Once mainly a topic for math geeks and techies, encryption is now widely recognized as the technology that protects your information from exposure if it’s captured in a data breach, or conversely blocks your access to it if you fall victim to a ransomware attack. It’s a fundamental part of an enterprise access control strategy, and the last line of defense when other protections break down, yet many organizations struggle with its fundamentals.
Entrust and I have the great fortune of partnering with Dr. Larry Ponemon and the team at the Ponemon Institute on THE most comprehensive study of encryption in our industry. With responses from over 6400 IT professionals in 17 countries/regions around the world, the 2020 Global Encryption Trends Study provides a very revealing look at the evolution of encryption use and, importantly, information that readers can use to benchmark their encryption and data protection strategies.
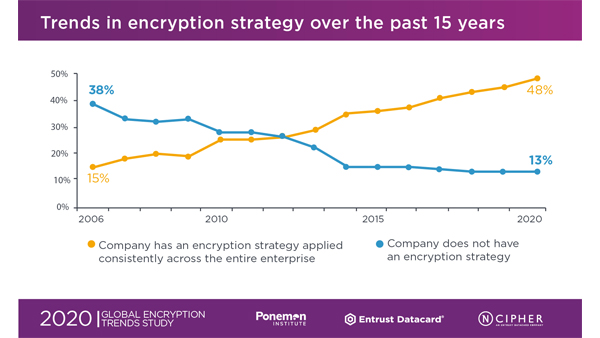
Key takeaways
Some of the most interesting takeaways from the study aren’t just from the current year; they come from looking at multi-year trends. Just four short years ago, the dominant driver for deploying encryption was regulatory compliance. Check the box and (hopefully) move on, auditor willing. But today? For the first time in the 15-year history of this study, protection of customer information is the top reason for encryption. Right on its heels? Protection of intellectual property. So encryption has clearly taken center stage as businesses protect what is most important to them, and the health, reputation, and sustainability of their business.
So that might sound easy enough. Identify your most sensitive information and encrypt it. But it turns out that identifying it isn’t nearly the hardest problem. That prize goes to actually DISCOVERING where all that sensitive data actually resides. In today’s mobile and cloud-enabled world, data proliferation is at an all-time high. Nothing defeats an enterprise encryption strategy faster than if you encrypt data in one location, but leave it exposed in others. And everyone needs to be thinking right now about how new remote work situations may be creating new sensitive data exposures. Attackers will target the lowest hanging fruit every time.
Encryption challenges
The other Achilles heel of encryption is key management. Our study shows that with the rise of encryption use, across more and more individual products and technologies, the difficulties of managing the associated keys become exacerbated. Over a third of respondents rated the “pain” of key management as a 9 or 10 on a scale of 1 (minimal) to 10 (severe)! Managing keys properly from creation to destruction is quite a bit more complicated than many people realize – and our study reveals that both operational and technological issues are contributors.
But I don’t want to paint doom and gloom. The study also reveals that hardware security modules (HSMs) are an increasingly important tool to fortify encryption strategies and enforce key management policies – and their usage rose to record levels in 2020. Also, enterprises are succeeding in employing encryption well beyond the mature use cases like backups/archives, databases, and laptop hard drives. Encryption with public cloud services, containers, and IoT devices and platforms are all on the rise, indicating that digital transformation is being bolstered by a healthy dose of data protection.
The future of encryption
So what’s next? We took our first look this year at whether new encryption technologies like multi-party computation (MPC), homomorphic encryption, or quantum resistant algorithms are ready to make an impact. The consensus was that MPC is the closest, but even that is a good five years from making an impact. So for now, it’s about sticking to the fundamentals and investing in protecting what matters the most.
The study is full of additional detail, including some revealing splits about encryption trends by country and by industry. To download the 2020 Global Encryption Trends Study, click here. Questions or comments? You can find me on Twitter @johnrgrimm, or follow Entrust on Twitter, LinkedIn, and Facebook.


