The oldest known example of hardened and tempered metal was a pick-axe found in Galilee dating back to 1200 B.C.. The forging process was used throughout the ancient world by skillful blacksmiths to develop tools, armor, and weapons. The process hasn’t changed much over the centuries; the steel is hardened when it is heated in a forge and then quenched followed by tempering, reheating the steel and allowing it to cool slowly. The quenching results in the formation of martensite, a very hard form of steel crystalline structure that gives it strength, and subsequent tempering reduces the brittleness of the material. I recently got to thinking how hardening metals used for weapons is really no different than hardening modern software environments for the cyber battlefield.
While no blacksmiths are involved, skilled IT security and administration professionals are essential in the environmental hardening process. Modern containerized applications are very much the go-to approach for software architects and developers, and hardening in this context relates to the locking down of the associated environment to minimize attack surfaces. At the same time staff are carefully steered through their software-related tasks to enforce consistent policies and practices and prevent misconfigurations that may lead to unwanted outages and service disruption.
In case you’re unfamiliar, a container is a runtime environment containing a software package and all its dependencies. Container images are standalone collections of executable code and content with popular vendors including Mirantis Kubernetes Engine, Red Hat OpenShift, VMware Tanzu, and Amazon EKS.
The development of containerized software follows the typical development lifecycle process. I’ve illustrated it in figure 1 below to reflect the nuances of the containerized development process:
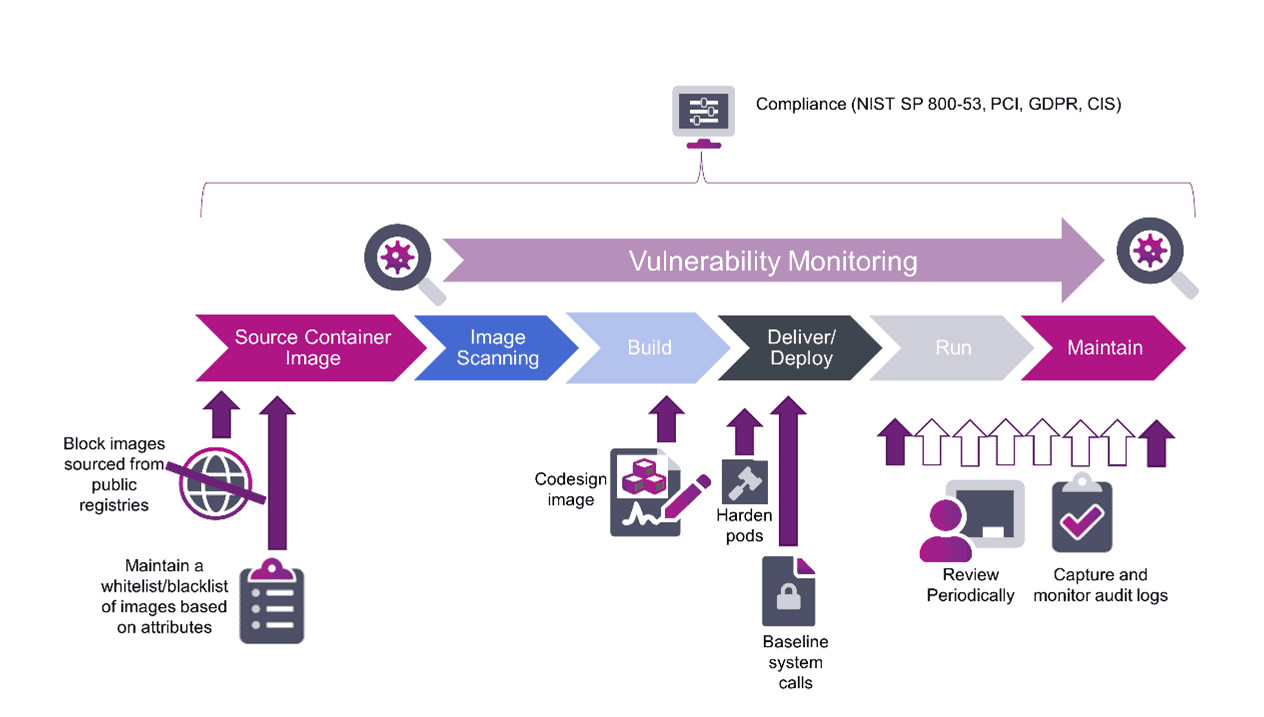
Figure 1: Container lifecycle process
For container environments, sourcing third-party image files is common practice. There are numerous public repositories available on the internet offering a huge range of containerized applications. Some of these are verified and come with a welcome seal of approval from a reputable source; however there are many container images posted by developers who are happy to share their efforts and others created by nefarious actors who upload containerized content with hidden malware and trojan payloads. And that is just the start of the development process. There are a lot more attack vectors to contend with as the container image is rolled into the DevOps/DevSecOps process. I’ve written a white paper, Hardening Your Container Ecosystem, which digs into this area and considers the threats and tactics used by nefarious actors specifically in the containerized ecosystems. In the white paper I discuss some of the tactics used by hackers identified in MITRE ATT&CK and then consider each phase of the container lifecycle and the best practice methods available to mitigate these threats. I touch on Entrust CloudControl and some of the other products from the Entrust portfolio that can help mitigate threats and keep the bad actors at bay.
Back to the front lines. In the past, the strength, resilience, and cutting abilities of the hardened and tempered steel weapons often defined the mettle (no pun intended) of those going into battle. Today it is about arming the IT security professionals with the right tools to harden their environment and defend against the nefarious bad actors and innocent misconfigurations by staff.
Why not download the white paper to read a bit more and see how Entrust can help your organization strengthen its defenses and rebuff the marauding invaders?



