
Identity and Access Management
Entrust Identity
Our intelligent IAM platform lets you implement a Zero Trust approach, providing user authentication, authorization, and access control to the right resources anytime anywhere.
A Single Unified IAM Portfolio
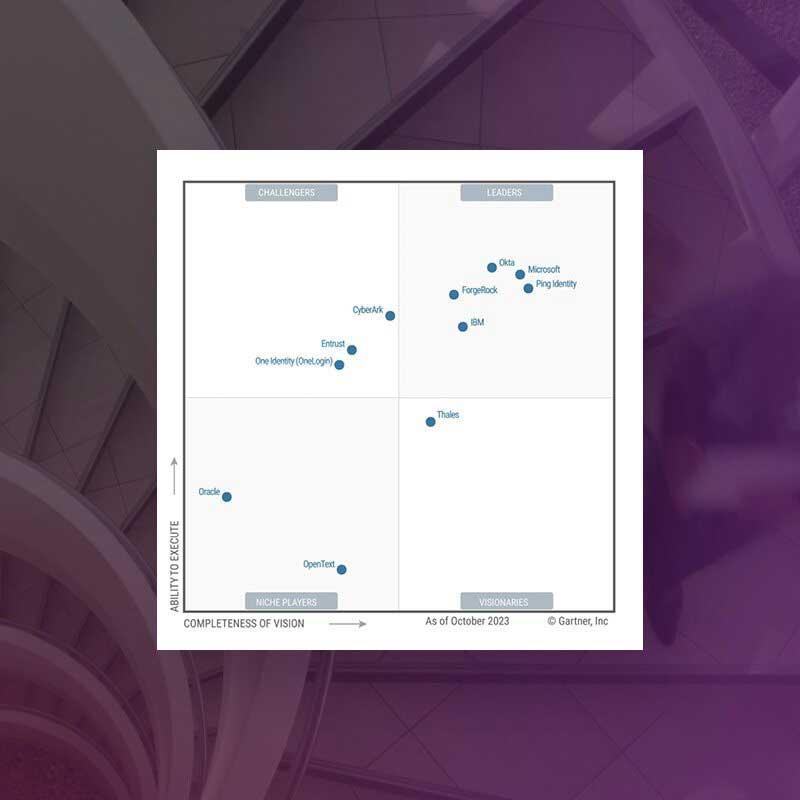
Explore the Entrust IDaaS platform, recently named a Challenger in the 2023 Gartner® Magic Quadrant™ for Access Management, and experience the benefits of an industry-leading identity and access management solution.
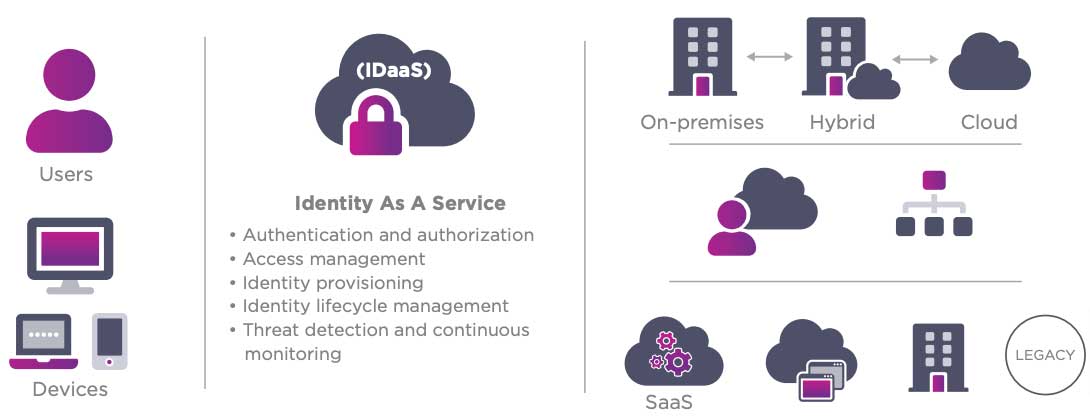
Identity as a Service (IDaaS)
All of your users. Endless possibilities in the cloud. Our intelligent IAM platform lets you implement a Zero Trust approach, providing user authentication, authorization, and access control to the right resources anytime anywhere.
Secure across the enterprise
With Entrust Identity, all of our customers, alliance and channel partners gain access to our complete authentication portfolio protecting the identities of workers, consumers, and citizens to ensure secure access and communications.
