
Secure Data
Support your Zero Trust journey by securing the cryptographic keys and secrets that protect your most sensitive organizational data.

Data Security and Encryption
Zero Trust requires that all sensitive data be rendered unreadable through encryption while in storage, use, and transit and that it is only accessible to explicitly authenticated users or entities.
Key Features
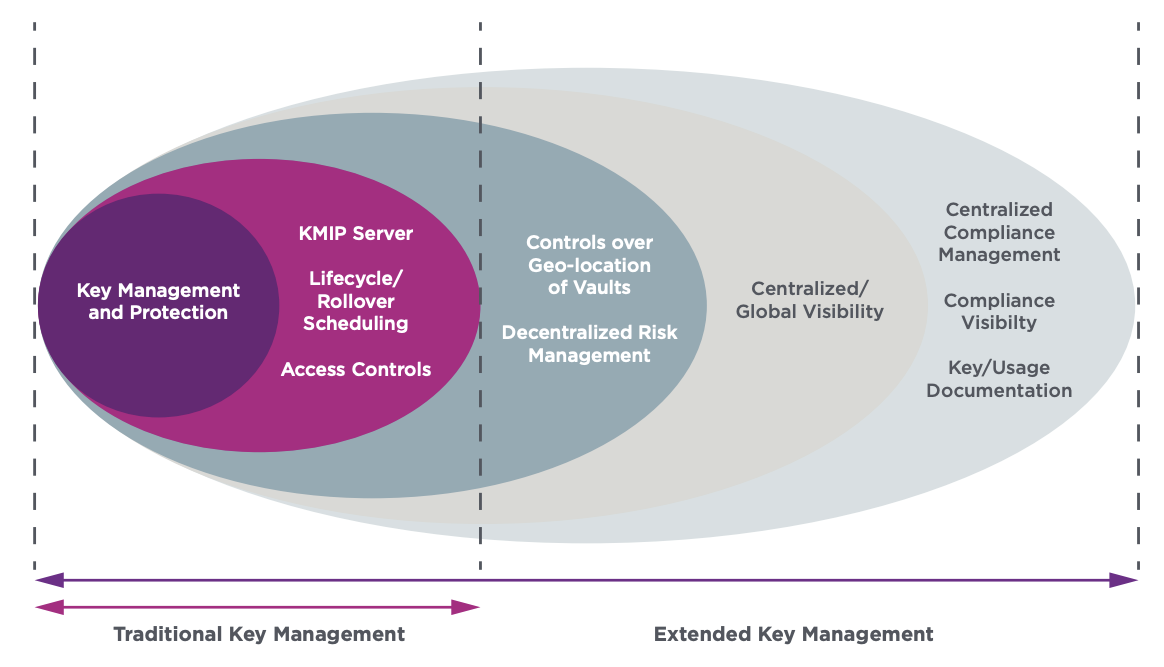
Traditional Key Lifecycle Management
Generate, deliver, and distribute cryptographic keys to a range of supported applications through multiple standard interfaces including KMIP. Provide access control to keys and enable automated capabilities including key rotation and key expiration.

Secure Root of Trust
Foundational element of the data protection pillar of the Zero Trust framework enables FIPS-certified high assurance secure cryptographic key generation and lifecycle management with dual-controls and separation of duties.

Decentralized Vault-Based Architecture
Distributed key storage ensures that keys and data are kept within the geographical areas where they are supposed to be maintained to facilitate compliance with geo-fencing and data sovereignly regulations.

Comprehensive Central Policy
Unified visibility across cryptographic assets regardless of the number of vaults deployed across the distributed environment.

Compliance Management Dashboard
Enables the documentation of keys and secrets based on templates for continuous compliance assessment using built-in or custom policies.

Secure Data Solution Brief
The Entrust centralized-decentralized security (CeDeSec) approach enables organizations to maintain full control of their data, ensuring the confidentiality and integrity of and controlled access to critical assets while facilitating compliance with security regulations.
