UITF format exactly as indicated. Do not dial an extra "1" before the "800" or your call will not be accepted as an UITF toll free call.
| Country | Number |
| Australia |
0011 - 800-3687-7863
1-800-767-513 |
| Austria | 00 - 800-3687-7863 |
| Belgium | 00 - 800-3687-7863 |
| Denmark | 00 - 800-3687-7863 |
| Finland |
990 - 800-3687-7863 (Telecom Finland)
00 - 800-3687-7863 (Finnet) |
| France | 00 - 800-3687-7863 |
| Germany | 00 - 800-3687-7863 |
| Hong Kong |
001 - 800-3687-7863 (Voice)
002 - 800-3687-7863 (Fax) |
| Ireland | 00 - 800-3687-7863 |
| Israel | 014 - 800-3687-7863 |
| Italy | 00 - 800-3687-7863 |
| Japan |
001 - 800-3687-7863 (KDD)
004 - 800-3687-7863 (ITJ) 0061 - 800-3687-7863 (IDC) |
| Korea |
001 - 800-3687-7863 (Korea Telecom)
002 - 800-3687-7863 (Dacom) |
| Malaysia | 00 - 800-3687-7863 |
| Netherlands | 00 - 800-3687-7863 |
| New Zealand |
00 - 800-3687-7863
0800-4413101 |
| Norway | 00 - 800-3687-7863 |
| Singapore | 001 - 800-3687-7863 |
| Spain | 00 - 800-3687-7863 |
| Sweden |
00 - 800-3687-7863 (Telia)
00 - 800-3687-7863 (Tele2) |
| Switzerland | 00 - 800-3687-7863 |
| Taiwan | 00 - 800-3687-7863 |
| United Kingdom |
00 - 800-3687-7863
0800 121 6078 +44 (0) 118 953 3088 |