More features and accelerated roadmap
By integrating our authentication portfolio, customers and channel partners have access to a breadth of authenticators, use cases, and deployment options that is unparalleled in the market today.
Mobile first platform
We are unifying our single purpose mobile apps into one modern app for the Entrust Identity portfolio that serves both iOS and Android devices. This also applies to our mobile Software Developer Kit which is used by many customers. As well, as customers augment and evolve their authentication solution, including moving from on-premises to the cloud, there is no longer the need to change out the mobile app.
Scalable
One unified identity portfolio means organizations can get started with what they need today and grow how and when they need, without having to swap out one product for another. Entrust Identity supports an unprecedented number of IAM use cases for workforce, consumer, and citizen user communities ranging in size from 50 to more than 10 million.
Benefits of a Comprehensive IAM Suite
Deployment Flexibility & Broad Capabilities
Effortlessly integrates with leading innovative solutions for unparalleled flexibility, enhancing ROI and optimizing workflows with versatile cloud or on-prem options.
Zero Trust Framework
Rapidly deploys secure, intuitive user experiences within a comprehensive Zero Trust framework, significantly enhancing operational efficiency by optimizing IT asset use.
Simplified & Secure Usability
Seamlessly merges cost efficiency with robust security, speeding up widespread adoption of passwordless and other advanced security technologies.
Robust Security with SSO and MFA
Delivers trustworthy, reliable security with advanced MFA and SSO capabilities, ensuring seamless operations while effectively preventing security breaches.
Enhanced User Experience
Provides secure, effortless, and intuitive access through flexible deployment options, incorporating MFA and adaptive authentication to improve consumer engagement.
Comprehensive IAM Coverage
Offers an extensive suite of IAM solutions, including advanced MFA and passwordless authentication, catering to a broad and diverse range of security and access needs.
Securing Your Largest Attack Vectors: Identity
Learn more about common identity-based cyberattacks and how to protect your organization against them.
The identity portfolio suited to your authentication needs
Consumer
Consumer Banking
Attract and retain customers with best-in-class mobile and online banking services.
Customer Portals
Give customers frictionless access to your portals—and build a great brand experience.
CIAM Integration
Our portfolio integrates seamlessly with your Customer Identity Access Management (CIAM) strategies.
Meet PSD2 Regulations
We have the trusted identity tools you need to help you be successful and in compliance.
Workforce
Physical/Logical Access
Our portfolio offers the necessary technologies to integrate physical and logical secure access.
Privileged Worker
Protect the critical application credentials of system administrators or senior leaders.
Passwordless Login
Get a true passwordless SSO solution that supports all devices, PCs and Macs, and cloud and on-premises apps.
Enable PIV Compliant Government Mobility
Remove complexity and enable highly secure mobility with proven PIV solutions.
Citizen
Digital Citizen
Use our portfolio to secure and manage passports, national ID's and driver's licenses.
Explore Our Identity Portfolio Capabilities
Entrust’s Identity portfolio helps you streamline onboarding, ensure strong security and exceptional user experiences, and continuously protect your systems against advanced threats.
Entrust Named a Challenger for Access Management
Gartner has named Entrust a Challenger in the 2023 Gartner® Magic QuadrantTM for Access Management, recognizing our ability to execute and completeness of vision.
Customer Success Stories
Whether you're interested in one of our flexible-deployment PKI solutions or want to explore your options for securely printing and issuing payment cards straight from your bank, see why thousands of customers trust Entrust secure identity products.
Entrust helps Banco Bice comply with SBIF security regulations
With digital transformation on the rise, security has never been so important, and financial institutions around the world have to find the right balance between usability and security.
Evangelische Gesellschaft makes secure remote work possible for 1,000 employees
Within the shortest possible time, remote network access for 1,000 employees was to be secured using multi-factor authentication and integrated with the existing Citrix infrastructure.
IAM Resources
Securing Your Largest Attack Vector: Identity
Learn more about common identity-based cyberattacks and how to protect your organization against them.
Entrust helps Banco Bice comply with SBIF security regulations
Financial institutions around the world must find the right balance between usability and security.
Egangelische Gesellschaft makes secure remote work possible for 1,000 employees
Remote network access was secured within the shortest possible time.
Enable your organization to implement PDS2
Learn what PSD2 is, what is means, and how can you use it to your advantage.



