When it comes to Zero Trust, the conversation has moved from being a nebulous term several years ago to a well-understood framework with a true north that has broad acceptance across the cybersecurity industry.
That said, confusion abounds among C-suite executives and boards. If you walked around the exhibition at the 2023 RSA Conference, you could hear from a networking specialist that Zero Trust is all about IP, and then from an identity vendor that it’s all about credentials. Defining Zero Trust narrowly runs the risk of creating a false sense of security – if you just secure the network or the credentials, you’re done with the Zero Trust journey.
That’s why the recent release of the latest CISA Zero Trust Maturity Model in April 2023 provided a much-needed reference point for government agencies as well as enterprises on how to develop Zero Trust strategies. Zero Trust is broader than any one vendor’s solution. It is an approach that can govern user identity and access management (IAM), and access and security of devices, networks, application workloads, and data, with a risk-based access control model that can be implemented across an organization’s entire user base and IT stack.
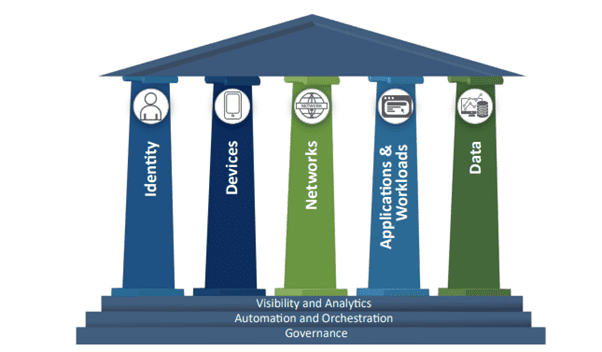
CISA’s Zero Trust Maturity Model Pillars
When we talk to our customers, we talk about Zero Trust foundations. Regardless of which vendors you choose, Zero Trust is a journey, one that you can track along the maturity model. This includes making sure you’re securing the network and credentials – for humans, machines, and applications. In today’s post-perimeter environment, it means implementing dynamic authentication that is verified rather than assumed and secures your data assets with encryption and key management best practices, and ensuring development code is signed and approved.
In fact, that last item is a great case in point when it comes to these potential Zero Trust blind spots that arise when you don’t think holistically. When developing applications, code is brought in via APIs, libraries, and repositories and analysis shows us that as much of 70% of an organization’s code is assembled rather than written. An application deployed within an organization and the software bill of materials that make them up aren’t always thought of when it comes to Zero Trust planning, but they absolutely should be. How you certify code that comes from outside your organization and the risk profile you apply to it should be part of that framework.
Ultimately the shift in thinking boils down to moving from the idea of trust to verification. So instead of trusted identities and applications we have verified identities and applications. The second part of that shift is the delta, the change over time, which means we don’t just verify once, but continuously. This is change that can be measured over time, geography, and access entitlement and that is aligned with the risk profile for any given user, machine, or application.
This approach is a reflection of the Zero Trust maturity model, which has gained significant attention from cybersecurity professionals and organizations alike. For most organizations, the current state of Zero Trust maturity is still in its early stages.
We recognize that implementing a Zero Trust security model requires a significant investment of time and resources. It involves assessing the current state of security controls and infrastructure, identifying gaps and weaknesses, and developing a plan to address those gaps. While many have a long way to go before they can claim to have a fully mature Zero Trust security posture, there are excellent resources available to help map out that journey, as well as partners like Entrust that can offer the guidance and broad portfolio needed to get there.



