
Bring Your Own Key to Microsoft Azure
Microsoft Azure Key Vault safeguards the critical cryptographic keys used in the cloud to keep your data secured.
A growing number of Microsoft services and vendor applications now consume Azure Key Vault and can benefit from BYOK.
Deployed around the world in Azure data centers, Entrust nShield hardware security modules (HSMs) safeguard and manage your keys in the cloud. To give you greater control, Entrust enables you to create, hold, and transfer your own keys for use with Azure Key Vault in the cloud or on your own premises.
Maintain full control of your sensitive cloud data and applications with nShield BYOK for Azure.
Watch our quick overview video to learn how it works.
Validation
An Entrust Warrant (Digital Certificate) Identifies Every nShield HSM
Use this hash value and the utility supplied to you by Microsoft to validate the warrant chain and key generation certificate, and assert that all the signing information was created inside a certified nShield HSM.
nCore Key Hash of nShield Warrant Signing Key (v0):
59178a47 de508c3f 291277ee 184f46c4 f1d9c639
Cloud
Control the critical keys securing your sensitive data in the cloud
As a cloud service, you can run Azure Key Vault on-demand without incremental IT infrastructure, and ensure that your data is protected across organizational boundaries. Azure Key Vault employs cryptography to deliver controlled access to and persistent protection for your data. Security depends on the level of protection given to the critical cryptographic key. Exposure of the cryptographic key can compromise your sensitive data. To ensure security, you can choose to protect your key within a robust boundary using Entrust nShield HSMs. nShield HSMs generate, safeguard, and manage the key independent of the software environment.
Enhanced security – nShield BYOK for Azure Key Vault
Entrust nShield has an unparalleled 20-year history in delivering data protection solutions to security-conscious businesses, governments, and technology vendors, including critical key management solutions for some of the most demanding security organizations in the world. As experts in the field, Entrust products and services provide high assurance security so customers can make effective use of cryptographic protection.
Entrust facilitates how you retain control of your keys. While keys can be generated in the cloud, for added assurance when using Azure Key Vault, keys are generated in your own nShield HSM (physically on-premises or as a service). Keys generated in this manner are securely shared with other nShield HSMs in the Azure cloud, but never leave the nShield HSM security boundary. Microsoft has used Entrust FIPS 140-2 Level 2 validated nShield HSMs to protect keys since the inception of Azure Key Vault.
What are HSMs?
HSMs are high-performance cryptographic devices designed to generate, safeguard and manage sensitive key material. Entrust nShield HSMs maintain your keys secure and usable only within the protected boundary. This enables you to maintain custody of your keys and visibility over their use.
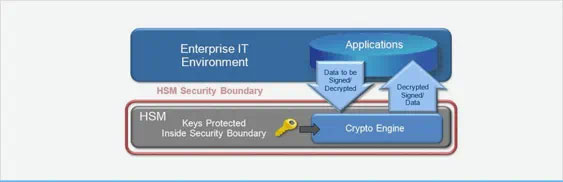
Why use Entrust nShield HSMs with Azure Key Vault?
Entrust nShield HSMs ensure that your keys are always under your control and never visible to Microsoft. The capability mitigates the perception that sensitive data maintained in the cloud is vulnerable.
Azure Key Vault offers you multiple levels of control. The Azure Key Vault keys become your tenant keys, and you can manage desired level of control versus cost and effort.
- By default, Azure Key Vault generates and manages the lifecycle of your tenant keys
- BYOK lets you generate tenant keys on your own physical or as a service Entrust nShield HSM
- Near-real time usage logs enhance security, allowing you to see exactly how and when your keys are being used
How it works
Entrust nShield HSMs create a locked cage protecting your tenant keys. You can cache the tenant keys securely from your on-site Entrust nShield HSM to an Entrust nShield HSM in Microsoft's Azure data center – without leaving the FIPS compliant security boundary created by the HSMs. The tenant keys are protected while in Microsoft's data centers – secured within a carefully designed cryptographic boundary that employs robust access control mechanisms to allow you to enforce separation of duties and ensure the keys are only used for their authorized purpose.
BYOK
BYOK for Azure Key Vault allows you to match the security properties of an on-premises environment. It enables you to generate your tenant keys on your on-premises or cloud-based nShield HSM per your IT policies, and transfer your tenant keys securely to the Azure cloud Entrust nShield HSM hosted by Microsoft.
