Can you remember the halcyon days of the video game arcades? This will probably date me, but I have fond memories entering the magical world of a gaming arcade while in first year at university. When the odd early morning Control Systems or Principles of Electricity lecture didn’t sound too compelling, I’d skip class and head to the local arcade with my friends for an hour or two of Defender, Tempest, Frogger, Space Invaders, or Pac-Man.
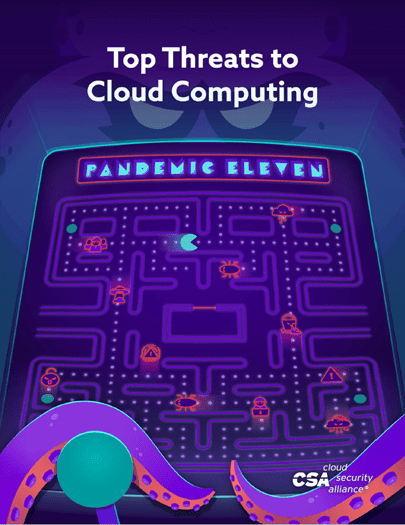
I was briefly reminded of the arcade gaming world when I came across a recent publication by the Cloud Security Alliance (CSA): Top Threats to Cloud Computing – Pandemic Eleven. The paper discusses cloud security themes and considers a range of cloud-related threats for practitioners and those planning migration to the cloud. As you can see from the front cover illustration above, they have designed the artwork inspired by the Pac-Man maze user interface with the 11 threats replacing the traditional Pac-Man ghosts.
The 11 issues are based on feedback from 700 industry experts who identified these, listed in priority as the top issues in their cloud environments. Each of the 11 topics are discussed briefly before considering the business impact, offering key takeaways and then anecdotes and real examples of exploits and exfiltrations to illustrate what has and can happen if you don’t protect against these threats. Each threat is also cross-referenced to other CSA resources such as their Security Guidance document and Cloud Controls Matrix (CCM) template spreadsheet. Useful for any cloud practitioners looking to tighten up their cloud environment.
The 11 threats outlined in the report are as follows:
| Threat | Consequence | |
| 1 | Insufficient Identity, Credentials, Access, and Key Management | Emphasizing the risk of privileged accounts and the need for least privileged access. |
| 2 | Insecure Interfaces and APIs | Stressing the need for APIs and microservices to be checked for vulnerabilities due to misconfiguration, poor coding practices, a lack of authentication, and inappropriate authorization. |
| 3 | Misconfiguration and Inadequate Change Control | Recognizing that both malicious and inadvertent mistakes can have a detrimental impact to an organization’s applications and infrastructure resulting in outages. |
| 4 | Lack of Cloud Security Architecture and Strategy | Emphasizing that “strategy should precede and dictate design” while recognizing the agile, incremental approach to planning. |
| 5 | Insecure Software Development | Threat actors can leverage the complexity of software to carry out exploits in the cloud. Log4j gets a mention here. |
| 6 | Unsecured Third-Party Resources | Stressing the importance of verifying the provenance and integrity of your supply chain. |
| 7 | System Vulnerabilities | Considers system vulnerabilities such as zero-day vulnerabilities, missing security patches, configuration-based vulnerabilities, and weak credentials. |
| 8 | Accidental Cloud Data Disclosure | Highlighting the challenges organizations face working in multi-cloud environments – making misconfigurations and finger trouble leading to unintentional data leaks. |
| 9 | Misconfiguration and Exploitation of Serverless and Container Workloads | In the spin up and tear down at scale environments for VMs and containers configuration there is a large attack surface at play that needs to be appropriately hardened. |
| 10 | Organized Crime/Hackers/Advanced Persistent Threats | Ransomware, SolarWinds, et al. The threat is real, and all organizations are in scope for such attacks. |
| 11 | Cloud Storage Data Exfiltration | Usual reputation damage, fines, and financial hit to an organization. |
Things have moved on since the 1980s when Pac-Man was ubiquitous, and the attack vectors were the fast-moving ghost gang characters. Blinky was one of them. Maybe you can remember the others? Internet search engine reports Pinky, Inky, and Clyde were the other ghosts in the Pac-Man gang. Full marks if you named all four! Reading the CSA publication reminded me how challenges have evolved from the on-premises environment where the threats were known, the data center was in close proximity, and the processes and procedures were documented and practiced. In the cloud, we have shared responsibility, and the dynamic as well as the threat models/attack vectors have changed.. Yes, the cloud offers the rigor and security diligence of the major cloud service providers but the need for careful allocation of system admins, setting least privilege, environmental hardening, due diligence, and compliance has not gone away.
Entrust CloudControl offers a compliance-centric, enterprise-grade solution for virtualized and containerized environments. It ensures DevSecOps and security administrators can establish, manage, and maintain a robust security posture across multiple clouds and on-prem environments. This prevents inadvertent or malicious misconfigurations leading to failed audits, service disruption, or breaches in security.
For those organizations migrating to multi-cloud and hybrid deployments, Entrust provides a complete suite of security solutions offering the right tools to protect against the top cloud computing threats outlined by the report. Entrust offers solutions that deliver across categories and enable enterprises to achieve their multi-cloud security strategy through a single vendor, securing the workload, creating trust in the environment in which it runs, and ensuring compliance with defined policy managed and maintained across all artifacts and across all deployment environments.



