The Cloud Boom…
Cloud adoption has been astronomical. Organizations are pursuing cloud because of the multidimensional value of these services – such as agility, scalability, cost benefits and innovation. According to a forecast from Gartner, the market for cloud services will grow 18% this year, to $246.8 billion in total worldwide revenue from $209.2 billion. The cloud vendors that are leading this charge are Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP). Along with a desire for the business benefits the cloud provides, the proliferation of data collected from the IoT, AI, machine learning and other big data apps (which require tremendous computing power) will further stoke growth.
As organizations adopt cloud services, they may be surprised to learn they need not abdicate control over their data security to their cloud vendor. Ultimately, this is a good thing: companies that face regulatory requirements need better than ‘default’ security. Generally, they require more control and higher assurance levels than the out-of-the-box key management provided by their cloud vendor.
Most cloud providers offer encryption for data at rest, both to protect files and archives from unwanted inspection by authorized infrastructure managers, and in case of data leaks from the cloud service. In many ways encryption is another commodity feature of the cloud service you pay for. However, it is only effective when encryption keys are properly protected – and therein lies the rub.
…and How to Avoid the Cloud Bust
Unfortunately, controlling encryption keys — and thus your data — while adopting cloud services is one of the more difficult puzzles in moving to the cloud. According our 2017 Ponemon Global Encryption Trends Report, keys for external cloud or hosted services rated as the most painful to manage across a comprehensive list of key types.
Fortunately, there are options (the need for options was most recently illustrated by the OneLogin data beach, during which a hacker was able to access a set of OneLogin’s AWS keys. According to reports, OneLogin did not have full control over its keys at the time. Following the breach, the company stated, “The threat actor was able to access database tables that contain information about users, apps and various types of keys. While we encrypt certain sensitive data at rest, at this time we cannot rule out the possibility that the threat actor also obtained the ability to decrypt data”).
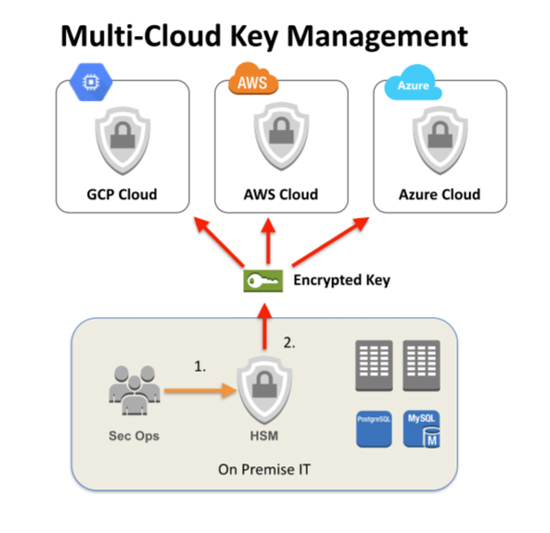
Entrust, for example, provides “bring your own key” (BYOK) solutions to cloud applications, for users of AWS, GCP, and Microsoft Azure. Our nShield high-assurance HSMs allow organizations to benefit from the flexibility and economy of cloud services while strengthening the security of key management practices and gaining greater control of keys.
Retaining autonomy over encryption reinforces application and cloud services controls, because it empowers organizations to preserve their own data usage policies. Enforcing data usage policies also provides auditors comfort – which is a win-win for all.
Interested in learning more? We recommend you download this (free!) Securosis white paper about multi-cloud key management, which you can also find on the Securosis website. In the piece, you will discover why firms look for greater security and consistency with key management, the different approaches available, and how to select the right strategy from the many possible combinations.
Have comments or questions? Message me @vikramesh or find me on LinkedIn here.