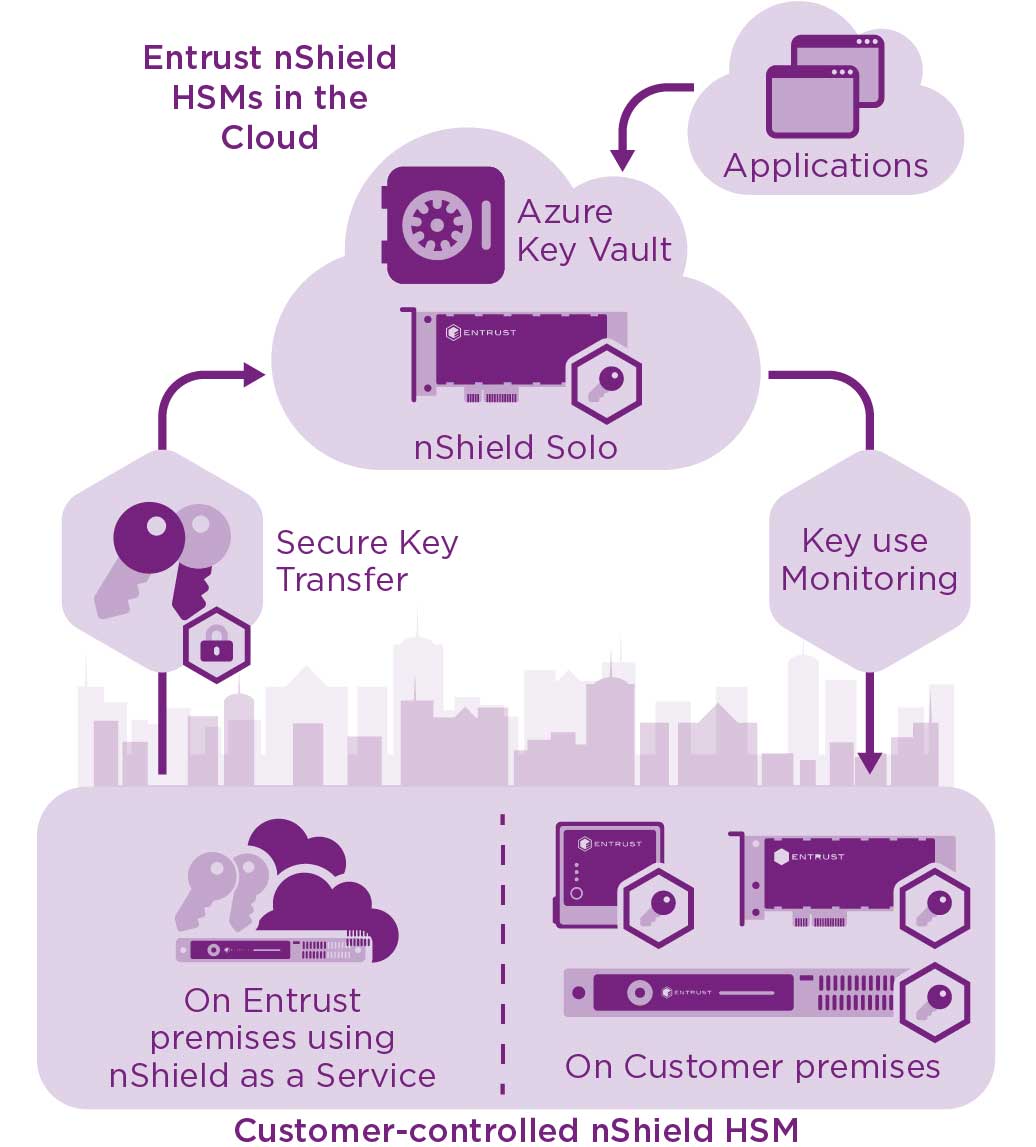
Hosted HSM validation
To ensure that the hosted HSM is an authorized Entrust nShield HSM, the Azure Key Vault with BYOK provides you a mechanism to validate its certificate. The capability, ONLY available with Entrust BYOK, enables you to verify that the key encryption key used to secure the upload of your tenant key was indeed generated in an Entrust nShield HSM.
On Premises
Safeguard and manage your Azure Information Protection (AIP) keys with high assurance hardware
While most content can be served by securely stored keys in Azure Key Vault, some sensitive content can never be shared or transmitted outside your own security perimeter. The security for this sensitive content needs to be physically on-premises only, with very limited access and sharing. To manage your most sensitive data within your own security perimeter, AIP offers hold your own key (HYOK) that is enabled by an on-premises physical component, with key management provided through nShield HSMs.
What are HSMs?
HSMs are high-performance cryptographic devices designed to generate, safeguard, and manage sensitive key material. nShield HSMs maintain your keys securely locked and usable only within the protected boundary. This enables you to maintain custody of your keys and visibility over their use.
