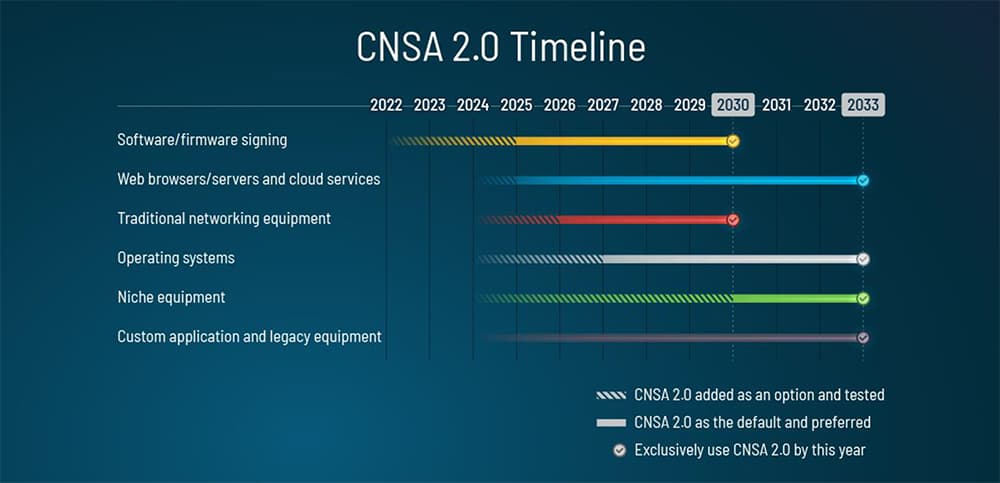
Just last month, the National Security Agency (NSA) announced the release of the “Commercial National Security Algorithm Suite 2.0.” The purpose of the document is to notify and guide National Security Systems (NSS) owners, operators, and vendors of PQ requirements as it relates to “networks that contain classified information or are otherwise critical to military and intelligence activities.” It also set out some timing parameters to begin this transition. So, when does their timeline start? They identified the first area to be addressed is software and firmware signing, and that that transition should begin immediately.
But this should come as no surprise. We’ve very much been of the position that the time to prepare for post-quantum is now. There is a consensus that within the decade, there will be a quantum computer powerful enough to disrupt cryptography as we know it. Additionally, we know that transition is not just another crypto refresh cycle. The migration to quantum-safe algorithms is much more involved and will span several years.
The reason the NSA is looking at this and setting such aggressive timelines is because of the data they know needs to be secured. Government agencies – as well as other industries such as financial services and healthcare – have long-life data (sensitive data that needs to live and remain confidential for 10+ years) that needs to be protected with quantum-resistant cryptography today, so that it remains secure during the lifetime of the data.
But the need to prepare isn’t exclusive to the government. All organizations should be taking steps to prepare, including:
1 – Inventory Data
- Once again, it’s important to understand where your valuable and/or long-life data resides, as well as the related data flows. Once you have that catalog and inventory, then you know where to start where your highest concerns are.
2 – Inventory Cryptographic Assets
- Some organizations already struggle knowing what cryptographic assets reside in their environment and having full visibility into this is key when creating a post-quantum readiness plan. In addition to visibility, it’s also important to ensure compliance, control, and automation of these assets.
3 – Build a Cryptographic Agility Strategy and Roadmap
- Cryptographic agility will be critical for the PQ transition. Crypto agility is the ability to easily move from one algorithm to another – such as a PQ one. And given that these are not a mature set of algorithms, being agile even after the PQ transition will also be key. It’s also important for organizations to identify areas of risk relating to cryptography including process, people, and technology. Entrust has a Crypto Agility Maturity Assessment that does all this. It also includes the development of a prioritized roadmap of remediation and increased agility in line with the NIST/DHS PQ reference model.
4 – Test and Plan the Migration
- All eyes are on the NIST PQ Competition to determine the recommended algorithms that are PQ safe, but in the meantime, round 3 finalist algorithms have been announced and testing can begin. For example, the Entrust PKIaaS PQ supports all 3 algorithms and allows organizations to begin testing these certificate types within their applications.
While the timelines are fuzzy, the takeaway is clear: The time to prepare for PQ is now – from creating a PQ-readiness team to building out a PQ strategy and roadmap.
For more information on post-quantum preparedness, see our resource page.



