Chocolate or vanilla is a familiar question we are often asked. Whether its cake, ice cream, or some other sweet, we all have our preference, and many times the answer is both! The same is the case with cryptography, there is symmetric and asymmetric encryption, and their combination makes for powerful cybersecurity solutions. Although we might not be aware, symmetric and asymmetric encryption is everywhere, whether we are tapping our card at a payment terminal or making an online purchase, these two processes are often carried out in the background. If you are responsible for the security of your company’s systems or are a consumer curious about how sensitive data and transactions are protected, I’ll try and give you some straightforward insight into the cryptography that secures our daily lives. In this blog, I will go back to basics and define the two encryption methods, compare their features, and offer examples to further illustrate their use in everyday applications.
Back to basics
Cryptography is the science of protecting the confidentiality, integrity, and availability of data, to ensure that it can only be read and used by authorized parties and cannot be altered. Like many other inventions, cryptography had its origins in warfare, and can be traced back to the ancient Greeks. Methods by which data is masked or hidden from plain view include transposition and substitution of characters using a cipher or an algorithm that defines the steps needed to be taken to code, and later decode, the operations. To protect the confidentiality of data, encryption is used. Simply put, encryption works much like a lock, and you need a key (or multiple keys) to encrypt and decrypt the data. Protecting the integrity of information is also very important. To ensure data cannot be altered, signing and hashing mechanisms are employed.
What is encryption?
Encryption is the process of taking data that can be easily read by anyone, what is commonly called “plain text,” and transforming it to “cipher text” that can only be read by those recipients that hold the right cryptographic key. There are two ways of doing this – symmetric encryption that uses a single key to encrypt and decrypt, and asymmetric encryption that uses two different keys, one to encrypt and another one to decrypt.
What is symmetric encryption?
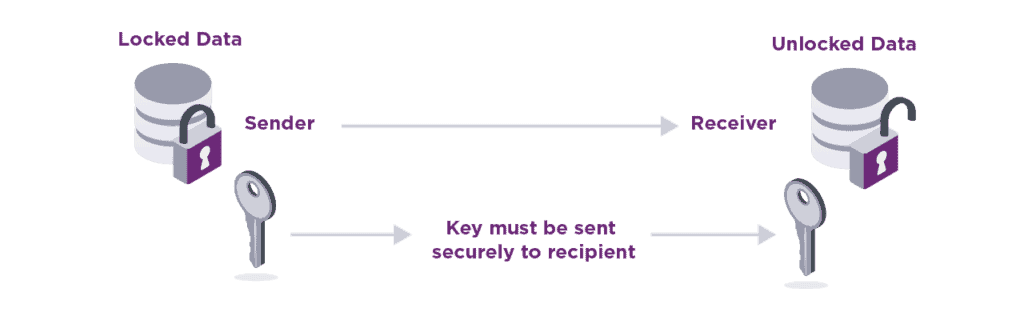
Symmetric encryption is the process of protecting data using a single cryptographic key. The same key used to encrypt the data is also used to decrypt the data. Think of it as your traditional lock in your home. You lock the door with your key, and you unlock it with the same key. To protect your belongings, you need to protect your key. If you want others to have access to your home, you must make and distribute copies of the key. Figure 1 describes how symmetric encryption protects the exchange of data between parties.
Figure 1: Symmetric encryption.
Sender locks data with key and receiver uses same key to unlock data.
What is asymmetric encryption?
