Fall has arrived in the US northeast, and with it comes beautiful foliage, pumpkin spice lattes, apple crisp, cool nights and moderate days – what’s not to love! Another sign of fall is the arrival of the annual Global PKI and IoT Trends Study from the Ponemon Institute – now in its 5th year. And although hard pressed to match the visceral appeal of the other fall arrivals, it is nonetheless a barometer for the impact of this underappreciated and critically important technology.
Like the foundation of a house, PKI technology, processes and personnel are the bedrock of IT security – and their impact continues to expand. As this study hits the streets, I wanted to take a couple minutes and highlight some of the most interesting findings, and how they can help guide your forward PKI strategy.
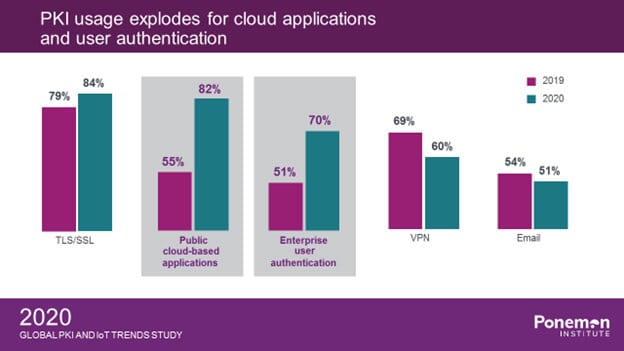
The headline of this research is undoubtedly a significant spike in the use of PKI credentials for two specific use cases: public cloud-based applications and enterprise user authentication. In a survey of this size (almost 2000 respondents from 17 countries/regions), it is rare to see year-over-year changes of 10% or higher. These two use cases left even that number way in the dust, with PKI use for public cloud applications growing 27% over 2019, and use for enterprise user authentication growing 19% over 2019. On top of that, consider that the research was performed just before COVID-19 took hold. We all know how secure remote access has never been more important as the WFH era moved to the forefront.
Another finding of the study that is particularly striking is the challenges that organizations face in enabling their applications to use PKI. The number one challenge to enabling PKI to support those applications is that responsible teams lack the knowledge and visibility to the security capabilities of the PKI. Think about this for a minute: enterprises are rapidly increasing their PKI use for their most important applications, while still not fully understanding if the PKI is fit for the purpose from a security perspective. Certainly a tenuous position from a risk management standpoint. It’s hard to rework the foundation once you’ve built the house.
PKI has long been a stalwart application in the on-premise data center. This year’s survey found that PKI is making its wayto the cloud While on-premise, internal certificate authorities (CAs) remain the top deployment model for PKI, particularly among the most security-conscious industries, organizations are increasingly augmenting them with external CA-managed services. And when you look at the knowledge and visibility challenge described above, you start to see the reason: Lacking internal expertise, enterprises are turning to reputable certified external CA services providers as a fast path to PKI security best practices. More robust choices are available than ever before, and given the complexity of security challenges, the “to do it right, I have to do it myself” adage is becoming a thing of the past.
The Ponemon study also looks into IoT applications, the fastest growing trend driving PKI deployment. Although there is evidence suggesting that IoT projects slowed this year due to disruption from COVID-19, two notable trends emerged. One is that discovery of connected devices has shifted to be the most important IoT security capability in 2020. That’s a good sign of embracing the fundamentals – you can’t secure or manage it if you don’t know it’s there. And time has proven over and over that even the most innocuous connected device like a coffee pot can be your downfall – with the attacker using it simply as a network entry point while going after more lucrative resources.
The other more ominous finding related to IoT is that many simply aren’t prioritizing security mechanisms that address their top threats. Respondents indicate that the top IoT threat is altering the function of a device (for example, by loading malware), but bewilderingly, rank secure delivery of patches and updates to IoT devices – the mechanism that directly addresses that threat – dead last when ranking important IoT security capabilities. Another sign of the still-developing IoT security landscape.
There are positive signs as well. Organizations are putting high value on Common Criteria and FIPS evaluation for their PKI. Hardware security module (HSM) use remains strong for the most important components of a PKI: the root CA and online issuing CAs. More are using multi-factor authentication for PKI administrators, and the highly vulnerable password-only protected PKI is becoming increasingly scarce. It does look like there are some challenges brewing with certificate revocation, which is notable particularly with the large rise in overall certificate volumes seen in the study (43% higher in 2020 than 2019). There is no doubt that certificate lifecycle management including revocation is, and will be, a critical capability for years to come.
The 2020 Global PKI and IoT Trends Study is full of additional detail, including some revealing splits about encryption trends by country and by industry. To download the study, click here. Questions or comments? You can find me on Twitter @johnrgrimm