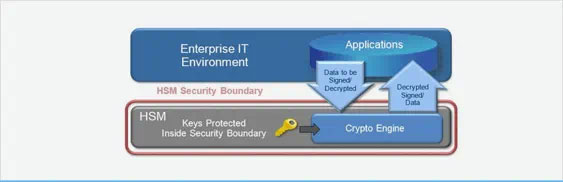
Why use nShield HSMs with AIP?
nShield HSMs provide hardened protection for the keys used by AIP to secure your critical data. nShield generate, safeguard, and manage the keys completely independent of the software environment.
How it works
nShield HSMs create a locked cage protecting your keys. The keys are protected within a carefully designed cryptographic boundary that employs robust access control mechanisms that let you enforce separation of duties to ensure the keys are only used for their authorized purpose. nShield use key management, storage, and redundancy features to guarantee your keys are always accessible when needed.
HYOK
nShield HSMs provide a hardware solution to protect your critical keys. nShield safeguards and manages the keys completely independently from the software environment, enabling you to hold your own key when access to your most sensitive content needs to remain physically on-premises only.
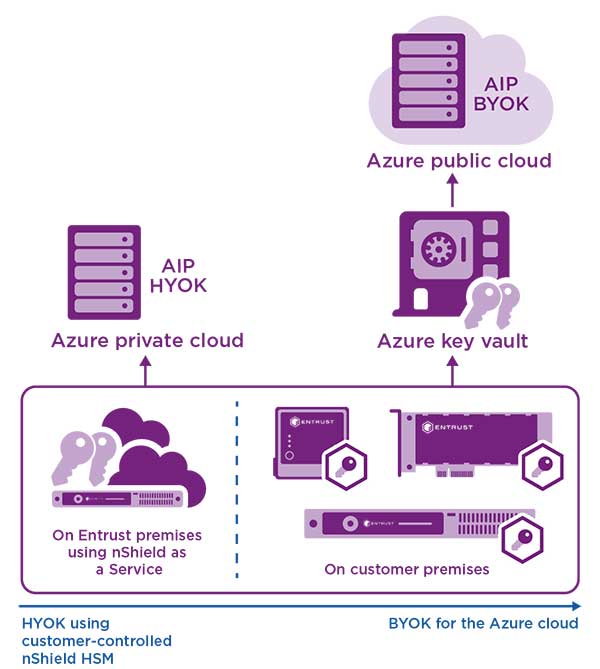
How to Buy
Entrust is the only HSM vendor that support both version of BYOK offered by Microsoft:
- nShield BYOK
- Microsoft BYOK
nShield BYOK offers strong attestation for key import and nShield HSM validation. Microsoft BYOK is supported by nShield Cloud Integration Option Pack.
What to buy to generate and protect your Microsoft Azure Key Vault keys using nShield BYOK
nShield Edge
If you need low volume, physical on-premises key generation, nShield Edge provides convenient USB-attached hardware security. Recommended integration uses two nShield Edge HSMs for full redundancy.
Learn more | nShield Edge Data Sheet
nShield Solo+ and Solo XC
For physical on-premises key generation, nShield Solo+ and Solo XC embedded PCIe card provides high-volume hardware-based key generation and management.
Learn more | nShield Solo Data Sheet
nShield Connect+ and Connect XC
If you need higher performance physical on-premises key generation, nShield Connect+ and Connect XC network attached appliance provides high-volume hardware-based key generation and management.
Learn more | nShield Connect Data Sheet
Entrust nShield as a Service
If you need higher performance on-premises key generation, you can also subscribe to your own nShield Connect HSM using nShield as a Service. Entrust nShield as a Service provides high-volume hardware-based key generation and management.
Learn more | nShield as a Service Data Sheet
What to buy to generate and protect your Microsoft Azure Key Vault keys using Microsoft BYOK
To generate and protect your keys using Microsoft BYOK, you will need one of the nShield HSM models listed above and the nShield Cloud Integration Option Pack.
Entrust Cloud Integration Option Pack
This option pack provides users of major cloud services the ability to generate keys in their own environment and export them for use in the cloud with confidence that their key has been generated securely using a strong entropy source, and that the long term storage of their key is protected by a FIPS-certified nShield HSM.
Together with these products, Entrust offers expert training, maintenance, and service programs to ensure the success of your integration now and in the future as your needs change.
BYOK Deployment Service Package
If you need low volume, on-premises key generation for Azure and are new to HSM technology, this customized packaged service includes an nShield Edge HSM, instruction, and installation. An Entrust consultant will teach you how to create and transfer your keys, and provide a detailed process, and checklist. Recommended integration with Azure uses two nShield Edge HSMs for full redundancy.
BYOK Deployment Service Package Data Sheet
Expert personnel will be happy to assist you with your purchase and advise you on training and maintenance options to fit your specific needs.
Contact your regional sales representative
Additional Resources
BYOK/HYOK to Azure Resources
Azure Information Protection with HYOK
Microsoft and Entrust deliver persistent information protection and key management option that puts you in control in the cloud