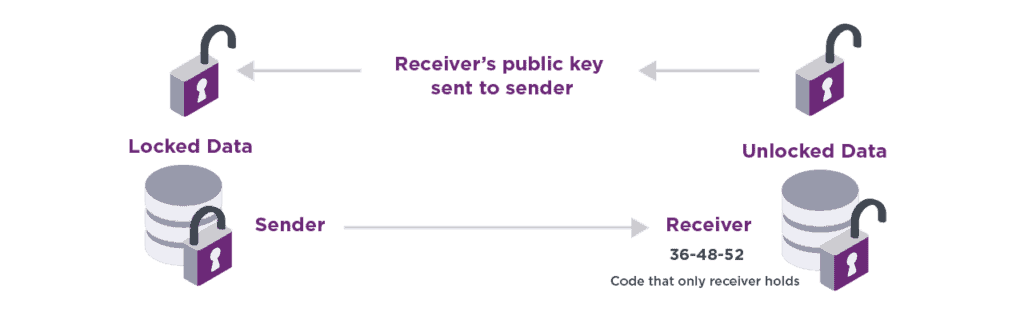
Asymmetric encryption uses two keys, one key is used to lock, and a different key is used to unlock. The key used to lock your data can be made available to anyone; in fact, we call it the “public key.” The key you use to unlock the data is held only by you and must always be protected. We aptly call this key the “private key.” To illustrate this, I like to use the analogy of an open combination lock. You can give this open combination lock to anyone who needs to send you data securely. They can use it to lock your data, but since you (and only you) have the code or combination, you are the only one that can open the data and convert it back to plain text. Figure 2 describes how asymmetric encryption works using this analogy.
Figure 2: Asymmetric encryption.
Sender requests a public key (open combination lock) from receiver to use to lock the data to send. Receiver uses the private key (code or combination that only she/he knows) to open the lock and access the data.
What is signing and hashing?
In cryptography, signing and hashing are mechanisms used to validate the authenticity of identities and data, and to prevent alteration. Signing is typically done using a private key that only the entity authorizing a document or transaction has possession. Like signing a paper check or contract, the signing individual puts down a mark that can only be attributed to that individual. To validate that the data or transaction has not been altered between the time it leaves the sender and arrives at the recipient, hashing is used to encrypt a piece of the data with the private key. Using the associated public key, the decrypted data is compared to the rest of the data. If it matches, integrity has been preserved.
What are some examples of symmetric and asymmetric ciphers or algorithms?
Common symmetric ciphers include the old Data Encryption Standard (DES) and 3DES, and the newer Advanced Encryption Standard (AES) and Rivest Code (RC5) algorithms.
Common asymmetric algorithms include the Rivest Shamir Adleman (RSA) and Elliptic Curve Cryptography (ECC) ciphers.
How do symmetric and asymmetric encryption compare?
Symmetric encryption is simpler and faster. It can be quickly executed by the sender without having to request anything from the receiver, and there is only one key that needs to be distributed. However, because the key that needs to be distributed to the recipient is the one that unlocks the data, it must always be protected, and therefore a parallel and secure distribution method for keys must be in place.
Asymmetric encryption on the other hand is slower because of the more complex procedure and requirement to obtain the public key (open lock) from the recipient, before initiating the process. However, because the encryption key is public, there is no need to secure it, and can be posted for anyone to use. This makes for a significant advantage in contrast to its slower performance.
Best of both worlds
Many encryption processes used today to secure transactions and data, employ a combination of both symmetric and asymmetric encryption. In doing so, they take advantage of the benefits of each of these methods. Transactions are typically initiated using asymmetric encryption so there is no need to distribute a key. The public key is used to start and establish a secure session. Once the initial session is established and a secured tunnel is in place, symmetric keys can then be exchanged through that protected channel, and the rest of the transaction or transactions can then be performed more rapidly to achieve high performance.
Where is symmetric and asymmetric encryption used?
Symmetric and asymmetric encryption is extensively used in eCommerce, Cloud Computing, and in the fast-growing Internet of Things (IoT) among other applications. eCommerce is perhaps one of the more mature areas of applications. To establish trust among parties in the virtual/online world, users, which can be real-life people or machines, need to be given identities that can be verified. Public Key Infrastructures (PKIs) form the foundational building blocks that issue and manage digital identities. PKIs include the hardware, software, procedures, and processes needed to identify users and validate their identities to ensure secure transactions. Transport Layer Security (TLS), which is still commonly referred to by its predecessor’s name, Secure Socket Layer (SSL), has been around for decades and uses certificates (public keys) to authenticate users and establish Secured Hyper Text Transfer Protocol (HTTPS) transactions that we commonly use when buying things on-line.
Way forward
Offering a one-stop shop for solutions, and the expertise to be your trusted advisor, Entrust enables digital transformation by securing payments, identities, data, and infrastructure. To learn more about cryptography and digital security, visit our PKI and Hardware Security Module FAQ sites. To learn more about how Entrust can help you securely transform your business, visit our Digital Security Solutions page.



